PicoCTF - More Cookies
The homepage seems simple enough:
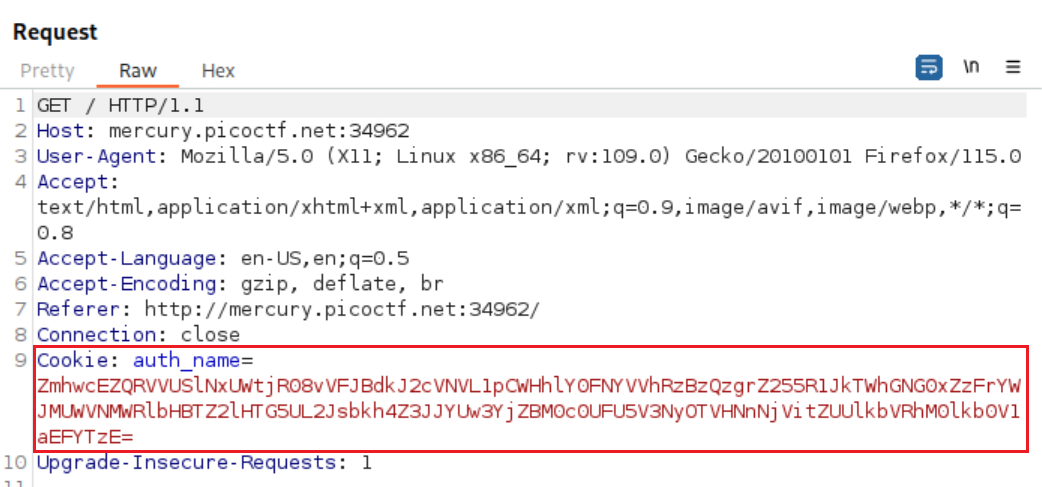
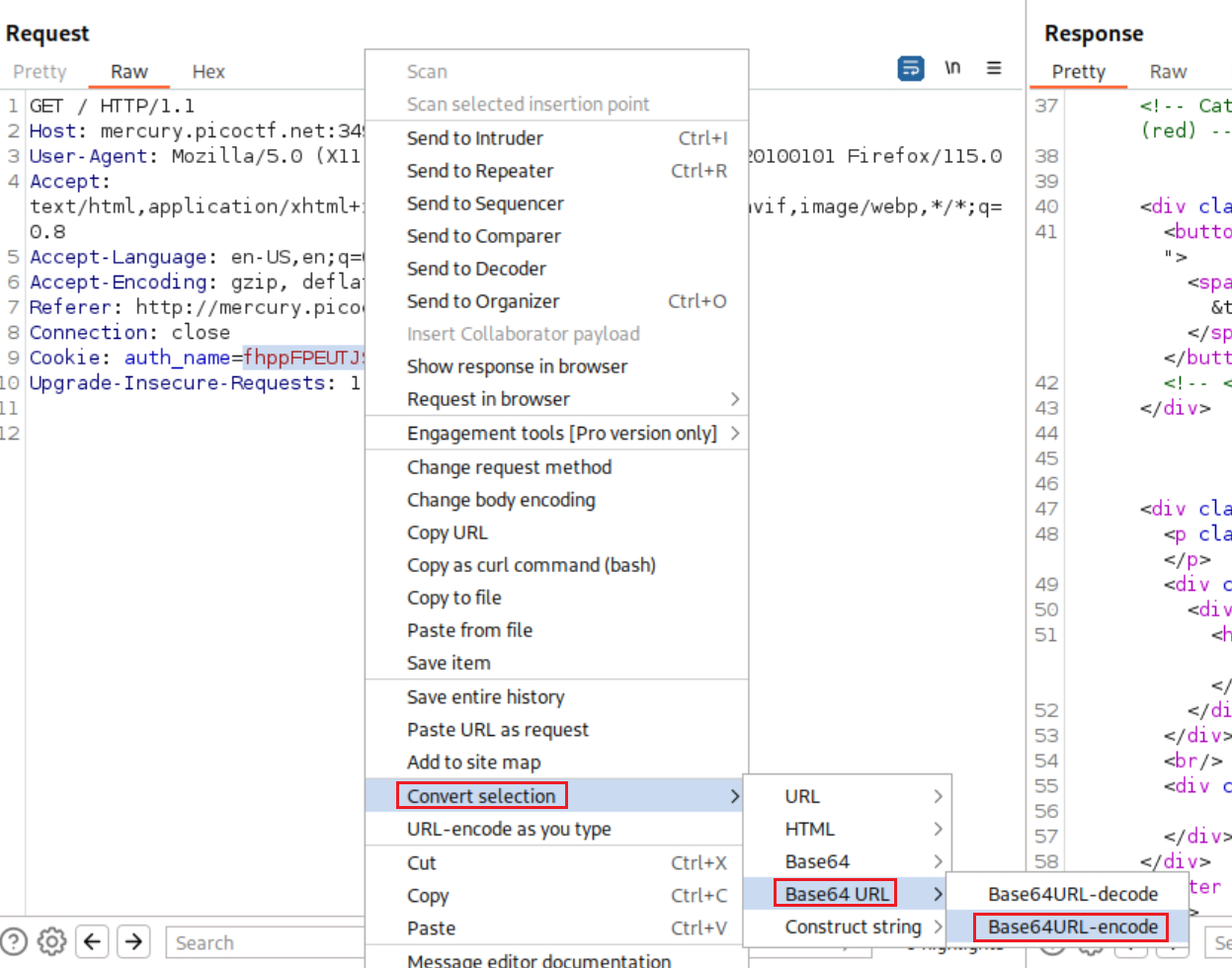
By intercepting and inspecting the request with Burp, we see that there is a cookie called
auth_namewhich seems to be Base64 encoded:Decoding the cookie produces a series of strings seperated by a
/:Trying splitting the strings, base64 encoding them, and sending a new request with each one does not produce any interesting results:
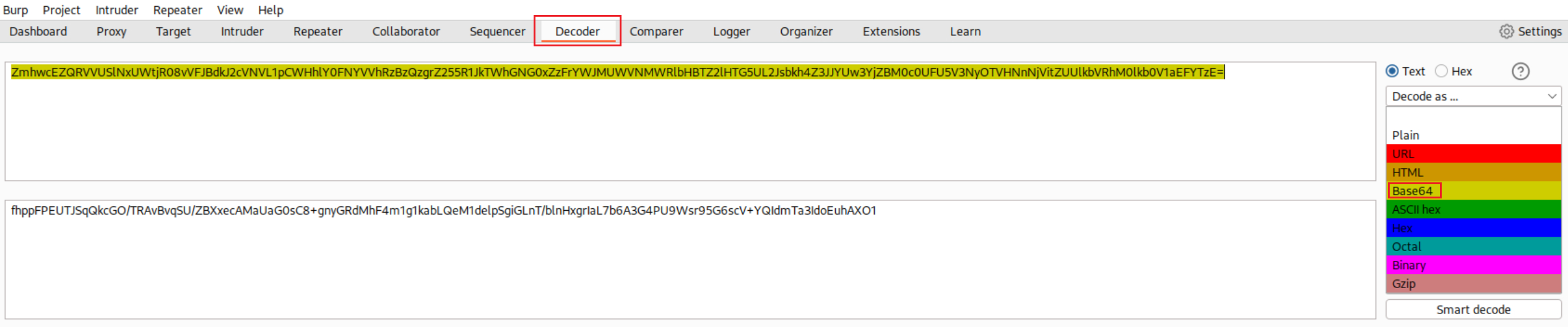
If we decode it using Base64 a second time we get this:
1 2 3
$ echo "ZmhwcEZQRVVUSlNxUWtjR08vVFJBdkJ2cVNVL1pCWHhlY0FNYVVhRzBzQzgrZ255R1JkTWhGNG0xZzFrYWJMUWVNMWRlbHBTZ2lHTG5UL2Jsbkh4Z3JJYUw3YjZBM0c0UFU5V3NyOTVHNnNjVitZUUlkbVRhM0lkb0V1aEFYTzE=" | base64 -d | base64 -d ~⸮i�L��BG;���o�%?d�y� di��x�]zZR�!��?ۖq�⸮/��q�=OV��yW�!ٓkr�K�s�
It’s time to look up the first hint which is just a Wikipedia article, but after searching a bit more about it, I found this brilliant article about Homomorphic Encryption:
Homomorphic encryption is a cryptographic method that allows mathematical operations on data to be carried out on cipher text, instead of on the actual data itself. The cipher text is an encrypted version of the input data (also called plain text). It is operated on and then decrypted to obtain the desired output. The critical property of homomorphic encryption is that the same output should be obtained from decrypting the operated cipher text as from simply operating on the initial plain text.
As always, when encountering complex topics for the first time reading led to even more reading. After going through some walkthroughs like this, this, and this there are some things to note down:
Some letters are capitalized in the challenge’s description which is a common way for authors to pass hints:
CBC stands for Cipher Block Chaining which is a mode of operation for a block cipher and its key characteristic is that it uses a chaining process that causes the decrytpion of a block of ciphertext to depend on all the preceding ciphertext blocks.
Essentially, there is a single bit that determines if the user is an admin. Maybe there is a parameter like
admin=0and if we change the correct bit then we can setadmin=1. However, the position of this bit is unknown, so we can try every position until we get the flag.
So at least we now know (kind of) what we are dealing with. After searching how we can break CBC, we learned that there is a common attack called the CBC Byte Flipping Attack and there is even a Python-written PoC for it.
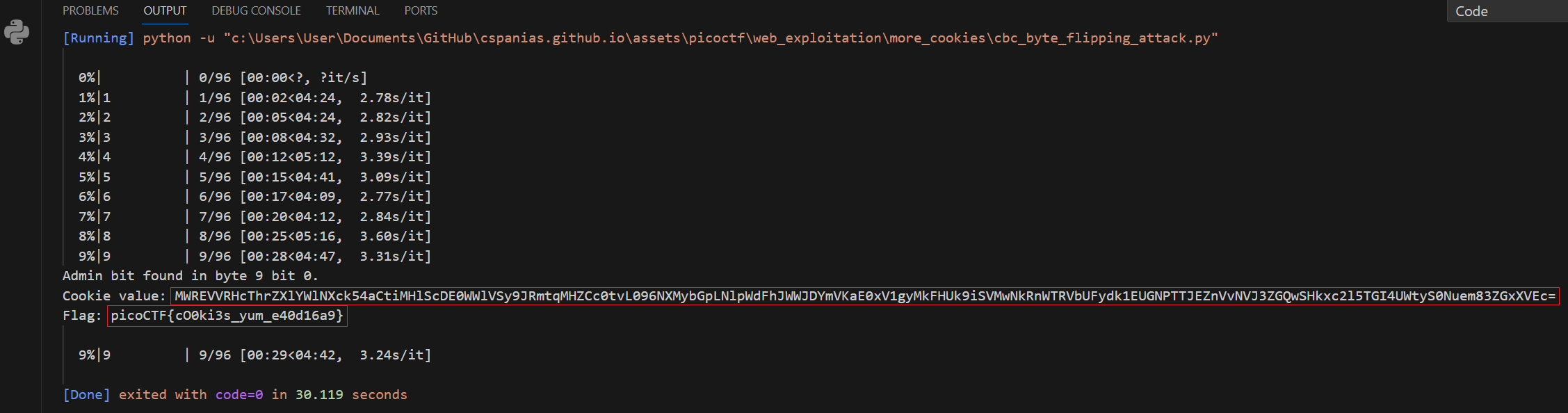
Instead of reinventing the wheel, we can minimally modify HHousen’s code to perform the CBC Byte Flipping attack and get the flag as well as the encoded cookie value so we can then pass it to the request if we like to:
You can find the modified code here.
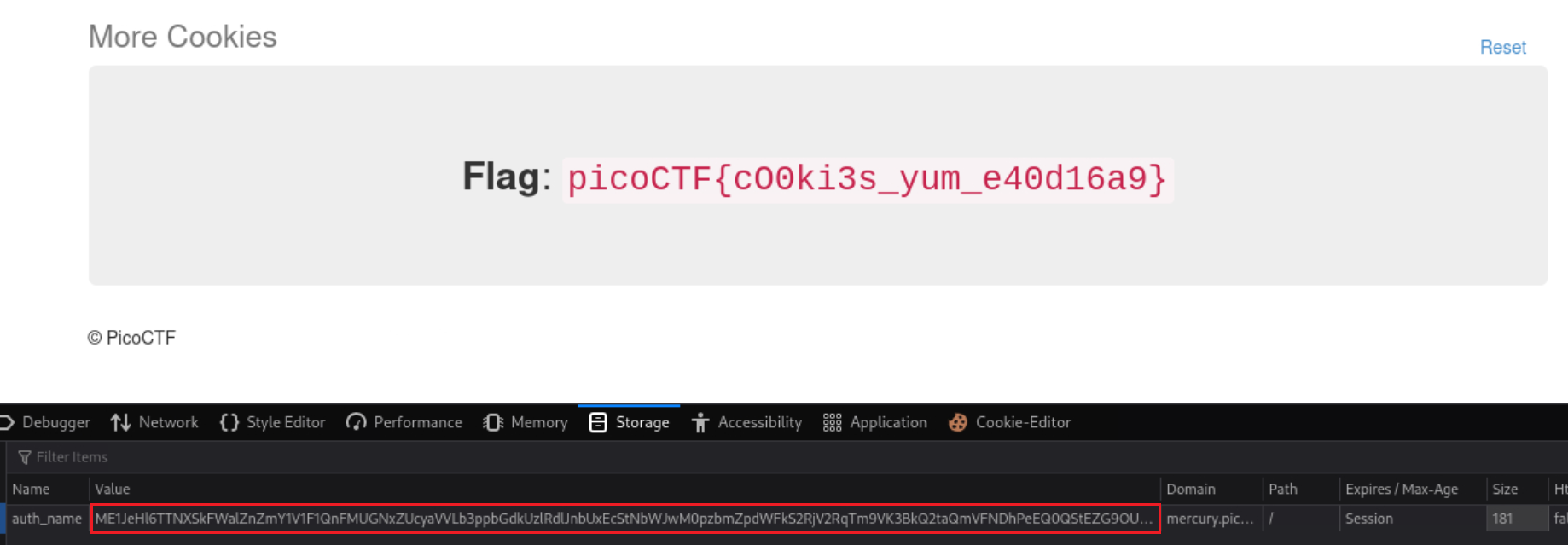
We can replace the cookie’s value in our browser, refresh the page, and confirm that it is working: