THM - Git Happens
1 Summary
- Enumeration with nmap
- Subdirectory Enumeration with Nikto
- Git Repository Manipulation with GitTools
2 Background Information
The Git Happens room, as the name suggests, focuses on Git. Thus, some basic knowledege about Git, as well as some familiarity with Git’s functionality, would greatly help in solving this challenge.
Some quick and great resources to read through and practice the main concepts are:
- Git Tutorial from w3schools.
- Introduction to GitHub from GitHub’s official documentation.
In brief, Git is the most popular version control system today, which can be thought as a timeline management utility. The core building blocks of a Git project are its commits, which are essentially snapshots along the project’s timeline.
As GitHub’s documentation perfectly explains:
Over time, commits should tell a story of the history of your repository and how it came to be the way that it currently is.
Keep this last line in mind, as it’s extremely relevant to this room!
3 CTF Process
3.1 Port-scanning with nmap
As usual, let’s start with an nmap port-scanning:
1
nmap -sV -T4 -open <taget-ip>
-sV Attempts to determine the version of the service running on port.
-T4 Aggressive (4) speeds scans; assumes you are on a reasonably fast and reliable network.
-open Show only open (or possibly open) ports.
<target-ip> The target machine’s IP.
Not much there, just an nginx web server on port 80. Vising the site via our browser, we see a login page:
3.2 Subdirectory enumeration with Nikto
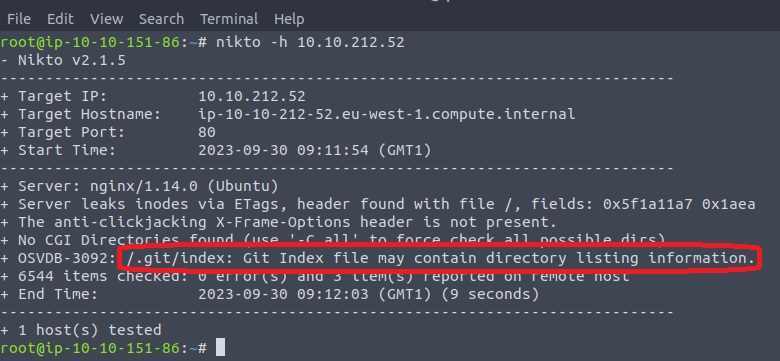
We can use various tools for searching subdirectories, such as gobuster and Nikto, but let’s go with Nikto this time:
It looks like Nikto found a public-facing git repository: /.git !
3.3 Git Repositories and GitTools
We can download the whole repository on our machine using GitTools. We just need to:
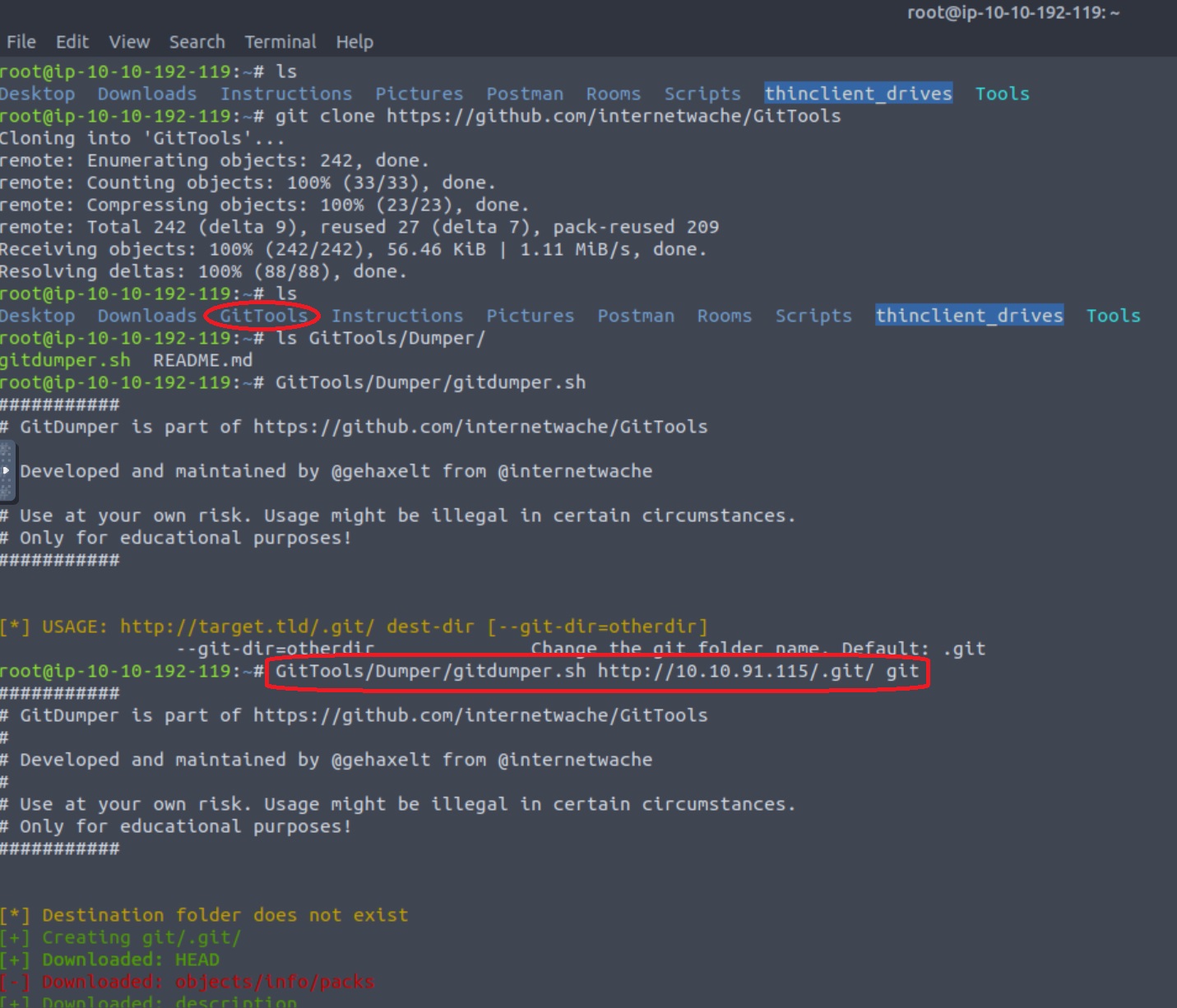
- Go to the desired directory and clone GitTools with
git clone https://github.com/internetwache/GitTools. - Use the
gitdumber.shscript passing the target repository and the destination directory that we want to clone it in:gitdumber.sh http://<target-ip>/.git <dest-dir>.
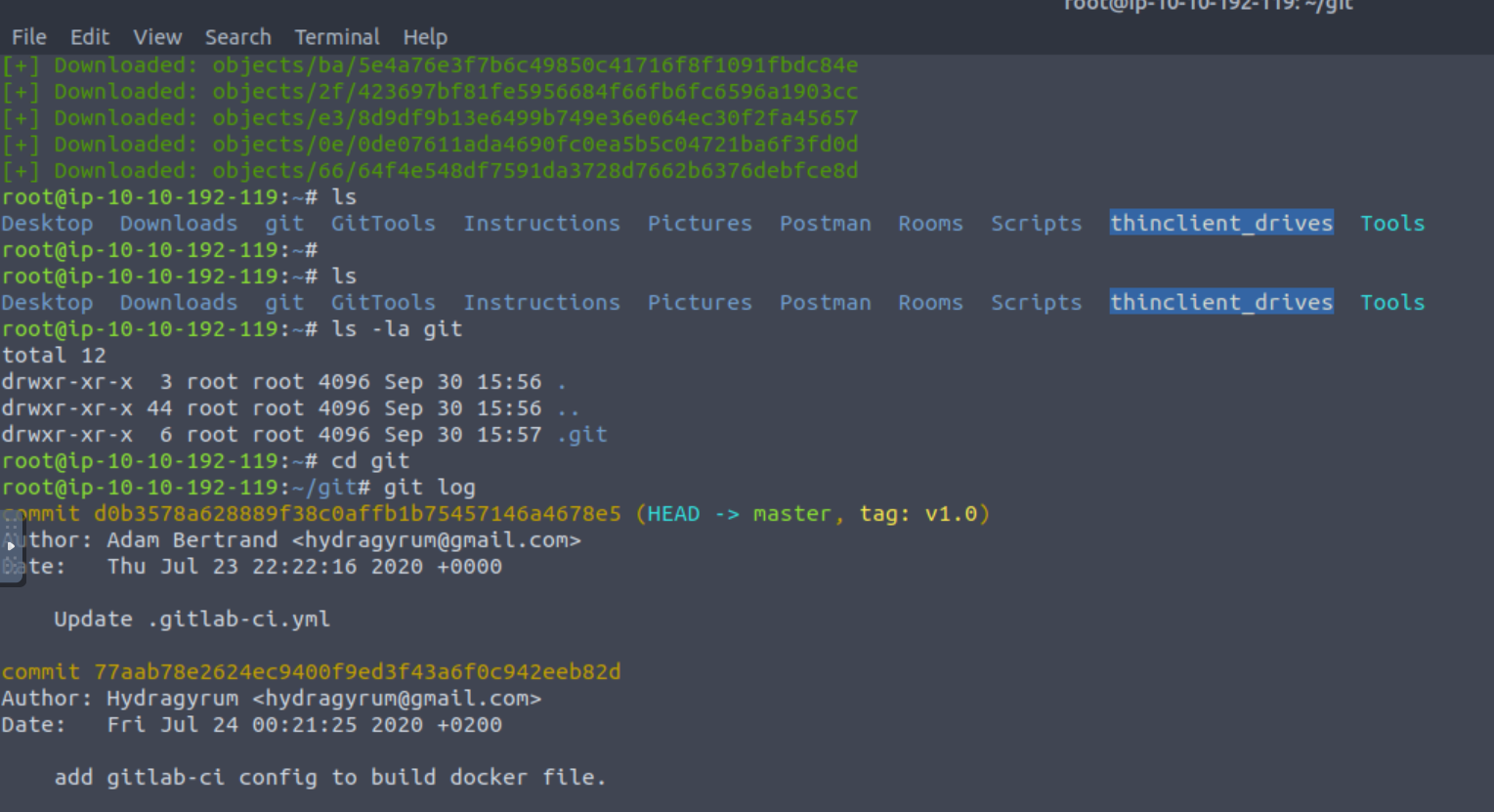
By moving within the directory, in this case git, we can interact as it was our own. For instance, we can see its logs using git log:
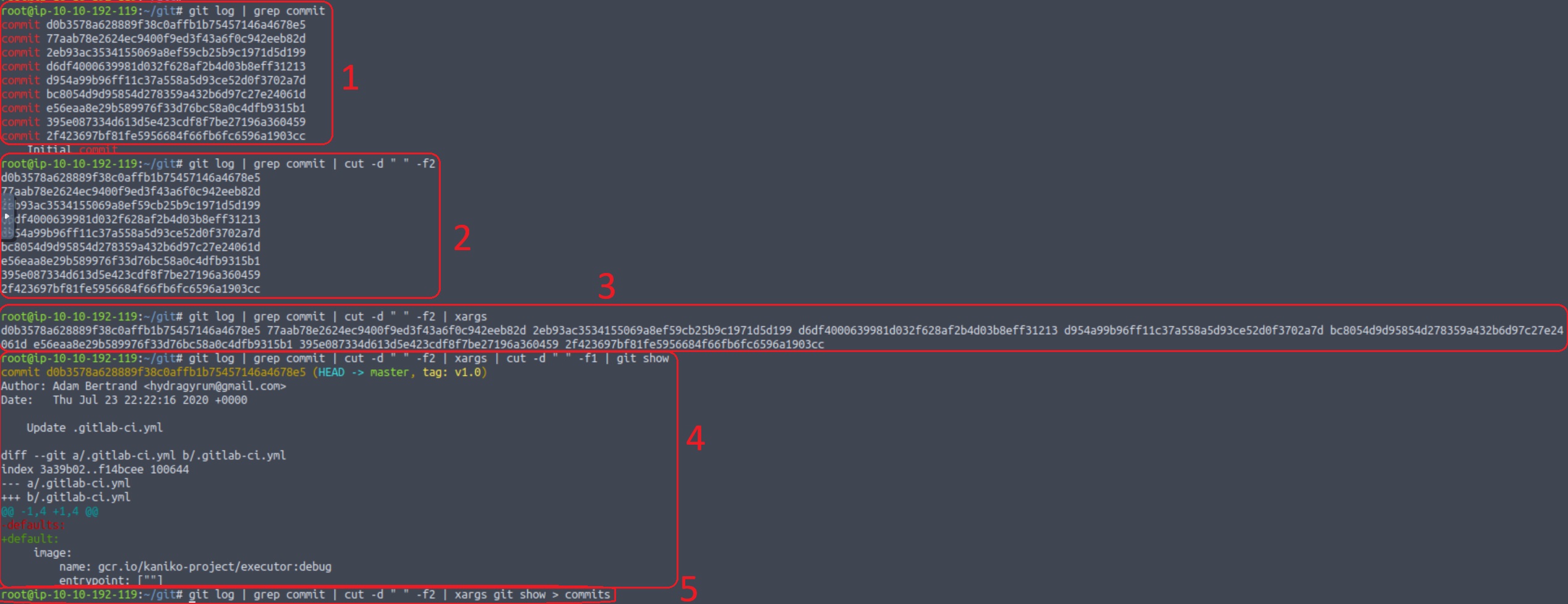
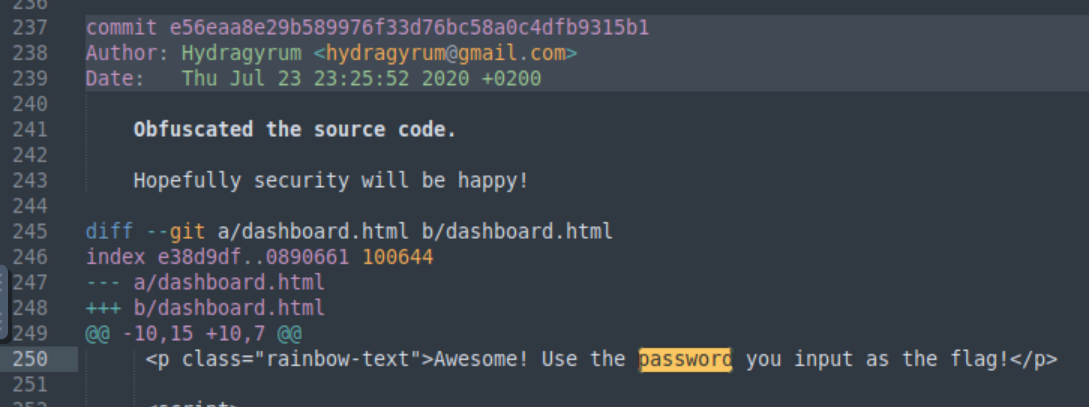
We are interested mostly on the commits included within the log, and in particularly the earlier ones, when the site was on its initial stages. We can achieve this by chaining commands using the pipe operator |, which passes a command’s output as the following command’s input.
git log | grep commitRead logs and show only the lines which include the word “commit”.git log | grep commit | cut -d " " -f2Separate each line using space as the delimiter, and keep only the second field.git log | grep commit | cut -d " " -f2 | xargsConverts standard input into arguments for a command.git log | grep commit | cut -d " " -f2 | xargs | cut -d " " -f1 | git showSeparate arguments using space as the delimiter, keep only the first field, and show the corresponding commit.git log | grep commit | cut -d " " -f2 | xargs git show > commitsUse the arguments generated as an input togit show, and write them to thecommitsfile.
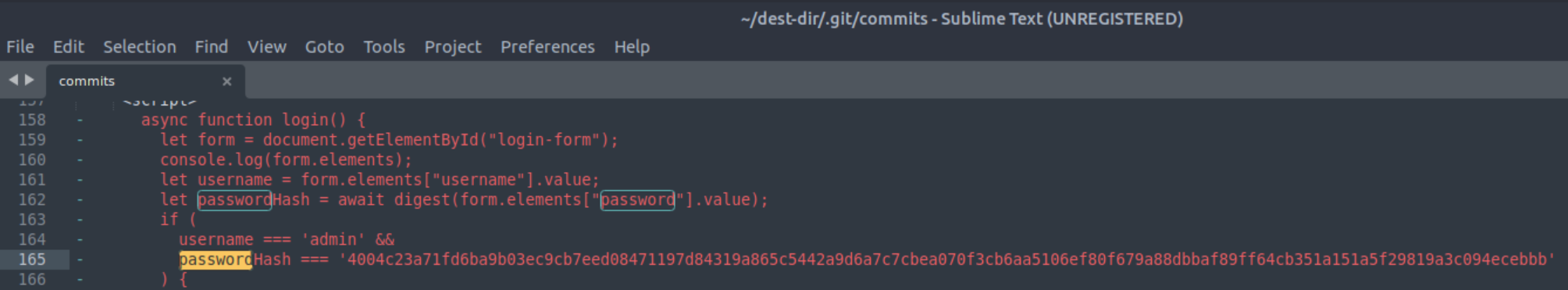
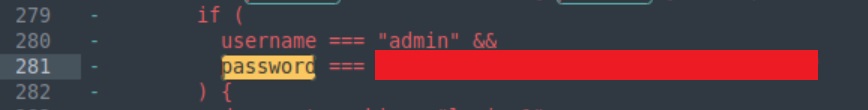
Finally, we can use subl commits to open the file we just created with the sublime editor, and search for the word “password” by pressing CTRL+F. We can see a discussion regarding the password’s security all the way from its creation in plaintext format.
The plaintext password is our first and only 🚩 🥂 !