PicoCTF - Some Assembly Required 1
Visiting the site we encounter just an input box:
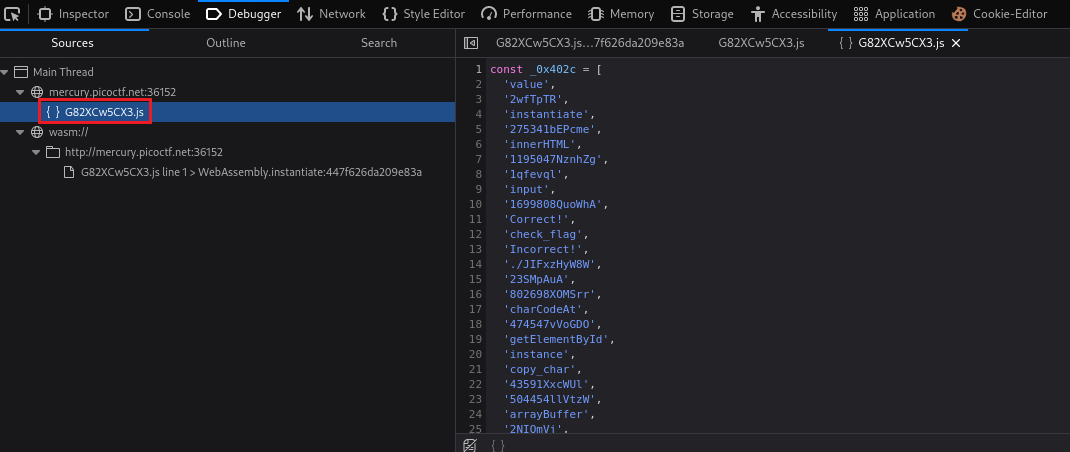
Inspecting the page we notice two files:
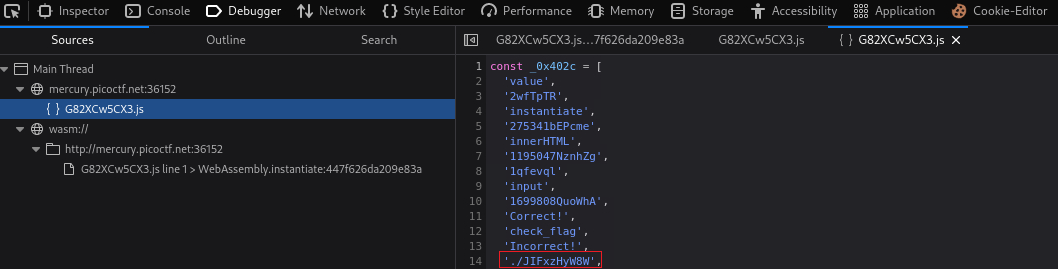
The first one looks like obfuscated JS code:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65
const _0x402c = [ 'value', '2wfTpTR', 'instantiate', '275341bEPcme', 'innerHTML', '1195047NznhZg', '1qfevql', 'input', '1699808QuoWhA', 'Correct!', 'check_flag', 'Incorrect!', './JIFxzHyW8W', '23SMpAuA', '802698XOMSrr', 'charCodeAt', '474547vVoGDO', 'getElementById', 'instance', 'copy_char', '43591XxcWUl', '504454llVtzW', 'arrayBuffer', '2NIQmVj', 'result' ]; const _0x4e0e = function (_0x553839, _0x53c021) { _0x553839 = _0x553839 - 470; let _0x402c6f = _0x402c[_0x553839]; return _0x402c6f; }; ( function (_0x76dd13, _0x3dfcae) { const _0x371ac6 = _0x4e0e; while (!![]) { try { const _0x478583 = - parseInt(_0x371ac6(491)) + parseInt(_0x371ac6(493)) + - parseInt(_0x371ac6(475)) * - parseInt(_0x371ac6(473)) + - parseInt(_0x371ac6(482)) * - parseInt(_0x371ac6(483)) + - parseInt(_0x371ac6(478)) * parseInt(_0x371ac6(480)) + parseInt(_0x371ac6(472)) * parseInt(_0x371ac6(490)) + - parseInt(_0x371ac6(485)); if (_0x478583 === _0x3dfcae) break; else _0x76dd13['push'](_0x76dd13['shift']()); } catch (_0x41d31a) { _0x76dd13['push'](_0x76dd13['shift']()); } } }(_0x402c, 627907) ); let exports; ( async() => { const _0x48c3be = _0x4e0e; let _0x5f0229 = await fetch(_0x48c3be(489)), _0x1d99e9 = await WebAssembly[_0x48c3be(479)](await _0x5f0229[_0x48c3be(474)]()), _0x1f8628 = _0x1d99e9[_0x48c3be(470)]; exports = _0x1f8628['exports']; } ) (); function onButtonPress() { const _0xa80748 = _0x4e0e; let _0x3761f8 = document['getElementById'](_0xa80748(484)) [_0xa80748(477)]; for (let _0x16c626 = 0; _0x16c626 < _0x3761f8['length']; _0x16c626++) { exports[_0xa80748(471)](_0x3761f8[_0xa80748(492)](_0x16c626), _0x16c626); } exports['copy_char'](0, _0x3761f8['length']), exports[_0xa80748(487)]() == 1 ? document[_0xa80748(494)](_0xa80748(476)) [_0xa80748(481)] = _0xa80748(486) : document[_0xa80748(494)](_0xa80748(476)) [_0xa80748(481)] = _0xa80748(488); }
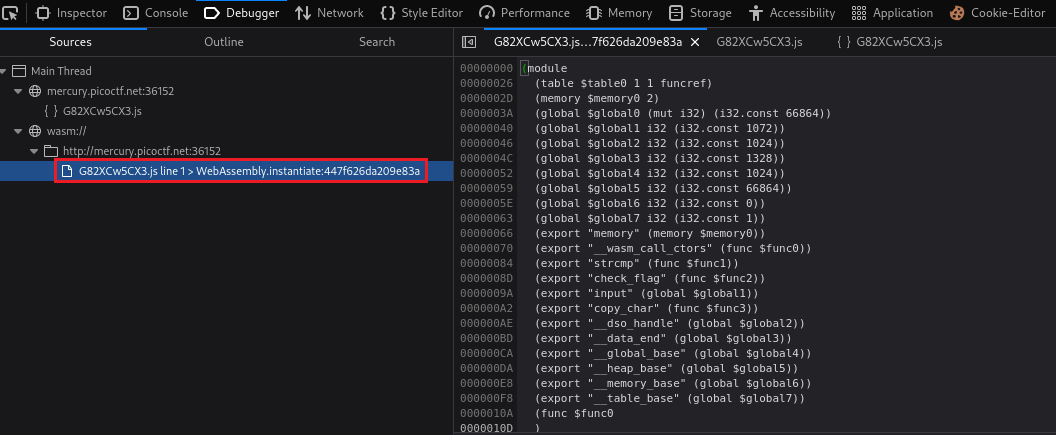
If we notice closely, there is something that looks like a path:
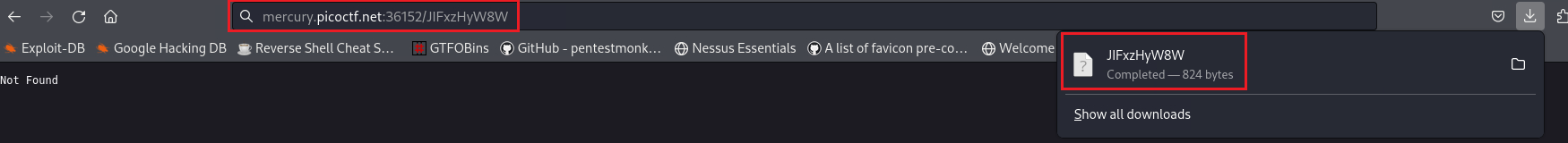
If we visit the above directory, a file starts downloading:
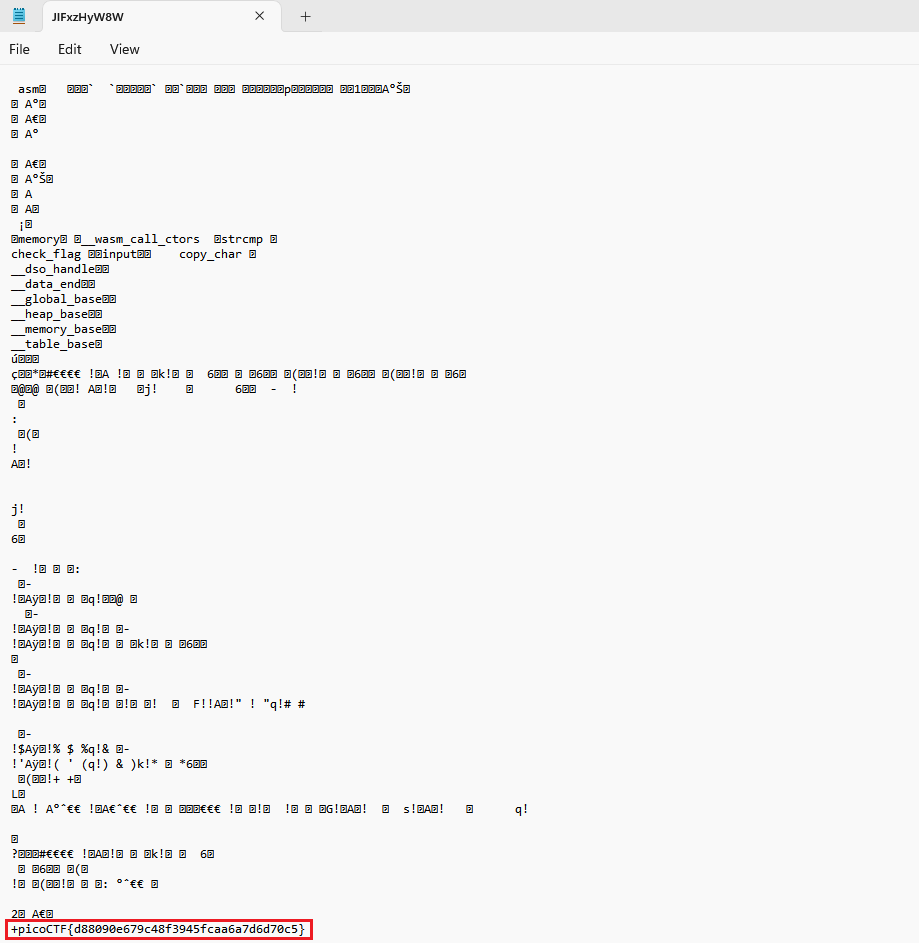
Opening and scrolling at the end of the file we can find the flag:
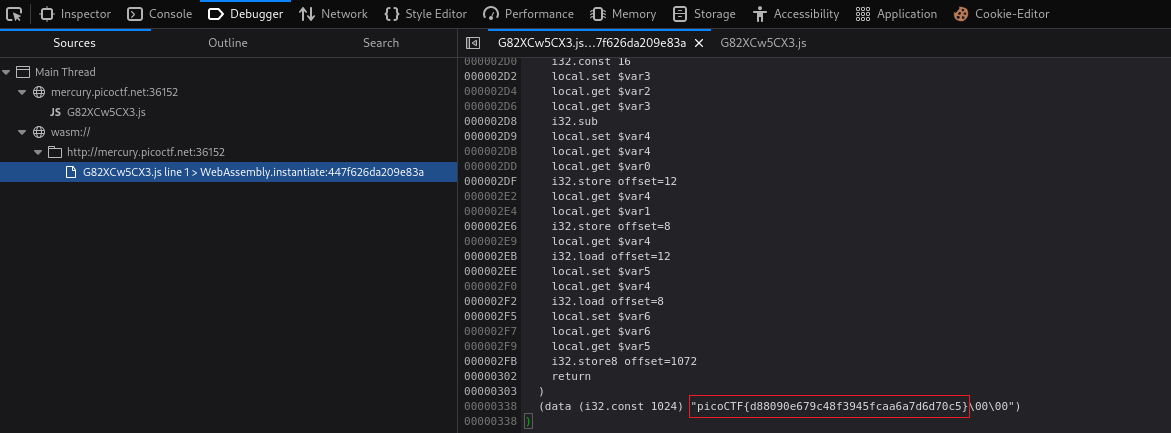
The second file looks like assembly code, and is inside the
wasmdirectory. So, let’s find out what that is:WebAssembly is a type of code that can be run in modern web browsers — it is a low-level assembly-like language with a compact binary format that runs with near-native performance and provides languages such as C/C++, C# and Rust with a compilation target so that they can run on the web. It is also designed to run alongside JavaScript, allowing both to work together.
The wasm script is quite large, but we can find the flag at the end of it: