8. Second-order SQLi
Second-order SQLi
First-order SQLi occurs when the app processes user input from an HTTP request and incorporates the input into a SQL query in an unsafe way.
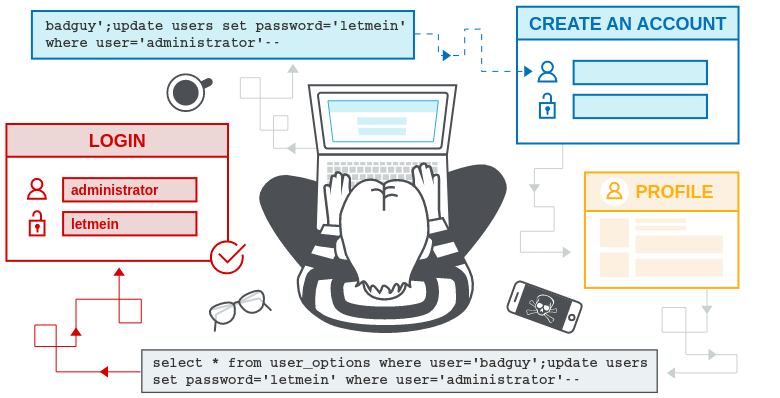
Second-order SQLi occurs when the app takes user input from an HTTP request and stores it for future use. This is usually done by placing the input into a database, but no vulnerability occurs at the point where the data is stored. Later, when handling a different HTTP request, the app retrieves the stored data and incorporates it into a SQL query in an unsafe way.
For this reason, second-order SQLi is also known as stored SQLi.
Stored SQLi often occurs in situations where developers are aware of SQLi vulnerabilities, and so safely handle the initial placement of the input into the database. When the data is later processed, it is deemed to be safe, since it was previously placed into the database safely. At this point, the data is handled in an unsafe way, because the developer wrongly deems it to be trusted.