HTB - Find the easy pass
Overview
| Challenge | Find the easy pass |
| Rank | Easy |
| Time | 45min |
| Category | Reverse Engineering |
Quick solve
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
# download the required zip file
ls
'Find The Easy Pass.zip'
# unzip the file with the given password
unzip Find\ The\ Easy\ Pass.zip
Archive: Find The Easy Pass.zip
[Find The Easy Pass.zip] EasyPass.exe password:
inflating: EasyPass.exe
ls
EasyPass.exe 'Find The Easy Pass.zip'
# check file type
file EasyPass.exe
EasyPass.exe: PE32 executable (GUI) Intel 80386, for MS Windows, 8 sections
# create a hex dump and write it to a file
xxd EasyPass.exe > bin_code
# read file with sublime
subl bin_code
Search for “password” in Sublime.
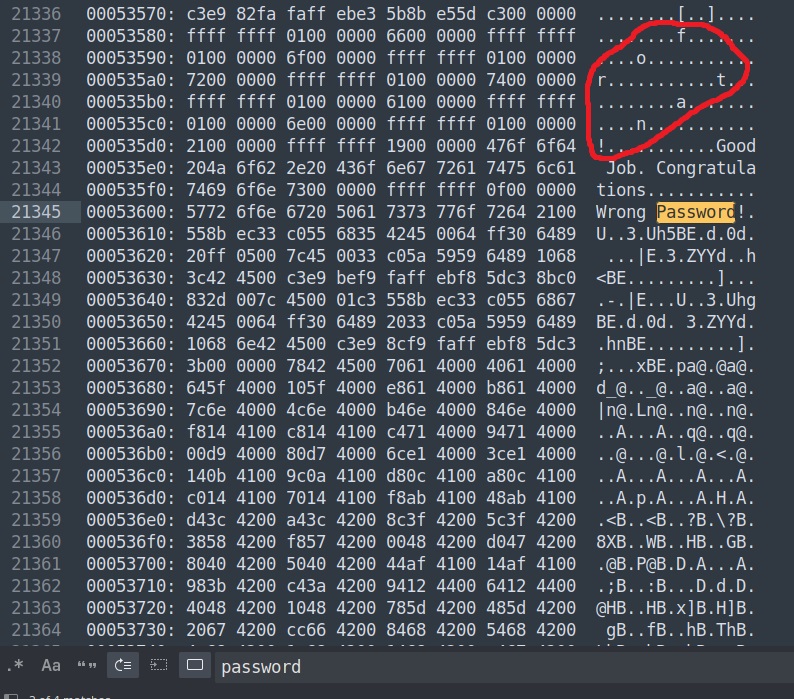
Since ‘fortan!’ gave ‘Wrong Password!’, I tried ‘fortran!’ which is a general-purpose programming language and it worked!
Proper solution
Taken from haxez.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
# check file permissions
ls -l
total 2280
-rw-r--r-- 1 kali kali 402432 Jul 3 2017 EasyPass.exe
-rwxrwxrwx 1 kali kali 210291 Nov 28 14:02 'Find The Easy Pass.zip'
# give execute permissions to .exe
sudo chmod +x EasyPass.exe
# check again to confirm that .exe has execute permissions
ls -l
total 2280
-rwxr-xr-x 1 kali kali 402432 Jul 3 2017 EasyPass.exe
-rwxrwxrwx 1 kali kali 210291 Nov 28 14:02 'Find The Easy Pass.zip'
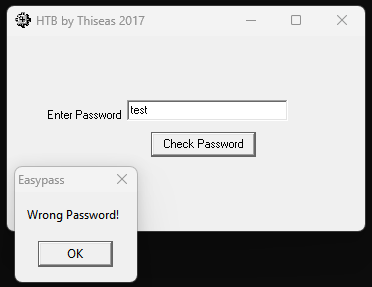
# run the program
./EasyPass.exe
1
2
# launch ghidra
ghidra
Ghidra is a reverse engineering tool, aka a disassembly tool, that was developed by the NSA and released in 2019 (Ghidra quickstart & tutorial: Solving a simple crackme).
Search for the string ‘password’:
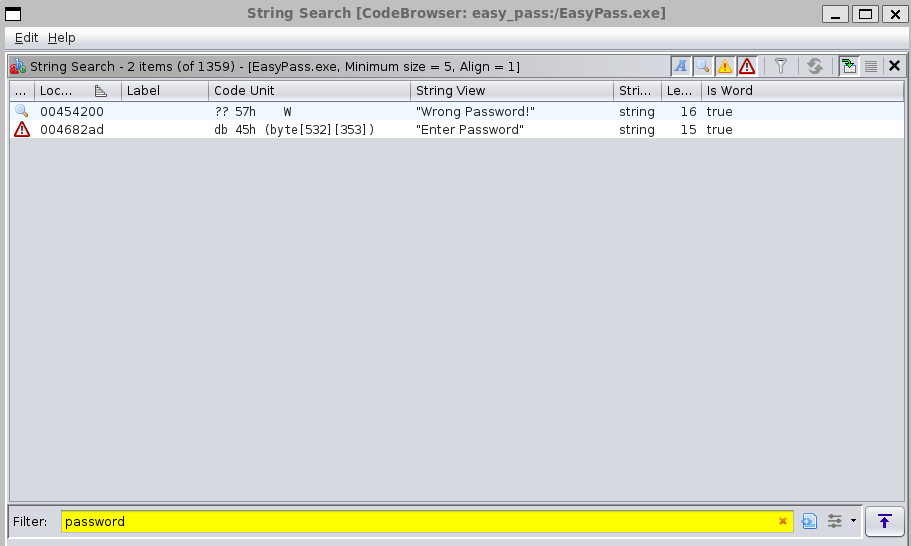
Click on ‘Wrong Password’ (memory reference: 00454200) and check References from main app:
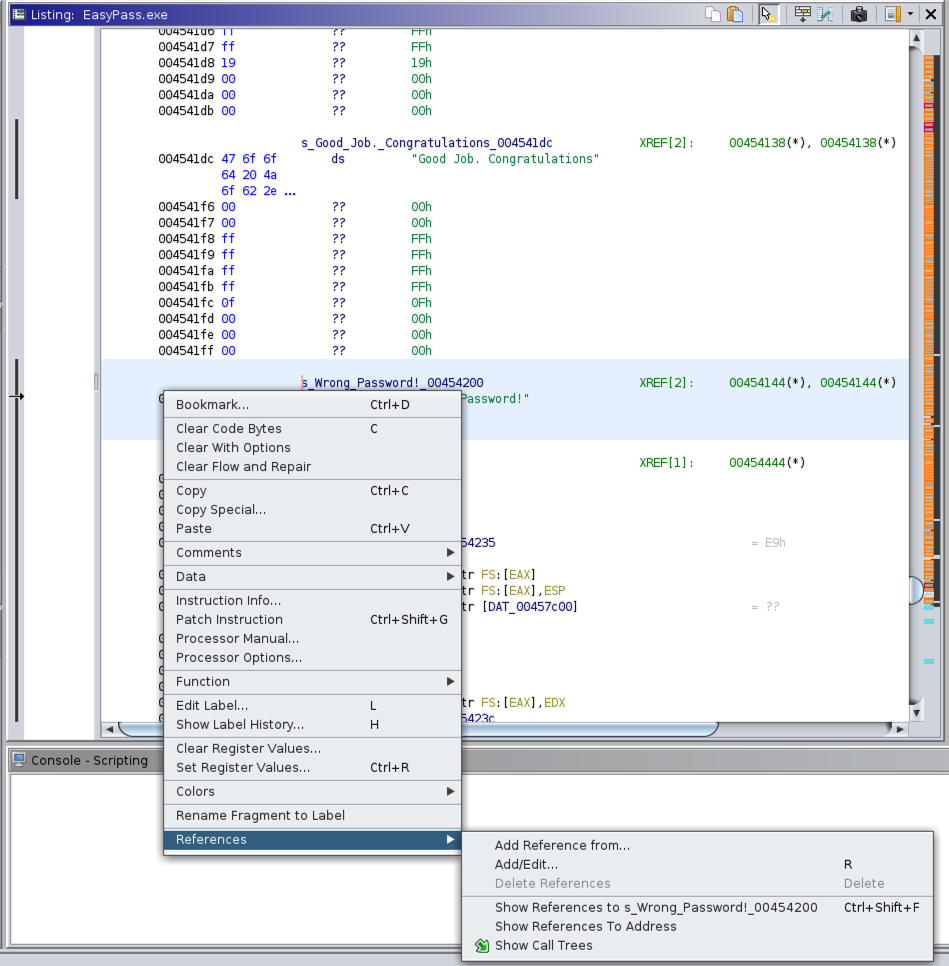
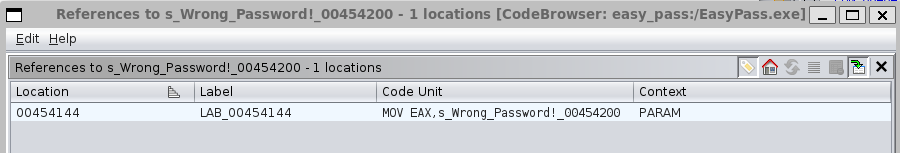
Repeat above step (memory ref: 00454144) and click on the Function Graph icon (top bar):
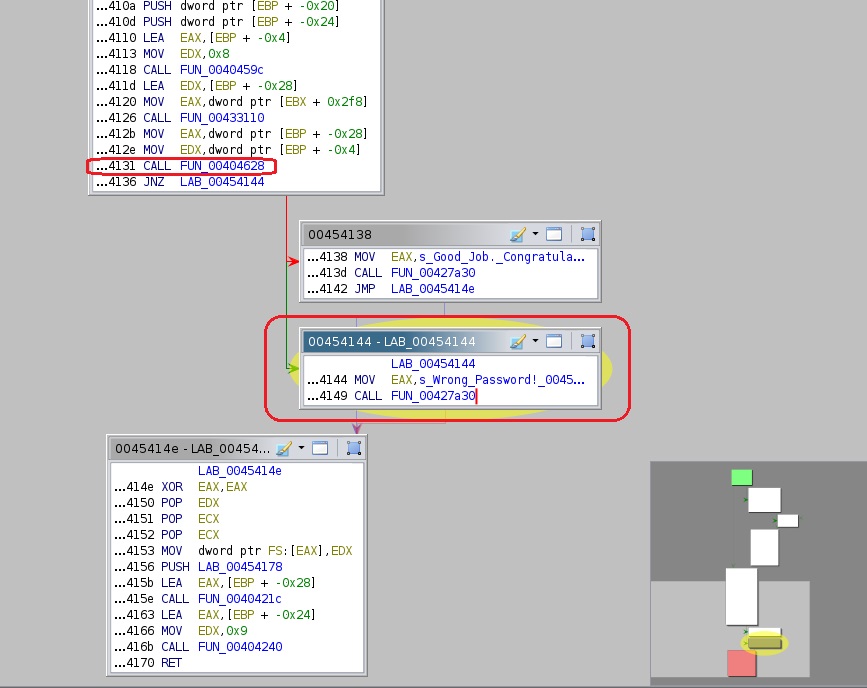
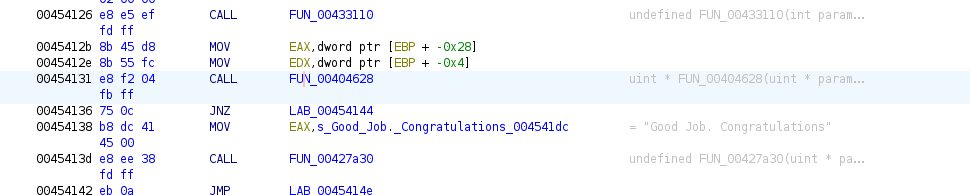
The above represents an if statement and the green arrow indicates that the function executed the second box (00454144). The last function call was FUN_00404628. Click on the function and check back on the main window (mem ref: 00454131):
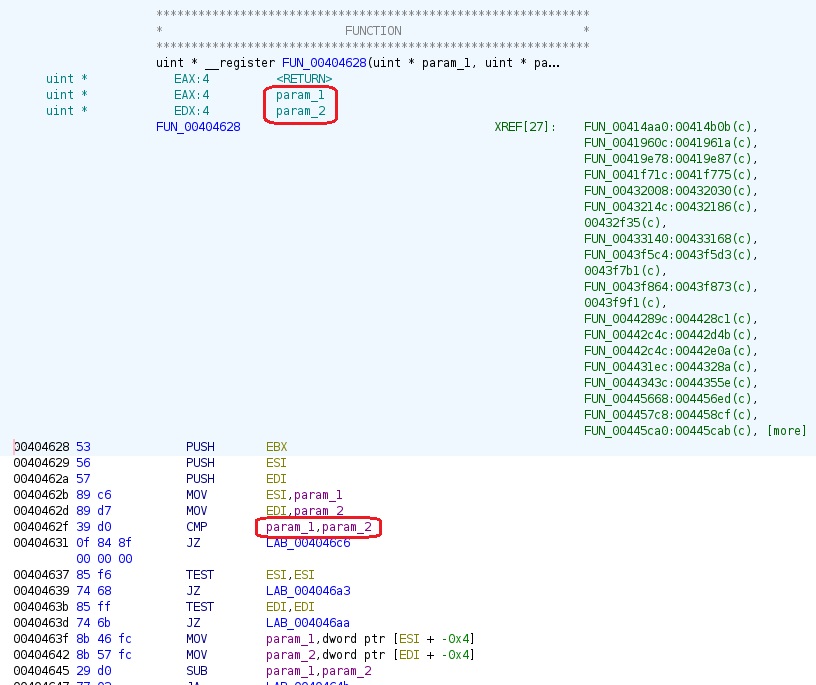
Double-click the function to reveal its logic. It takes 2 parameters, param_1 and param_2, and then compares them. So we can ‘safely’ assume that one of them would be the correct one:
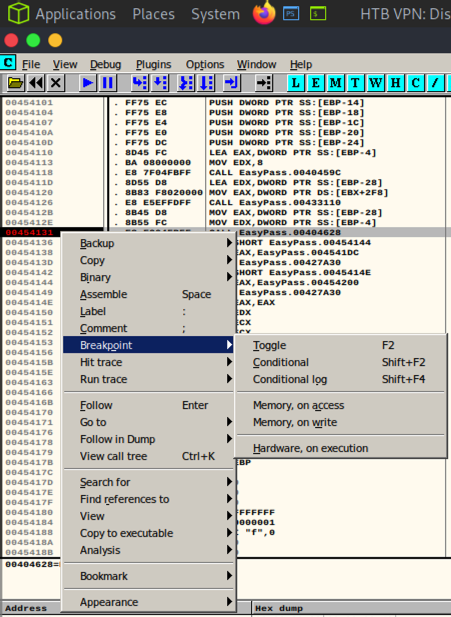
We need to find out what is stored inside these parameters. Open .exe with ollydgb, find function’s mem ref and toggle a breakpoint:
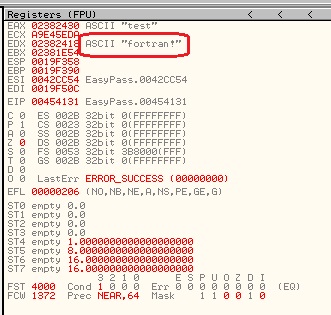
Now click the Play button on top and check the registers on the right-hand side: