HTB - Spookifier
Overview
| Challenge | Spookifier |
| Rank | Very easy |
| Category | Web |
Challenge description: There’s a new trend of an application that generates a spooky name for you. Users of that application later discovered that their real names were also magically changed, causing havoc in their life. Could you help bring down this application?
The home page includes input box which takes our name:
After examining the challenge’s files, we can see that this app is using the Mako template engine:
1 2 3 4 5 6 7 8 9 10 11 12
# Dockerfile content $ cat Dockerfile FROM python:3.8-alpine RUN apk add --no-cache --update supervisor gcc # Upgrade pip RUN python -m pip install --upgrade pip # Install dependencies RUN pip install Flask==2.0.0 mako flask_mako Werkzeug==2.0.0 <SNIP>
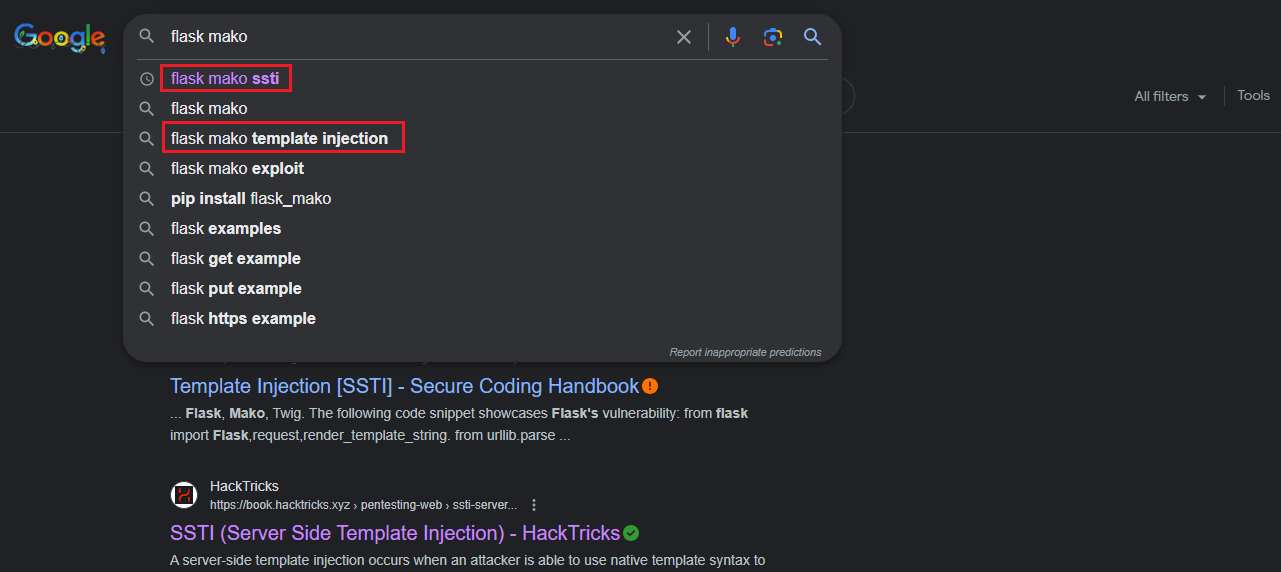
After searching for “flask mako” on Google, the first and third results were about Server Side Template Injection (SSTI):
SSTI is when an attacker is able to use native template syntax to inject a malicious payload into a template, which is then executed server-side.
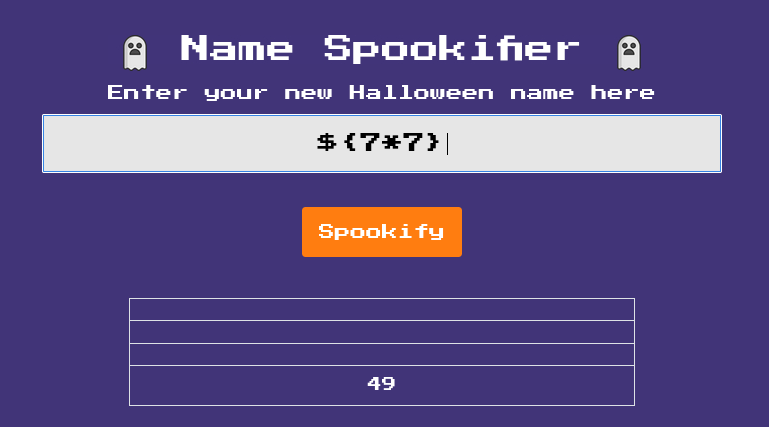
There is a list of payloads on Hacktricks for detecting SSTI, and upon trying the
${7*7}we can see that is works:PayloadsAllTheThings also has a
Python Makosection with specific payloads for that template:
1
cd ../;cat flag.txt