PicoCTF - Findme
Description: Help us test the form by submiting the username as
testand password astest! Additional details will be available after launching your challenge instance.
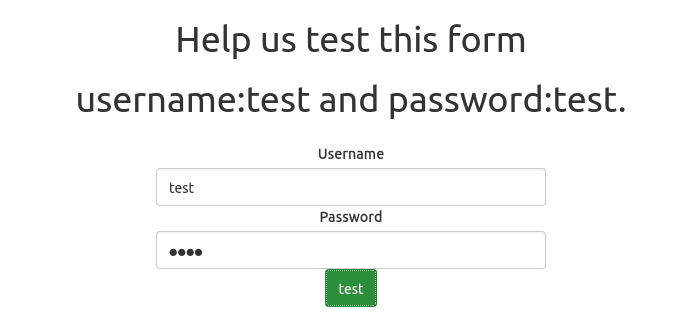
Upon launching an instance we face a login form. When we use
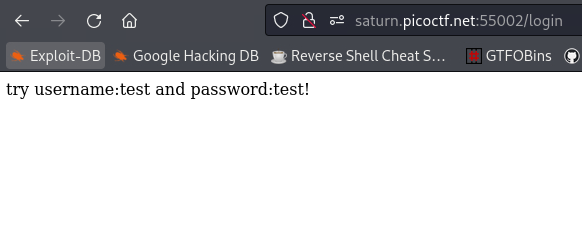
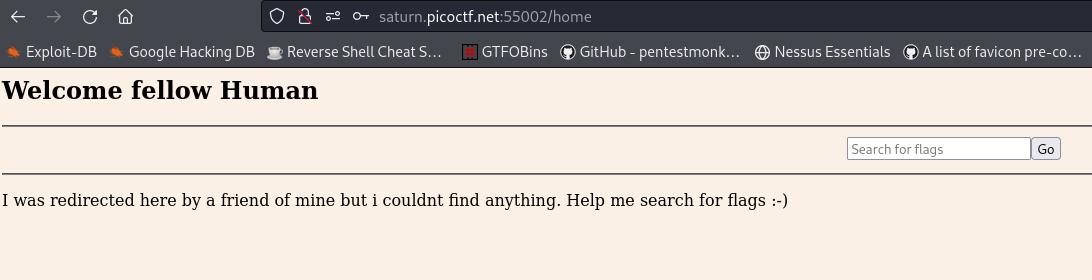
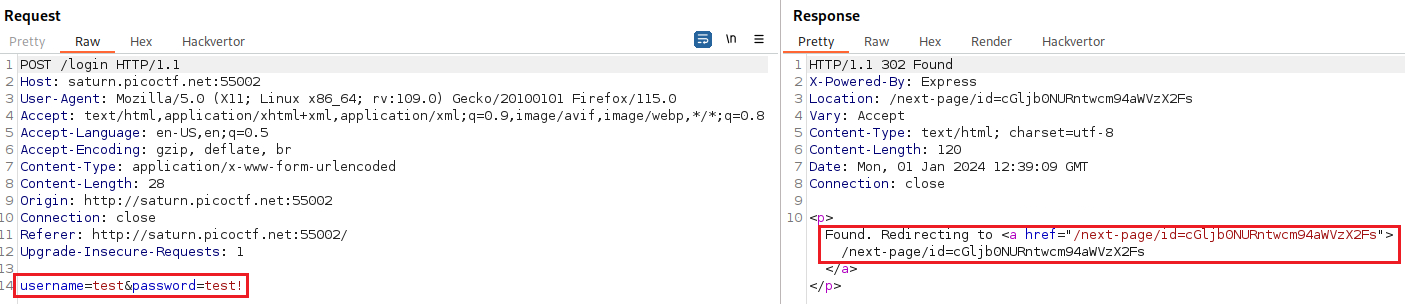
test:testas credentials, it instructs to usetest:test!instead:When we login with
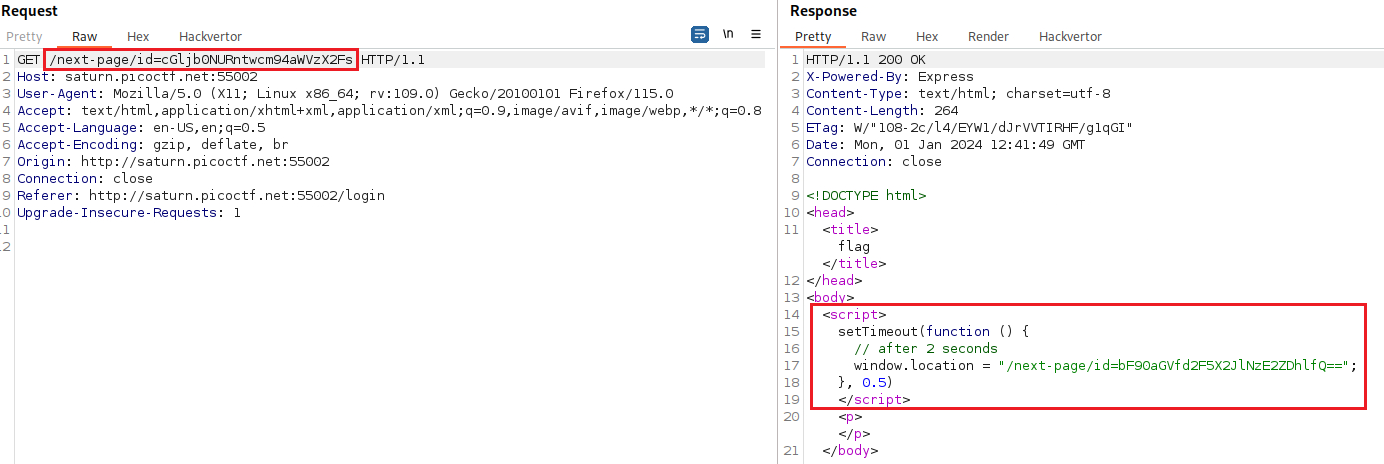
test:test!as our creds, we get into the/homedirectory. Intercepting the traffic with Bup the request looks like this:It seems like we get redirected to another page, more specifically
/next-page/id=cGljb0NURntwcm94aWVzX2Fs. Landing there, we get redirected again to/next-page/id=bF90aGVfd2F5X2JlNzE2ZDhlfQ==:The latter seems like a base64 encoding string, so we can try to decode it:
1 2 3
# decoding the base64 encoded string $ echo "bF90aGVfd2F5X2JlNzE2ZDhlfQ==" | base64 -d l_the_way_be716d8e}
This seems to be the second part of the flag, so the first redirection might also be encoded in base64:
1 2 3
# decoding the base64 encoded string $ echo "cGljb0NURntwcm94aWVzX2Fs" | base64 -d picoCTF{proxies_al
We can join the two strings and submit our whole flag:
1 2
$ echo "cGljb0NURntwcm94aWVzX2FsbF90aGVfd2F5X2JlNzE2ZDhlfQ==" | base64 -d picoCTF{proxies_all_the_way_be716d8e}